This
DHL-themed phish got me looking at an IP address range of
64.20.51.16/29 which is a range belonging to
Interserver Inc in the US, but which has been reallocated to a customer. But who? Because the WHOIS details for that block are not valid..
%rwhois V-1.5:003fff:00 city.trouble-free.net (by Network Solutions, Inc. V-1.5.9.5)
network:Class-Name:network
network:ID:NETBLK-INTSRV.64.20.32.0/19
network:Auth-Area:64.20.32.0/19
network:Network-Name:INTSRV-64.20.51.16
network:IP-Network:64.20.51.16/29
network:Org-Name:N/A N/A
network:Street-Address:N/A
network:City:N/A
network:State:na
network:Postal-Code:N/A
network:Country-Code:US
network:Created:20150624
network:Updated:20150922
network:Updated-By:abuse@interserver.net
Well, that's quite a sloppy move by Interserver to allow that, but it doesn't mean that the block is evil. However, an analysis of the sites currently and formerly hosted in that range indicate a very high proportion of phishing sites.. in fact, the range is a hotbed of sophisticated fraud sites, many of which seem to be undiscovered.
I combined current reverse IP data from DomainTools and current and historical data from DNSDB and then ran them through an IP lookup and a check against the Google Safe Browsing and
SURBL reputations.
The results [csv] show a very large number of sites flagged by SURBL in particular, amounting to 47 out of 167 sites (i.e. 28%) that I can identify as being currently hosted in that range.
In addition, a large number of phishing and other malicious sites have been hosted on 64.20.51.16/29 in the past and are now hosted elsewhere.
nswo.co.uk / "La Casa Limpia - a Balaeric Island Villa"
At first glance, some of the remaining sites look legitimate. Consider
nswo.co.uk entitled "
La Casa Limpia - a Balaeric Island Villa".
It looks utterly legitmate, although it is an odd domain name for a villa in Spain. Let's check those WHOIS details..
Domain name:
nswo.co.uk
Registrant:
P J Green
Registrant type:
UK Sole Trader
Registrant's address:
100 Malderen Road
Islington
London
Greater London
LN23 6AU
United Kingdom
Data validation:
Nominet was able to match the registrant's name and address against a 3rd party data source on 10-Dec-2012
Despite Nominet claiming to verify the address, there is no such road as "Malderen Road" anywhere in the United Kingdom, and the post code of "LN23 6AU" is also completely invalid and exists nowhere in the UK. A bit of investigation shows that the site is almost a complete rip-off of a
legitimate site at
palmyramenorca.com.. but with different contact details.
dominioncollege.ca / "Dominion College"
Consider also
dominioncollege.ca - a professional looking website billing itself as
Dominion College of Canada.
Apparently, Dominion College is the "Highest Ranking Creative Arts University". But there is
no such university in Canada, and the domain for this "150 year old" institution was only registered in August 2015.
Domain name: dominioncollege.ca
Domain status: registered
Creation date: 2015/08/14
Expiry date: 2016/08/14
Updated date: 2015/08/19
DNSSEC: Unsigned
Registrar:
Name: PublicDomainRegistry.com Inc
Number: 3059041
The "About Us" page gives another clue.
That is actually
Old Dominion University in Virginia, United States. A completely different and wholly legitimate institution.
hkbbr.org / "Hong Kong Business Bureau Registry"
Consider
hkbbr.org billing itself as the
Hong Kong Business Bureau Registry..
Yet a
Google search for that term only returns hardly anything except content from the site itself, indicating that there is no such organisation.
The domain was registered in 2013 to an anonymous registrant. What is the point of
this site? Well, it looks like it is a register of legitimate Hong Kong businesses. You can search for business in their online services page..
Well, it
looks like a search.. but in fact it just loads results from a page
www.hkbbr.org/entity/ which has an open directory.. so you can see that there actually only 43 companies in the database. One or more of which will be fake.
Presumably this forms part of a scam where the victim has to deal with a fake company, and the scammers use this web site to try to convince the victim that they are dealing with a
legitimate company.
tricountysalesmexia.com / "Tri County Sales Mexia"
Consider
tricountysalesmexia.com, entitled "
Tri County Sales Mexia's Premier Pre-Owned Late Model Luxury and Exotic Vehicle Dealer - Mexia | Texas"
We added up the value of the cars listed on this "Tri County Sales" site. There were 218 cars valued at around $13.2 million, or around $60,000 per car.
Their website shows plush offices..
Now, Tri County Sales is a real company and I suspect a reliable vendor of used vehicles. But in reality the company's premises look
like this:
Does it look like somewhere that stocks $13 million dollars worth of high-end exotic vehicles? Of course not. Let's take a look at one of the more notable cars on the website.
This is a pretty rare car. But look closely at the partial logo in the top left hand corner of the large photo..
It's the logo of
Southlake Motorcars, where the image was stolen from..
Several of the other vehicles also turn up on other sites. You can be assured that although Tri County Sales is a real company, this website does not belong to them and is a scam.
goldwestgroup.com / "Gold West Group"
Consider
goldwestgroup.com calling itself "
Gold West Group"..
It's a bit vague about where it has mines, but the facility pictured at the top is the
Obuasi Gold Mine in Ghana belonging exclusively to
AngloGold Ashanti and no-one else.
The site itself mentions a Chile address, and the WHOIS details are consistent.
Registrant Name: Manu DeSouza
Registrant Organization: Gold West Group
Registrant Street: Europa Oficinas
Registrant Street: Guardia Vieja 255
Registrant City: Providencia
Registrant State/Province: Santiago
Registrant Postal Code: 2103
Registrant Country: Chile
Registrant Phone: +56.22997704
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: webmaster@goldwestgroup.com
But AngloGold Ashanti have
no operations in Chile. This site is a scam.
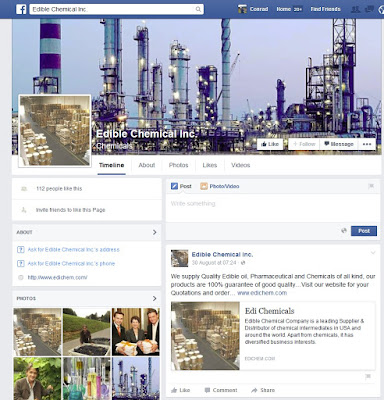
edichem.com / "Edible Chemical Inc"
Consider
edichem.com describing itself as "
Edible Chemical Inc"..
This site is riddle with spelling errors and has some comically bad photo manipulation.
The offices in the picture actually belong to a company called
APAG.
Let's have a look at that so-called CEO..
"Birningham University"? Quite a typo. And that photo is of a completely different person called
Peter Westenthaler.
This fake company has even gone to the effort of setting up a Facebook page at
www.facebook.com/edichem.biz:
cllinternational.com / "Courier Logistics Limited"
Consider
cllinternational.com calling itself "
Courier Logistics Limited":
In what way is
this logo meant to reflect "Courier Logistics Limited"?
It doesn't.. it belongs to the
IEEE Robotics and Automation Society.
The purpose of this site appears to be to generate fake courier tracking numbers, so a victim who has ordered a product will assume that it is actually on it's way. The tracking lookup seems to respond to a six-digit tracking code. The fake tracking site is on another IP,
185.24.233.16 in Ireland.
steadyprivateloan.com / "Steady Private Loan"
Most of the fake companies I have found so far have zero internet footprint. This fake finance company has at least attractive a
couple of complaints:
Edmond L.
Beware !!! Do not deal with TERRANCE CLARK / CLARK BRIAN of Goldmine Private Loan now with a new name "Steady Private Loan". These are scam artist.
8 months ago
Sharon Todd
I agree. We fell for their Goldmine Loan and now Steady Private Loan owe us $21,195 ...They look fantastic but do not fall for them. We are reporting them to the FBI
7 months ago
Unlike some of the other sites, this is a bit more amateurish and generic.
It claims to be based in Delaware.
The bottom line here is that there is no such corporation as "Steady Private Loan" in Delaware. This site is a scam.
madrewson.net / "Madrewson Consult"
Consider
madrewson.net calling itself "
Madrewson Consult". This bills itself as some sort of HR consultancy, but you can guarantee that everythig it touches is fake.
There are a bunch of testimonials on the "About Us" page.
These are all attractive, well-photographed people aren't they? And they pop up in so many places. The photo of "Helen Pyzowski" turns up in a
bunch of places. "Adam Smith" is a
stock image. "Kristin Malie" turns up in a
bunch of places. "John L. Skelley" turns up in a
bunch of places. The testimonials are fake, as is this so-called company.
mobgifts.net / "Coca Cola Promo"
"Coca Cola" themed prize scams are well known (and documented on the
Coca Cola corporate site) but I've never seen anyone go to the effort of creating a fake website to go with it.
There are several photos of people being handed cheques. But what is that cheque exactly?
This is someone winning a prize alright.. but for
developing a mobile app, not a lottery. All the other pictures of people getting cheques are similarly bogus. There is no such thing a the Coca Cola Promo free lottery.
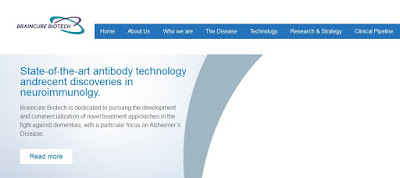
braincure-biotech.com / "Braincure Biotech"
Consider this so-called Taiwanese biochemistry firm, "
Braincure Biotech" (
braincure-biotech.com)
The site looks professional but very generic. But is it genuine? Unfortunately, the Taiwanese companies registry is in Chinese only and is quite difficult to use.
So let's just Google it.
There are virtually zero references to this "company" apart from its own website. And by the time you look, probably this blog. A quick check of the body text of the site reveals that it is copied from other genuine biotech sites. This company does not exist, but presumably is there as part of an investment or employment scam.
What else is there?
Trawling through the IP address range shows many fake blogs (set up to promote goodness only knows what), some Bitcoin and make-money-fast sites and a whole load of sites that appear to be suspended. I cannot confirm a single legitimate site in this range.
Who is behind this?
Although the IP address range is owned by
Interserver Inc it is allocated to a customer. However, Interserver seems to have displayed poor governance here because it not only has allocated the range to an anonymous registrant, but it has not acted on the extremely high concentration of fraudulent sites.
Looking at the range, I can see several nameservers..
ns3.boldhosts.com
64.20.51.18
ns4.boldhosts.com
64.20.51.19
ns2.paidhoster.com
64.20.51.20
ns1.ok2host.com
64.20.51.21
ns2.ok2host.com
64.20.51.22
ok2host.com has anonymous WHOIS details, but the other two are related:
BOLDHOSTS.COM
Registry Registrant ID:
Registrant Name: Abdul Razzaq
Registrant Organization: Boldhosts
Registrant Street: Street 18 Clifton Block 8
Registrant City: Karachi
Registrant State/Province: Sind(en)
Registrant Postal Code: 75500
Registrant Country: PK
Registrant Phone: +92.2135491130
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: info@boldhosts.com
PAIDHOSTER.COM
Registrant Name: Sajid Mahmood
Registrant Organization: GroomHost
Registrant Street: Progressive Center Shahrah e Faisal
Registrant City: Karachi
Registrant State/Province: Sind(en)
Registrant Postal Code: 75400
Registrant Country: PK
Registrant Phone: +92.215681734
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: info@boldhosts.com
Although paidhoster.com does not resolve, both
boldhosts.com and
ok2host.com do and are hosted on adjacent IPs of
76.73.85.141 and
76.73.85.142 respectively, indicating that they might be the same company. Groomhost.com is also mentioned in the WHOIS details above, and that is hosted on
76.73.85.140.
It turns out that there is another IP block of
76.73.85.136/29 hosting a variety of possibly white-label web hosts:
network:Auth-Area:76.73.0.0/17
network:Class-Name:network
network:OrgName:Naeem Nasir
network:OrgID;I:FDC-11211
network:Address:Street number 18 clifton block 8
network:City:Karachi
network:StateProv:Sindh
network:PostalCode:75500
network:Country:PK
network:NetRange:76.73.85.136 - 76.73.85.143
network:CIDR:76.73.85.136/29
network:NetName:FDC-11211-76.73.85.136
The WHOIS details for the IP range don't give a lot of data, but we can also find the same registrant details for the domain
sandhost.com:
Registry Registrant ID:
Registrant Name: Muhammad Naeem Nasir
Registrant Organization:
Registrant Street: Street 18 clifton block 8
Registrant City: Karachi
Registrant State/Province: Sindh
Registrant Postal Code: 75500
Registrant Country: Pakistan
Registrant Phone:
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: naeem.nasir@yahoo.com
The AA419 database
shows several hits for this email address going back to 2011, so it seems that whoever this Pakistani web host is, they have been tolerating this activity on their network for several years, even if they are just providing hosting services rather than perpetrating fraud.
Conclusion
I really just skimmed the surface with my analysis here, but it is clear that the
64.20.51.16/29 block is being used almost exclusively for fraud. Moreover, the fraud is extremely sophisticated involving things like fake business registries and couriers. It is also clear that the Pakistani web hosts apparently providing these services have been doing so for some time.
Recommended blocklist:
64.20.51.16/29
76.73.85.136/29
185.24.233.16