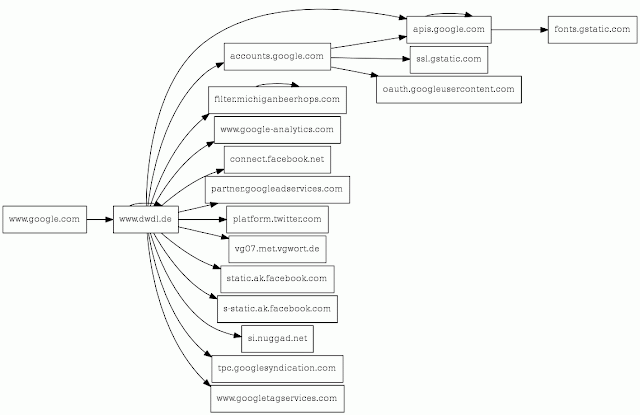
Popular German media website dwdl.de has been hacked and is serving up malware, according to this URLquery report.
URLquery's IDS function detects what looks like the RIG Exploit kit:
The exploit is in injected code pointing to a server at 94.142.140.222 (Marosnet Telecommunication Company, Russia) which in the example is using filter.michiganbeerhops.com which is a hijacked GoDaddy domain.
The exploit only appears to work if the site is accessed via a search engine, which looks like a classic .htaccess hack. URLquery's script relationship chart shows this in action:
VirusTotal gives an overview of other malicious domains on this server. It indicates that the following domains have been hijacked and malicious subdomains set up:
123goled.com
123gooled.com
123homeautomation.com
123oled.com
135warranty.com
1drones.com
4ktechsupport.com
audiovideoalternatives.com
audiovideoinsight.com
autonomouscontrolsystem.com
autonomouscontrolsystems.com
autonomousinterface.com
avioav.com
birminghamaudiovideo.com
birminghamtheatercompany.com
birminghamtheatersystems.com
cleanlittleengine.com
cleanpowercell.com
cleansunpower.com
clearviewelectronic.com
clearviewelectronic.net
clearviewelectronics.info
clearviewelectronics.me
clearviewelectronics.net
clearviewelectronics.org
crazyoled.com
daddybeer.com
devilscrotchhotsauce.com
dreamybikini.com
educationdrone.com
efgled.com
energeticled.com
ferndalebar.com
hometheaterlogistics.com
hopsmichigan.com
imagerled.com
inwallsoundbar.com
ledgest.com
ledimager.com
ledisme.com
ledrefill.com
ledrequired.com
ledstuf.com
lightsusingled.com
michiganbeerhops.com
timeandplacephotos.com
torredelpainelandscapes.com
travelersvisions.com
travelerviews.net
travelervisions.com
travelervisions.net
triadthinking.com
turkeylight.com
turkishlandscapes.com
tuscanycolor.com
understandinglight.com
urbanchina.info
veniciancolor.com
venicianlight.com
viewartsandsciences.com
viewevolution.com
viewevolution.net
viewevolution.org
viewhumanities.com
viewliberalarts.com
viewnaturalsciences.com
viewprocess.org
viewsocialsciences.com
visionandthought.com
visioningmind.com
visioningmind.net
visioningplace.com
visioningplace.net
visionofchina.net
visionofchina.org
visquest.info
visualcreativethinking.com
visualcreativethinking.net
visualcreativity.info
visualizationfuture.com
visualizationthinking.com
visualizingmaps.net
visualknowledge.org
visualmexico.net
vizmodeling.com
vizmodels.com
vizsee.com
vizthought.com
volgadeutsch.com
wallartbycountry.com
wayfindingadventure.com
wayfindingtravel.com
waysofthinking.com
waysofthinking.net
waystosee.net
webviews.info
westerneuropelandscapes.com
wilkiephotos.com
worldwallart.com
worldwallart.net
xianspirit.com
yunnanlandscapes.com
yunnanlight.com
zocaloscenes.com
Showing posts with label Hacked sites. Show all posts
Showing posts with label Hacked sites. Show all posts
Monday, 24 August 2015
Popular German wesite dwdl.de hacked, serving malware via 94.142.140.222
Labels:
Germany,
GoDaddy,
Hacked sites,
Russia
Thursday, 20 August 2015
Search the Ashley Madison hacked leaked database (enter name or email)
Search the Ashley Madison hacked leaked database (enter name or
email)
Nothing found
The profile_relationship column specifies the relationship status.
const ATTACHED_FEMALE_SEEKING_MALE = 1;
const ATTACHED_MALE_SEEKING_FEMALE = 2;
const SINGLE_MALE_SEEKING_FEMALE = 3;
const SINGLE_FEMALE_SEEKING_MALE = 4;
const MALE_SEEKING_MALE = 5;
const FEMALE_SEEKING_FEMALE = 6;
So, if it's a "2", it's a cheating man. The pref_opento items, which is a list of sexual fantasies users are open to:
1: "Threesome"
3: "Being Dominant/Master"
4: "Being Submissive/Slave"
6: "Bondage"
7: "Conventional Sex"
11: "Fetishes"
14: "Nothing Kinky"
15: "One-Night Stands"
17: "Role Playing"
18: "Sex Talk"
19: "Spanking"
21: "Experimenting with Tantric Sex"
22: "Transvestitism"
23: "Experimenting with Sex Toys"
23: "Exploring with Sex Toys"
26: "Aggressiveness"
27: "Blindfolding"
28: "Bubble Bath for 2"
29: "Cuddling & Hugging"
30: "Curious - Domination"
31: "Curious - Submission"
32: "Dressing Up/Lingerie"
33: "Erotic Movies"
34: "Erotic Tickling"
36: "Extended Foreplay/Teasing"
37: "Gentleness"
38: "Good With Your Hands"
39: "Kissing"
40: "Light Kinky Fun"
41: "Likes to be Watched/Exhibitionism"
42: "Likes to Give Oral Sex"
43: "Likes to Receive Oral Sex"
44: "Likes to Go Slow"
45: "Lots of Stamina"
46: "Open to Experimentation"
48: "Sensual Massage"
49: "Sharing Fantasies"
50: "Someone I Can Teach"
51: "Someone Who Can Teach Me"
52: "You Like to Cross Dress"
They also have a "looking for" section. Those numbers are:
1: "A Don Juan"
4: "Sense of Humor"
6: "Aggressive/Take Charge Nature"
9: "Average Sex Drive"
10: "Confidence"
11: "Discretion/Secrecy"
12: "Dislikes Routine"
14: "Good Personal Hygiene"
16: "Has a Secret Love Nest"
17: "High Sex Drive"
18: "Imagination"
19: "Likes Routine"
30: "A Professional/Well Groomed"
31: "Stylish/Classy"
32: "Casual Jeans/T-shirt Type"
33: "Tattoos"
34: "Body Piercing"
35: "BBW"
36: "Full Size Body"
37: "Muscular/Fit Body"
38: "Petite Figure"
39: "Slim to Average Body"
40: "Tall Height"
41: "Short Height"
42: "Long Hair"
43: "Short Hair"
44: "Girl Next Door"
45: "Naughty Girl"
46: "Bad Boy"
47: "Boy Next Door"
48: "Creative and Adventurous"
49: "Relaxed and Easy Going"
50: "Hopeless Romantic"
51: "A Father Figure"
52: "Not Possessive"
53: "A Good Listener"
54: "Good Communicator"
55: "Disease Free"
56: "Drug Free"
57: "Casual/Social Drinker"
58: "Seeking a Sugar Baby"
59: "Seeking a Sugar Daddy"
60: "Natural Breasts"
61: "Facial Hair"
62: "Tall, Dark and Handsome"
Nothing found
The profile_relationship column specifies the relationship status.
const ATTACHED_FEMALE_SEEKING_MALE = 1;
const ATTACHED_MALE_SEEKING_FEMALE = 2;
const SINGLE_MALE_SEEKING_FEMALE = 3;
const SINGLE_FEMALE_SEEKING_MALE = 4;
const MALE_SEEKING_MALE = 5;
const FEMALE_SEEKING_FEMALE = 6;
So, if it's a "2", it's a cheating man. The pref_opento items, which is a list of sexual fantasies users are open to:
1: "Threesome"
3: "Being Dominant/Master"
4: "Being Submissive/Slave"
6: "Bondage"
7: "Conventional Sex"
11: "Fetishes"
14: "Nothing Kinky"
15: "One-Night Stands"
17: "Role Playing"
18: "Sex Talk"
19: "Spanking"
21: "Experimenting with Tantric Sex"
22: "Transvestitism"
23: "Experimenting with Sex Toys"
23: "Exploring with Sex Toys"
26: "Aggressiveness"
27: "Blindfolding"
28: "Bubble Bath for 2"
29: "Cuddling & Hugging"
30: "Curious - Domination"
31: "Curious - Submission"
32: "Dressing Up/Lingerie"
33: "Erotic Movies"
34: "Erotic Tickling"
36: "Extended Foreplay/Teasing"
37: "Gentleness"
38: "Good With Your Hands"
39: "Kissing"
40: "Light Kinky Fun"
41: "Likes to be Watched/Exhibitionism"
42: "Likes to Give Oral Sex"
43: "Likes to Receive Oral Sex"
44: "Likes to Go Slow"
45: "Lots of Stamina"
46: "Open to Experimentation"
48: "Sensual Massage"
49: "Sharing Fantasies"
50: "Someone I Can Teach"
51: "Someone Who Can Teach Me"
52: "You Like to Cross Dress"
They also have a "looking for" section. Those numbers are:
1: "A Don Juan"
4: "Sense of Humor"
6: "Aggressive/Take Charge Nature"
9: "Average Sex Drive"
10: "Confidence"
11: "Discretion/Secrecy"
12: "Dislikes Routine"
14: "Good Personal Hygiene"
16: "Has a Secret Love Nest"
17: "High Sex Drive"
18: "Imagination"
19: "Likes Routine"
30: "A Professional/Well Groomed"
31: "Stylish/Classy"
32: "Casual Jeans/T-shirt Type"
33: "Tattoos"
34: "Body Piercing"
35: "BBW"
36: "Full Size Body"
37: "Muscular/Fit Body"
38: "Petite Figure"
39: "Slim to Average Body"
40: "Tall Height"
41: "Short Height"
42: "Long Hair"
43: "Short Hair"
44: "Girl Next Door"
45: "Naughty Girl"
46: "Bad Boy"
47: "Boy Next Door"
48: "Creative and Adventurous"
49: "Relaxed and Easy Going"
50: "Hopeless Romantic"
51: "A Father Figure"
52: "Not Possessive"
53: "A Good Listener"
54: "Good Communicator"
55: "Disease Free"
56: "Drug Free"
57: "Casual/Social Drinker"
58: "Seeking a Sugar Baby"
59: "Seeking a Sugar Daddy"
60: "Natural Breasts"
61: "Facial Hair"
62: "Tall, Dark and Handsome"
Labels:
Hacked sites,
Humour
Thursday, 12 June 2014
pcwelt.de hacked, serving EK on 91.121.51.237
The forum of popular German IT news site pcwelt.de has been hacked and is sending visitors to the Angler exploit kit.
Visitors to the forum are loading up a compromised script hxxp://www[.]pcwelt[.]de/forum/map/vbulletin_sitemap_forum_13.xml.js which contains some Base64 obfuscated malicious code (see Pastebin here) which uses a date-based DGA (domain generation algorithm) to direct visitors to a URL with the following format:
The .pw domain contains Base64 encoded data which points to the payload kit, in this case [donotclick]exburge-deinothe.type2consulting.net:2980/meuu5z7b3w.php (Pastebin) which is hosted on 91.121.51.237 (OVH, France). This appears to be the Angler EK.
It looks like the EK domains rotate regularly, but the following sites can be observed on this address:
ingetrekte.valueoptimizationfrontier.com
shellshellwillbomb.type2consulting.net
voorspannenzl.valueoptimizationfrontier.com
tourmenterai.afiduciaryfirst.com
kingyoku.typetwoconsulting.com
mittelbau.typetwoconsulting.com
yogeespith1.typetwoconsulting.com
rozrzewnienie.typetwoconsulting.com
geschaeftlichen.typetwoconsulting.com
kyhtyy-pimprinum.typetwoconsulting.com
jezuietendriesthe.typetwoconsulting.com
depolitsuperconfusion.typetwoconsulting.com
degivreraitdeorganization.typetwoconsulting.com
sknktekonzile-streelsters.typetwoconsulting.com
shogunalbeschenktet.viverebenealcaldo.com
subigi.valueoptimizationfrontier.com
totalize.valueoptimizationfrontier.com
puyaljoukou.valueoptimizationfrontier.com
weisungsgemaess.valueoptimizationfrontier.com
kezune-palpitera.valueoptimizationfrontier.com
remorquervltimme.valueoptimizationfrontier.com
clackdisfundamellemting.valueoptimizationfrontier.com
doscall.type2consulting.net
pehmoilla.type2consulting.net
moariesubigissem.type2consulting.net
unvigilant-straucht.type2consulting.net
mycetozoanreassesses.type2consulting.net
It is worth noting that these domains appear to have been hijacked from a GoDaddy customer:
type2consulting.net
valueoptimizationfrontier.com
typetwoconsulting.com
afiduciaryfirst.com
The following .pw sites are live right now, hiding behind Cloudflare:
7411447a.pw
31674ec.pw
e4ae59eb.pw
95bded0e.pw
Recommended blocklist:
91.121.51.237
type2consulting.net
valueoptimizationfrontier.com
typetwoconsulting.com
afiduciaryfirst.com
7411447a.pw
31674ec.pw
e4ae59eb.pw
95bded0e.pw
(and if you can block all .pw domains then it is probably worth doing that too)
Thanks to the #MalwareMustDie crew and Steven Burn for help with this analysis.
Visitors to the forum are loading up a compromised script hxxp://www[.]pcwelt[.]de/forum/map/vbulletin_sitemap_forum_13.xml.js which contains some Base64 obfuscated malicious code (see Pastebin here) which uses a date-based DGA (domain generation algorithm) to direct visitors to a URL with the following format:
[7-or-8-digit-hex-string].pw/nbe.html?0.[random-number]
The .pw domain contains Base64 encoded data which points to the payload kit, in this case [donotclick]exburge-deinothe.type2consulting.net:2980/meuu5z7b3w.php (Pastebin) which is hosted on 91.121.51.237 (OVH, France). This appears to be the Angler EK.
It looks like the EK domains rotate regularly, but the following sites can be observed on this address:
ingetrekte.valueoptimizationfrontier.com
shellshellwillbomb.type2consulting.net
voorspannenzl.valueoptimizationfrontier.com
tourmenterai.afiduciaryfirst.com
kingyoku.typetwoconsulting.com
mittelbau.typetwoconsulting.com
yogeespith1.typetwoconsulting.com
rozrzewnienie.typetwoconsulting.com
geschaeftlichen.typetwoconsulting.com
kyhtyy-pimprinum.typetwoconsulting.com
jezuietendriesthe.typetwoconsulting.com
depolitsuperconfusion.typetwoconsulting.com
degivreraitdeorganization.typetwoconsulting.com
sknktekonzile-streelsters.typetwoconsulting.com
shogunalbeschenktet.viverebenealcaldo.com
subigi.valueoptimizationfrontier.com
totalize.valueoptimizationfrontier.com
puyaljoukou.valueoptimizationfrontier.com
weisungsgemaess.valueoptimizationfrontier.com
kezune-palpitera.valueoptimizationfrontier.com
remorquervltimme.valueoptimizationfrontier.com
clackdisfundamellemting.valueoptimizationfrontier.com
doscall.type2consulting.net
pehmoilla.type2consulting.net
moariesubigissem.type2consulting.net
unvigilant-straucht.type2consulting.net
mycetozoanreassesses.type2consulting.net
It is worth noting that these domains appear to have been hijacked from a GoDaddy customer:
type2consulting.net
valueoptimizationfrontier.com
typetwoconsulting.com
afiduciaryfirst.com
The following .pw sites are live right now, hiding behind Cloudflare:
7411447a.pw
31674ec.pw
e4ae59eb.pw
95bded0e.pw
Recommended blocklist:
91.121.51.237
type2consulting.net
valueoptimizationfrontier.com
typetwoconsulting.com
afiduciaryfirst.com
7411447a.pw
31674ec.pw
e4ae59eb.pw
95bded0e.pw
(and if you can block all .pw domains then it is probably worth doing that too)
Thanks to the #MalwareMustDie crew and Steven Burn for help with this analysis.
Labels:
Angler EK,
France,
Germany,
Hacked sites,
Injection Attacks,
OVH
Tuesday, 29 October 2013
Suspect network: 69.26.171.176/28
69.26.171.176/28 is a small network range is suballocated from Xeex to the following person or company which appears to have been compromised.
%rwhois V-1.5:0000a0:00 rwhois.xeex.com (by Network Connection Canada. V-1.0)
network:auth-area:69.26.160.0/19
network:network-name:69.26.171.176
network:ip-network:69.26.171.176/28
network:org-name:MJB Capital, Inc.
network:street-address:8275 South Eastern Avenue
network:city:Las Vegas
network:state:NV
network:postal-code:89123
network:country-code:US
network:tech-contact:Mark Bunnell
network:updated:2013-05-30 10:01:58
network:updated-by:noc@xeex.com
network:class-name:network
There are three very recent Malwr reports involving sites in this range:
69.26.171.179 - bookmarkingbeast.com
69.26.171.181 - allisontravels.com
69.26.171.182 - robotvacuumhut.com
As a precaution, I would recommend temporarily blocking the whole range. These other sites are also hosted in the same block, and if you are seeing unusual traffic going to them then I would suspect that it is a malware infection:
bookmarkingbeast.com
antonseo.com
allisontravels.com
robotvacuumhut.com
glenburnlaw.com
timinteriorsystems.com
bulkbacklinks.com
prblogcomments.com
highprlinks.com
facebookadsppc.com
%rwhois V-1.5:0000a0:00 rwhois.xeex.com (by Network Connection Canada. V-1.0)
network:auth-area:69.26.160.0/19
network:network-name:69.26.171.176
network:ip-network:69.26.171.176/28
network:org-name:MJB Capital, Inc.
network:street-address:8275 South Eastern Avenue
network:city:Las Vegas
network:state:NV
network:postal-code:89123
network:country-code:US
network:tech-contact:Mark Bunnell
network:updated:2013-05-30 10:01:58
network:updated-by:noc@xeex.com
network:class-name:network
There are three very recent Malwr reports involving sites in this range:
69.26.171.179 - bookmarkingbeast.com
69.26.171.181 - allisontravels.com
69.26.171.182 - robotvacuumhut.com
As a precaution, I would recommend temporarily blocking the whole range. These other sites are also hosted in the same block, and if you are seeing unusual traffic going to them then I would suspect that it is a malware infection:
bookmarkingbeast.com
antonseo.com
allisontravels.com
robotvacuumhut.com
glenburnlaw.com
timinteriorsystems.com
bulkbacklinks.com
prblogcomments.com
highprlinks.com
facebookadsppc.com
Labels:
Hacked sites,
Malware,
Viruses,
Xeex
Thursday, 18 July 2013
primrose.co.uk hacked, email addresses compromised
Garden accessory primrose.co.uk has been hacked, and email addresses stored in their system are being abused for phishing purposes:
The attached form Account Information-Paypal.html is basically a phishing page, pulling content from www.thesenddirect.com (62.149.142.113 - Aruba, Italy) and submitting the data to www.paypserv.com (62.149.142.152 - also Aruba). The WHOIS details are no doubt fake are are respectively:
Saunders, John Alan mahibarayanlol@gmail.com
4 The Laurels off Oatland Close Botley, 4
Southampton, GB SO322EN
IT
+39.447885623455
----------
Clarke, Victoria johanjo1010@gmail.com
Innex Cottage Ropers Lane, 754
Wrington, GB BS405NH
IT
+39.441934862064
Primrose.co.uk were informed of the breach on 4th July and told me that IT were investigating, but as I haven't heard anything back and customers haven't been notified then I will assume they did not find anything.
Of note is that the spam email does not address customers by name, so it is possibly only email addresses that have been leaked. Also, passwords do not appear to be kept in plaintext which is good. Without further information from primrose.co.uk it is impossible to say if any financial data has been compromised.
From: paypal.co.uk [service@paypal.co.uk]
Date: 18 July 2013 11:01
Subject: We cannot process your payment at this time.
Dear,
We need your help resolving an issue with your account.To give us time to work together on this, we've temporarily limited what you can do with your account until the issue is resolved.
we understand it may be frustrating not to have full access to your PayPal account.We want to work with you to get your account back to normal as quickly as possible.
What's the problem ?
It's been a little while since you used your account.For reasons relating to the safe use of the PayPal service we need some more information about your account.
Reference Number: PP-001-278-254-803
It's usually quite straight forward to take care of these things.Most of the time, we just need some more information about your account or latest transactions.
1.
Download the attached document and open it in a browser window secure.
2.
Confirm that you are the account holder and follow the instructions.
Yours sincerely,
PayPal
Copyright 2013 PayPal. All rights reserved PayPal Email ID PP1589
The attached form Account Information-Paypal.html is basically a phishing page, pulling content from www.thesenddirect.com (62.149.142.113 - Aruba, Italy) and submitting the data to www.paypserv.com (62.149.142.152 - also Aruba). The WHOIS details are no doubt fake are are respectively:
Saunders, John Alan mahibarayanlol@gmail.com
4 The Laurels off Oatland Close Botley, 4
Southampton, GB SO322EN
IT
+39.447885623455
----------
Clarke, Victoria johanjo1010@gmail.com
Innex Cottage Ropers Lane, 754
Wrington, GB BS405NH
IT
+39.441934862064
Primrose.co.uk were informed of the breach on 4th July and told me that IT were investigating, but as I haven't heard anything back and customers haven't been notified then I will assume they did not find anything.
Of note is that the spam email does not address customers by name, so it is possibly only email addresses that have been leaked. Also, passwords do not appear to be kept in plaintext which is good. Without further information from primrose.co.uk it is impossible to say if any financial data has been compromised.
Labels:
Hacked sites
Subscribe to:
Comments (Atom)