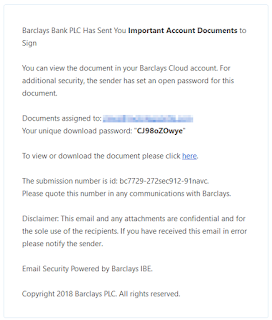
Nigerian registrants. Dodgy Eastern European host offering bulletproof and anonymous hosting. Yup, I very much doubt there is anything legitimate at all hosted on 188.241.58.60.. or indeed any part of Qhoster's network.
237buzz.com
255page.ga
702mine.com
779999977.com
a1cargomovers.com
abtprinting.com
adassco.com
admincamac.co.uk
afazendaideal.ml
afflluenceindia.com
africheck.com
alamiranut.com
alexandrahospitals.com
alliarnce.org.uk
allseaship.com
amba-medias.com
amiicogroup.com
andrzejkupnopark.eu
anook.info
ansaexpress.com
antrackdiplomaticcs.com
apidexconstruction.com
aramexbe.com
arshland.com
artyschat.com
atlanticfforum.com
aughana.com
battlegrounds-arena.com
baugeruest-handel.com
bevadgmbh.com
billdiamondfinance.co.uk
binaryoptionsmonitor.com
binco-sale.com
bit-masters.com
bitcoincashold.com
bitcoinsdrugsrehab.com
bitmain-alliances.com
bitmamashop.com
blecoman.com
bmpro.info
bourseafrique.com
britannia-pharmaceutical.co.uk
btccap.biz
btctriplermachine.com
buycounterfeitmoneys.com
calvinscott.biz
cameroonianbeauties.com
candodvillahotel.com
carphonewarehouse-eu.com
centroculturadigital.com
certificatesshop.com
chainconnect.co
chaseoffshoreonline.tk
chondomonitor.com
citydiaryfarms.com
classicdeliverycourier.com
clickhereforgiveaway.site
clickhereforgiveaway.xyz
cloud-bigfile.com
cncoslight-zh.com
cnximgang.com
coca-colafinancedept.com
coflaxfluidhandling.com
coinminners.com
coinrxstore.com
compasseguip.com
confirmedsoft.us
cosm0-hk.com
cosmosport24.com
creditonfcu.com
crewlinked.com
criagent.com
crypto023.com
cryptominingtechnology.com
cryptoshifters.com
cs-oilfeild.com
cureonlinepharmacy.org
denverlaserhairremoval.co
divecastle.com
dlnamicatrade.com
double-bitcoins-legit.com
eastmanimpex.cam
ebid-tg.com
efceosaudi.com
elitecertifiedhack.com
emailtime.info
ethiopianairilines.com
eurocertificationcentre.eu
fabftifun.com
faircloths.co.uk
fastcoine.com
fastestfingersfirst.com
fidelity-investment.co.uk
findingthepropercode.com
firstsuorceinc.com
forvisitingthankyou.com
fotesale.com
front-dashboard.com
gdp-international.com
general-funds.com
generate-dcash.biz
gettinginonthelow.com
global-news.center
globalinkscobsult.com
globalinksconsult.com
gmb-trade.com
goimsa.info
grand-sale.com
grantersmultiservices.com
greetapex.com
guaranteecds.com
hackers-list.com.de
harpack-ulma.com
heraeu.com
hereweareonit.com
hlroyoung.com
horizonpartnerrsltd.com
houseofspells.com
hsbrands-int.ml
humer1adminka.com
hyip.co.in
hyipcave.com
idexpresscargo.com
inlinefornine.com
interseadrill.com
item-desc.com
jdfrencis.com
jonihoppershowcase.com
kcf-th.com
kececiprofile.com
kencanafishing.com
kiingsay.com
kindres.com
kindres.de
kippaskagit.com
kmsinfoservice.com
ks-prod.com
lane-pres.com
legitrxonline.club
lifegoalsdevelopmentschool.com
litbitcoinembassy.com
littlerockbitcoins.com
live-rx-store.com
loactrippleser.ga
loan-assistance.com
loan-dealer.com
loudiclear.com
lurnentum.com
luwiex.com
manarpso.com
mannhiem.in
maomanlodocs.cf
marshawoifesquire.com
mcmg-tech.com
meetcameroonians.com
meetup4real.com
megachemstoreonline.com
miamibeachcoin.com
microclicker.com
mile22-casting.com
miningcrux.com
mission4christministry.com
movimientorevolucionariodelpueblo.org
ms-fi.com
mst4sale.com
mysite111.com
neatwaytogettheninth.com
neusportltd.com
news-world.center
nexttys.com
nightcapdice.com
ninthinline.com
nlsteinweg.com
nomuta.com
noworri.com
obsgruop.com
offshoreseadrill.com
onehereisreservedforyou.com
online-citibankgroup.com
ontothenextgame.com
opcolage.com
orifiameglobal.com
ourskynet.com
oxfords-pay.com
parcelservicess.com
pharmas4plus.com
plccsolutions.com
psypharm.com
ptochart.com
quicktitletransfer.com
rashedal-wataniagroup.com
rawgarner.com
realbuyrx.com
recordspharm.com
researchchem4us.com
resumedatabase11.xyz
rnailb.com
rnarhaba.com
ro-noutati-mondene.ml
robnsaconsult.com
rock-sale.com
rosenbaumcontemporarygroup.com
royalstandard.ga
rumlt.in
rush-sale.com
seachiefs.com
seguradoravirtual.com
seosenior.com
service-infoo.com
she-afro.com
shippingdynamics.com
showbarghana.com
siglobal.org
simplyitaly.dk
simplyitaly.it
skillocademy.com
sms-red-online.ga
solid-sale.com
southchina-sea.net
srcoin.ca
srnec-cn.com
stacksign.ga
superenterprise.work
superwhiteningpills.org
svclnlk.com
tax-gov.com
tccholdng-th.com
tecebusiness.com
techfronst.com
thebinaryoptionmonitor.org
thecolumbiabanks.com
thefutureofkitchen.com
theninthisin.com
thewomoorsfestival.co.uk
thisistheninth.com
tienhongjs.com
timetorefillthestock.com
torromodel.de
trans-atlanticdrilling.com
trustedhackers.com
turkiyenews247.tk
turkiyenews27.tk
twhe48.online
uk-pharmcay.com
ulmaparkaging.com
ultronnews.com
unipharma.bz
urnalaxmi-organics.com
usr-acc-serv.com
vendadebitcoin.com
visteonogbonnagroup.com
vpox.ru
vwork.pw
walletsofcoolandhip.com
weather-livenews.com
webs-host.pro
xcesstel.com
xopen.cc
yahoomailservice.com
youngcompamies.com
yoyooo.xyz
zestcrypto.com