From: Barclays [service@barclaysdownloads.co.uk]
Date: 10 May 2018, 13:16
Subject: New documents available for download
Signed by: barclaysdownloads.co.uk
Security: Standard encryption (TLS) Learn more
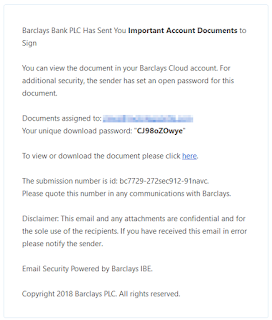
Barclays Bank PLC Has Sent You Important Account Documents to Sign
You can view the document in your Barclays Cloud account. For additional security, the sender has set an open password for this document.
Documents assigned to: jlines@[redacted]
Your unique download password: "CJ98oZOwye"
To view or download the document please click here.
The submission number is id: bc7729-272sec912-91navc.
Please quote this number in any communications with Barclays.
Disclaimer: This email and any attachments are confidential and for the sole use of the recipients. If you have received this email in error please notify the sender.
Email Security Powered by Barclays IBE.
Copyright 2018 Barclays PLC. All rights reserved.
The download password and submission number are the same in all cases I have seen. Clicking the link leads to a landing page at barclaysdownloads.com.
Entering the password downloads a document AccountDocuments.doc with a VirusTotal detection rate of 14/58, and Hybrid Analysis indicates that this uses an Equation Editor flaw to run a Powershell that downloads an additional component from:
http://basedow-bilder.de/kporto.bin
http://crimefiles.net/logo.bin
The .bin file is saved as %TEMP%\lovemete.exe and this currently has a detection rate of 15/65. Hybrid Analysis indicates this is Trickbot.
barclaysdownloads.co.uk and barclaysdownloads.com have both been registered for this purpose, the latter of which is hosted at Cloudflare.