Sometimes a spam comes through and it isn't immediately obvious what they are trying to do:
From: Brad Lorien [bclorien@ngcmp.com]
Date: 31 December 2014 at 01:12
Subject: Real estate (12/30/2014)
Our company reaches an online community of almost 41 million people,
who are mostly US and Canadian based. We have the ability to present
our nearly 41 million strong network with a best, first choice when
they are looking online for what your company does.
We are seeking a preferred choice to send our people who are looking
for real estate in Abilene and surrounding markets.
I’m in the office weekdays from 9:00 AM to 5:00 PM Pacific time.
Best regards,
Brad Lorien
Network Specialist, SPS EServices
Phone: (877) 489.2929, ext. 64
There is no link or attachment in the email. So presumably the spammer is soliciting replies to the email address
bclorien@ngcmp.com which is a valid address. The domain ngcmp.com uses a mail server
mail.ngcmp.com to receive email messages, hosted on
38.71.66.127 (PSInet / Virtual Empire, US). A look at the spam headers are rather revealing..
Received: from [38.71.66.126] (port=60856 helo=ngcmp.net)
by [redacted] with esmtp (Exim 4.80)
(envelope-from <bclorien@ngcmp.com>)
id 1Y67tI-0006Ub-TC
for [redacted]; Wed, 31 Dec 2014 01:16:17 +0000
Received: from mail.ngcmp.com (211.sub-75-215-49.myvzw.com [75.215.49.211])
by ngcmp.net (Postfix) with ESMTPA id 0812E3E34E
for <[redacted]>; Tue, 30 Dec 2014 19:18:13 -0600 (CST)
(envelope-from bclorien@ngcmp.com)
We can see that the spam was sent via a relay at
38.71.66.126 which is one IP different from the server handling incoming mail, which pretty much firmly identifies that whoever controls the ngcmp.com domain is actually sending the spam. The mail headers also identify the
originating IP as well as the relay, which is a Verizon Wireless customer at
75.215.49.211, possibly someone sending spam using throwaway cell phones to avoid being traced.
An examination of those two PSInet addresses shows the following domains are associated with them:
ncmp.co
ngmp.co
ngcmp.com
ng-portal.com
ngcmp.net
ng-central.net
luxebagscloset.com
reviewwordofmouth.com
All of these domains have anonymous WHOIS details, but you can see that there is a common pattern here. I don't recommend that you visit spam sites, but I did in this case to see what it was about.
It appears to be some crappy toolbar called
NetGuard and indeed the
ngcmp.com pulls down many resources from the
netguardtoolbar.com website. The site claims to be from a company called "
NG Systems" but gives no other identification. netguardtoolbar.com has also had anonymous WHOIS details since it was registered in 2008.
If we look at the "Privacy" page of the site, we can see what this is all about.
NetGuard does not ask you for any personally identifiable information such as an email address, phone number, your name, or any such data. We do track IP addresses only of those who choose to download our App. We also track downloads of the NetGuard App, as well as uninstalls of the NetGuard App, so that we may have accurate data on those two items only in dealing with our Advertisers. Our Advertisers assist us in maintaining our NetGuard App Community, which allows us to provide the public with even more features as time and innovation allows. NetGuard does, as part of our advertising process, allow Advertisers who maintain an active Advertiser Account, to present their websites when an end user of the NetGuard does a search on any of the major search engines. This in no way changes the search results contained on the native pages of the major search engines, but does allow NetGuard to continue to present the general public with more options as time and innovation allows.
This is basically adware. Going back to the original spam message, these "41 million people" are presumably suckers who have downloaded this crap, and NG Systems are busy spamming out to find more low-life advertisers to fill up their network. Or am I just sounding annoyed?
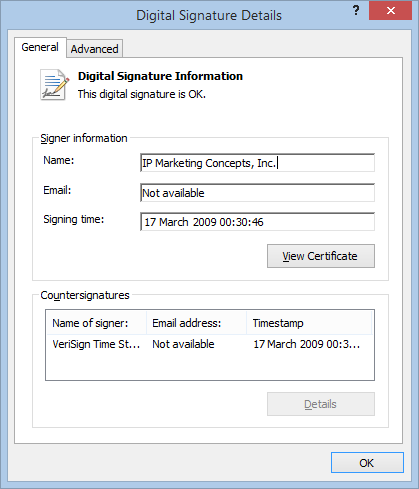
Predictably, there seems to be no such corporation as "NG Systems", but if you download the Toolbar it turns out it is digitally signed by a company called "
IP Marketing Concepts, Inc."
If we drill down into the certificate details we can find out more about this mystery corporation.
CN = IP Marketing Concepts, Inc.
OU = SECURE APPLICATION DEVELOPMENT
O = IP Marketing Concepts, Inc.
L = Lewes
S = Delaware
C = US
Some Googling around finds a Delware corporation number
4099908 founded in 2006, but as Delware is a "go to" place for corporation trying to hide their identities, it is hard to find out more information without paying.
The executable itself is tagged by
only one AV engine as malicious, but VirusTotal does note that it looks like a PUA. Malwr notes that
individual components appear to be Russian in origin.
So all in all, this spam is being sent out by a company that goes a very, very long way to disguise its origins. Would you really want to either install their product or advertise on their network?