From "Santanderbillpayment-noreply@SantanderBillPayment.co.uk" [Santanderbillpayment-noreply@SantanderBillPayment.co.uk]The attachment is named SantanderBillPayment_Slip0343884.zip although I have not been able to get a working copy. The payload is most likely the Upatre/Dyre banking trojan. My sources tell me that the current wave of this is phoning home to 197.149.90.166 in Nigeria which is worth blocking or monitoring.
Date Tue, 29 Sep 2015 12:33:56 GMT
Subject Info from SantanderBillpayment.co.uk
Thank you for using BillPay. Please keep this email for your records.
The following transaction was received on 29 September 2015 at 09:11:36.
Payment type: VAT
Customer reference no: 0343884
Card type: Visa Debit
Amount: GBP 4,683.00
For more details please check attached payment slip.
Your transaction reference number for this payment is IR0343884.
Please quote this reference number in any future communication regarding this payment.
Yours sincerely,
Banking Operations
This message is intended for the named person above and may be confidential, privileged
or otherwise protected from disclosure. If it has reached you by mistake please contact
the sender on 0300 200 3601 and delete the message immediately.
**PLEASE DO NOT REPLY TO THIS E-MAIL, AS WE WILL NOT BE ABLE TO RESPOND**
Emails aren't always secure, and they may be intercepted or changed after they've
been sent. Santander doesn't accept liability if this happens. If you think someone
may have interfered with this email, please get in touch with the sender another
way.
This message doesn't create or change any contract. Santander doesn't accept responsibility
for damage caused by any viruses contained in this email or its attachments. Emails
may be monitored. If you've received this email by mistake, please let the sender
know at once that it's gone to the wrong person and then destroy it without copying,
using, or telling anyone about its contents.
Santander Corporate Banking is the brand name of Santander UK plc, Abbey National
Treasury Services plc (which also uses the brand name of Santander Global Banking
and Markets) and Santander Asset Finance plc, all (with the exception of Santander
Asset Finance plc) authorised and regulated by the Financial Services Authority,
except in respect of consumer credit products which are regulated by the Office of
Fair Trading. FSA registration numbers: 106054, 146003 and 423530 respectively.
Registered offices: 2 Triton Square, Regent's Place, London NW1 3AN and Carlton Park,
Narborough LE19 0AL. Company numbers: 2294747, 2338548 and 1533123 respectively.
Registered in England. Santander and the flame logo are registered trademarks.
Tuesday 29 September 2015
Malware spam "Info from SantanderBillpayment.co.uk" / "Santanderbillpayment-noreply@SantanderBillPayment.co.uk"
This fake financial spam comes with a malicious attachment:
Thursday 24 September 2015
Evil network: 64.20.51.16/29 (Interserver Inc and Muhammad Naeem Nasir)
This DHL-themed phish got me looking at an IP address range of 64.20.51.16/29 which is a range belonging to Interserver Inc in the US, but which has been reallocated to a customer. But who? Because the WHOIS details for that block are not valid..
I combined current reverse IP data from DomainTools and current and historical data from DNSDB and then ran them through an IP lookup and a check against the Google Safe Browsing and SURBL reputations. The results [csv] show a very large number of sites flagged by SURBL in particular, amounting to 47 out of 167 sites (i.e. 28%) that I can identify as being currently hosted in that range.
In addition, a large number of phishing and other malicious sites have been hosted on 64.20.51.16/29 in the past and are now hosted elsewhere.
At first glance, some of the remaining sites look legitimate. Consider nswo.co.uk entitled "La Casa Limpia - a Balaeric Island Villa".
It looks utterly legitmate, although it is an odd domain name for a villa in Spain. Let's check those WHOIS details..
Consider also dominioncollege.ca - a professional looking website billing itself as Dominion College of Canada.
Apparently, Dominion College is the "Highest Ranking Creative Arts University". But there is no such university in Canada, and the domain for this "150 year old" institution was only registered in August 2015.
That is actually Old Dominion University in Virginia, United States. A completely different and wholly legitimate institution.
Yet a Google search for that term only returns hardly anything except content from the site itself, indicating that there is no such organisation.
The domain was registered in 2013 to an anonymous registrant. What is the point of this site? Well, it looks like it is a register of legitimate Hong Kong businesses. You can search for business in their online services page..
Well, it looks like a search.. but in fact it just loads results from a page www.hkbbr.org/entity/ which has an open directory.. so you can see that there actually only 43 companies in the database. One or more of which will be fake.
Presumably this forms part of a scam where the victim has to deal with a fake company, and the scammers use this web site to try to convince the victim that they are dealing with a legitimate company.
Consider tricountysalesmexia.com, entitled "Tri County Sales Mexia's Premier Pre-Owned Late Model Luxury and Exotic Vehicle Dealer - Mexia | Texas"
We added up the value of the cars listed on this "Tri County Sales" site. There were 218 cars valued at around $13.2 million, or around $60,000 per car.
Their website shows plush offices..
Now, Tri County Sales is a real company and I suspect a reliable vendor of used vehicles. But in reality the company's premises look like this:
Does it look like somewhere that stocks $13 million dollars worth of high-end exotic vehicles? Of course not. Let's take a look at one of the more notable cars on the website.
This is a pretty rare car. But look closely at the partial logo in the top left hand corner of the large photo..
It's the logo of Southlake Motorcars, where the image was stolen from..
Several of the other vehicles also turn up on other sites. You can be assured that although Tri County Sales is a real company, this website does not belong to them and is a scam.
It's a bit vague about where it has mines, but the facility pictured at the top is the Obuasi Gold Mine in Ghana belonging exclusively to AngloGold Ashanti and no-one else.
The site itself mentions a Chile address, and the WHOIS details are consistent.
This site is riddle with spelling errors and has some comically bad photo manipulation.
The offices in the picture actually belong to a company called APAG.
Let's have a look at that so-called CEO..
"Birningham University"? Quite a typo. And that photo is of a completely different person called Peter Westenthaler.
This fake company has even gone to the effort of setting up a Facebook page at www.facebook.com/edichem.biz:
In what way is this logo meant to reflect "Courier Logistics Limited"?
It doesn't.. it belongs to the IEEE Robotics and Automation Society.
The purpose of this site appears to be to generate fake courier tracking numbers, so a victim who has ordered a product will assume that it is actually on it's way. The tracking lookup seems to respond to a six-digit tracking code. The fake tracking site is on another IP, 185.24.233.16 in Ireland.
Unlike some of the other sites, this is a bit more amateurish and generic.
It claims to be based in Delaware.
The bottom line here is that there is no such corporation as "Steady Private Loan" in Delaware. This site is a scam.
There are a bunch of testimonials on the "About Us" page.
These are all attractive, well-photographed people aren't they? And they pop up in so many places. The photo of "Helen Pyzowski" turns up in a bunch of places. "Adam Smith" is a stock image. "Kristin Malie" turns up in a bunch of places. "John L. Skelley" turns up in a bunch of places. The testimonials are fake, as is this so-called company.
There are several photos of people being handed cheques. But what is that cheque exactly?
This is someone winning a prize alright.. but for developing a mobile app, not a lottery. All the other pictures of people getting cheques are similarly bogus. There is no such thing a the Coca Cola Promo free lottery.
The site looks professional but very generic. But is it genuine? Unfortunately, the Taiwanese companies registry is in Chinese only and is quite difficult to use. So let's just Google it.
There are virtually zero references to this "company" apart from its own website. And by the time you look, probably this blog. A quick check of the body text of the site reveals that it is copied from other genuine biotech sites. This company does not exist, but presumably is there as part of an investment or employment scam.
Looking at the range, I can see several nameservers..
ns3.boldhosts.com
64.20.51.18
ns4.boldhosts.com
64.20.51.19
ns2.paidhoster.com
64.20.51.20
ns1.ok2host.com
64.20.51.21
ns2.ok2host.com
64.20.51.22
ok2host.com has anonymous WHOIS details, but the other two are related:
Although paidhoster.com does not resolve, both boldhosts.com and ok2host.com do and are hosted on adjacent IPs of 76.73.85.141 and 76.73.85.142 respectively, indicating that they might be the same company. Groomhost.com is also mentioned in the WHOIS details above, and that is hosted on 76.73.85.140.
It turns out that there is another IP block of 76.73.85.136/29 hosting a variety of possibly white-label web hosts:
The WHOIS details for the IP range don't give a lot of data, but we can also find the same registrant details for the domain sandhost.com:
Recommended blocklist:
64.20.51.16/29
76.73.85.136/29
185.24.233.16
%rwhois V-1.5:003fff:00 city.trouble-free.net (by Network Solutions, Inc. V-1.5.9.5)Well, that's quite a sloppy move by Interserver to allow that, but it doesn't mean that the block is evil. However, an analysis of the sites currently and formerly hosted in that range indicate a very high proportion of phishing sites.. in fact, the range is a hotbed of sophisticated fraud sites, many of which seem to be undiscovered.
network:Class-Name:network
network:ID:NETBLK-INTSRV.64.20.32.0/19
network:Auth-Area:64.20.32.0/19
network:Network-Name:INTSRV-64.20.51.16
network:IP-Network:64.20.51.16/29
network:Org-Name:N/A N/A
network:Street-Address:N/A
network:City:N/A
network:State:na
network:Postal-Code:N/A
network:Country-Code:US
network:Created:20150624
network:Updated:20150922
network:Updated-By:abuse@interserver.net
I combined current reverse IP data from DomainTools and current and historical data from DNSDB and then ran them through an IP lookup and a check against the Google Safe Browsing and SURBL reputations. The results [csv] show a very large number of sites flagged by SURBL in particular, amounting to 47 out of 167 sites (i.e. 28%) that I can identify as being currently hosted in that range.
In addition, a large number of phishing and other malicious sites have been hosted on 64.20.51.16/29 in the past and are now hosted elsewhere.
nswo.co.uk / "La Casa Limpia - a Balaeric Island Villa"
At first glance, some of the remaining sites look legitimate. Consider nswo.co.uk entitled "La Casa Limpia - a Balaeric Island Villa".
It looks utterly legitmate, although it is an odd domain name for a villa in Spain. Let's check those WHOIS details..
Domain name:Despite Nominet claiming to verify the address, there is no such road as "Malderen Road" anywhere in the United Kingdom, and the post code of "LN23 6AU" is also completely invalid and exists nowhere in the UK. A bit of investigation shows that the site is almost a complete rip-off of a legitimate site at palmyramenorca.com.. but with different contact details.
nswo.co.uk
Registrant:
P J Green
Registrant type:
UK Sole Trader
Registrant's address:
100 Malderen Road
Islington
London
Greater London
LN23 6AU
United Kingdom
Data validation:
Nominet was able to match the registrant's name and address against a 3rd party data source on 10-Dec-2012
dominioncollege.ca / "Dominion College"
Consider also dominioncollege.ca - a professional looking website billing itself as Dominion College of Canada.
Apparently, Dominion College is the "Highest Ranking Creative Arts University". But there is no such university in Canada, and the domain for this "150 year old" institution was only registered in August 2015.
Domain name: dominioncollege.caThe "About Us" page gives another clue.
Domain status: registered
Creation date: 2015/08/14
Expiry date: 2016/08/14
Updated date: 2015/08/19
DNSSEC: Unsigned
Registrar:
Name: PublicDomainRegistry.com Inc
Number: 3059041
That is actually Old Dominion University in Virginia, United States. A completely different and wholly legitimate institution.
hkbbr.org / "Hong Kong Business Bureau Registry"
Consider hkbbr.org billing itself as the Hong Kong Business Bureau Registry..Yet a Google search for that term only returns hardly anything except content from the site itself, indicating that there is no such organisation.
The domain was registered in 2013 to an anonymous registrant. What is the point of this site? Well, it looks like it is a register of legitimate Hong Kong businesses. You can search for business in their online services page..
Well, it looks like a search.. but in fact it just loads results from a page www.hkbbr.org/entity/ which has an open directory.. so you can see that there actually only 43 companies in the database. One or more of which will be fake.
Presumably this forms part of a scam where the victim has to deal with a fake company, and the scammers use this web site to try to convince the victim that they are dealing with a legitimate company.
tricountysalesmexia.com / "Tri County Sales Mexia"
Consider tricountysalesmexia.com, entitled "Tri County Sales Mexia's Premier Pre-Owned Late Model Luxury and Exotic Vehicle Dealer - Mexia | Texas"
We added up the value of the cars listed on this "Tri County Sales" site. There were 218 cars valued at around $13.2 million, or around $60,000 per car.
Their website shows plush offices..
Now, Tri County Sales is a real company and I suspect a reliable vendor of used vehicles. But in reality the company's premises look like this:
Does it look like somewhere that stocks $13 million dollars worth of high-end exotic vehicles? Of course not. Let's take a look at one of the more notable cars on the website.
This is a pretty rare car. But look closely at the partial logo in the top left hand corner of the large photo..
It's the logo of Southlake Motorcars, where the image was stolen from..
Several of the other vehicles also turn up on other sites. You can be assured that although Tri County Sales is a real company, this website does not belong to them and is a scam.
goldwestgroup.com / "Gold West Group"
Consider goldwestgroup.com calling itself "Gold West Group"..It's a bit vague about where it has mines, but the facility pictured at the top is the Obuasi Gold Mine in Ghana belonging exclusively to AngloGold Ashanti and no-one else.
The site itself mentions a Chile address, and the WHOIS details are consistent.
Registrant Name: Manu DeSouzaBut AngloGold Ashanti have no operations in Chile. This site is a scam.
Registrant Organization: Gold West Group
Registrant Street: Europa Oficinas
Registrant Street: Guardia Vieja 255
Registrant City: Providencia
Registrant State/Province: Santiago
Registrant Postal Code: 2103
Registrant Country: Chile
Registrant Phone: +56.22997704
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: webmaster@goldwestgroup.com
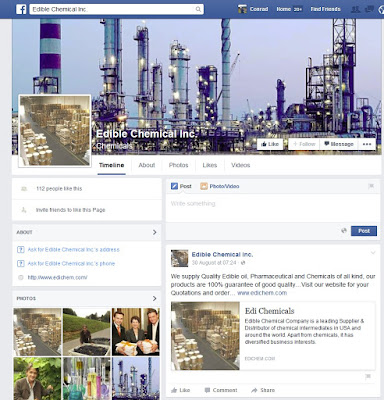
edichem.com / "Edible Chemical Inc"
Consider edichem.com describing itself as "Edible Chemical Inc"..This site is riddle with spelling errors and has some comically bad photo manipulation.
The offices in the picture actually belong to a company called APAG.
Let's have a look at that so-called CEO..
"Birningham University"? Quite a typo. And that photo is of a completely different person called Peter Westenthaler.
This fake company has even gone to the effort of setting up a Facebook page at www.facebook.com/edichem.biz:
cllinternational.com / "Courier Logistics Limited"
Consider cllinternational.com calling itself "Courier Logistics Limited":In what way is this logo meant to reflect "Courier Logistics Limited"?
It doesn't.. it belongs to the IEEE Robotics and Automation Society.
The purpose of this site appears to be to generate fake courier tracking numbers, so a victim who has ordered a product will assume that it is actually on it's way. The tracking lookup seems to respond to a six-digit tracking code. The fake tracking site is on another IP, 185.24.233.16 in Ireland.
steadyprivateloan.com / "Steady Private Loan"
Most of the fake companies I have found so far have zero internet footprint. This fake finance company has at least attractive a couple of complaints:Edmond L.
Beware !!! Do not deal with TERRANCE CLARK / CLARK BRIAN of Goldmine Private Loan now with a new name "Steady Private Loan". These are scam artist.
8 months ago
Sharon Todd
I agree. We fell for their Goldmine Loan and now Steady Private Loan owe us $21,195 ...They look fantastic but do not fall for them. We are reporting them to the FBI
7 months ago
Unlike some of the other sites, this is a bit more amateurish and generic.
It claims to be based in Delaware.
The bottom line here is that there is no such corporation as "Steady Private Loan" in Delaware. This site is a scam.
madrewson.net / "Madrewson Consult"
Consider madrewson.net calling itself "Madrewson Consult". This bills itself as some sort of HR consultancy, but you can guarantee that everythig it touches is fake.There are a bunch of testimonials on the "About Us" page.
These are all attractive, well-photographed people aren't they? And they pop up in so many places. The photo of "Helen Pyzowski" turns up in a bunch of places. "Adam Smith" is a stock image. "Kristin Malie" turns up in a bunch of places. "John L. Skelley" turns up in a bunch of places. The testimonials are fake, as is this so-called company.
mobgifts.net / "Coca Cola Promo"
"Coca Cola" themed prize scams are well known (and documented on the Coca Cola corporate site) but I've never seen anyone go to the effort of creating a fake website to go with it.
There are several photos of people being handed cheques. But what is that cheque exactly?
This is someone winning a prize alright.. but for developing a mobile app, not a lottery. All the other pictures of people getting cheques are similarly bogus. There is no such thing a the Coca Cola Promo free lottery.
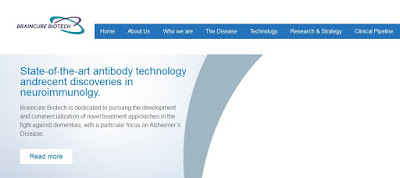
braincure-biotech.com / "Braincure Biotech"
Consider this so-called Taiwanese biochemistry firm, "Braincure Biotech" (braincure-biotech.com)The site looks professional but very generic. But is it genuine? Unfortunately, the Taiwanese companies registry is in Chinese only and is quite difficult to use. So let's just Google it.
There are virtually zero references to this "company" apart from its own website. And by the time you look, probably this blog. A quick check of the body text of the site reveals that it is copied from other genuine biotech sites. This company does not exist, but presumably is there as part of an investment or employment scam.
What else is there?
Trawling through the IP address range shows many fake blogs (set up to promote goodness only knows what), some Bitcoin and make-money-fast sites and a whole load of sites that appear to be suspended. I cannot confirm a single legitimate site in this range.Who is behind this?
Although the IP address range is owned by Interserver Inc it is allocated to a customer. However, Interserver seems to have displayed poor governance here because it not only has allocated the range to an anonymous registrant, but it has not acted on the extremely high concentration of fraudulent sites.Looking at the range, I can see several nameservers..
ns3.boldhosts.com
64.20.51.18
ns4.boldhosts.com
64.20.51.19
ns2.paidhoster.com
64.20.51.20
ns1.ok2host.com
64.20.51.21
ns2.ok2host.com
64.20.51.22
ok2host.com has anonymous WHOIS details, but the other two are related:
BOLDHOSTS.COM
Registry Registrant ID:
Registrant Name: Abdul Razzaq
Registrant Organization: Boldhosts
Registrant Street: Street 18 Clifton Block 8
Registrant City: Karachi
Registrant State/Province: Sind(en)
Registrant Postal Code: 75500
Registrant Country: PK
Registrant Phone: +92.2135491130
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: info@boldhosts.com
PAIDHOSTER.COM
Registrant Name: Sajid Mahmood
Registrant Organization: GroomHost
Registrant Street: Progressive Center Shahrah e Faisal
Registrant City: Karachi
Registrant State/Province: Sind(en)
Registrant Postal Code: 75400
Registrant Country: PK
Registrant Phone: +92.215681734
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: info@boldhosts.com
Although paidhoster.com does not resolve, both boldhosts.com and ok2host.com do and are hosted on adjacent IPs of 76.73.85.141 and 76.73.85.142 respectively, indicating that they might be the same company. Groomhost.com is also mentioned in the WHOIS details above, and that is hosted on 76.73.85.140.
It turns out that there is another IP block of 76.73.85.136/29 hosting a variety of possibly white-label web hosts:
network:Auth-Area:76.73.0.0/17
network:Class-Name:network
network:OrgName:Naeem Nasir
network:OrgID;I:FDC-11211
network:Address:Street number 18 clifton block 8
network:City:Karachi
network:StateProv:Sindh
network:PostalCode:75500
network:Country:PK
network:NetRange:76.73.85.136 - 76.73.85.143
network:CIDR:76.73.85.136/29
network:NetName:FDC-11211-76.73.85.136
The WHOIS details for the IP range don't give a lot of data, but we can also find the same registrant details for the domain sandhost.com:
Registry Registrant ID:The AA419 database shows several hits for this email address going back to 2011, so it seems that whoever this Pakistani web host is, they have been tolerating this activity on their network for several years, even if they are just providing hosting services rather than perpetrating fraud.
Registrant Name: Muhammad Naeem Nasir
Registrant Organization:
Registrant Street: Street 18 clifton block 8
Registrant City: Karachi
Registrant State/Province: Sindh
Registrant Postal Code: 75500
Registrant Country: Pakistan
Registrant Phone:
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: naeem.nasir@yahoo.com
Conclusion
I really just skimmed the surface with my analysis here, but it is clear that the 64.20.51.16/29 block is being used almost exclusively for fraud. Moreover, the fraud is extremely sophisticated involving things like fake business registries and couriers. It is also clear that the Pakistani web hosts apparently providing these services have been doing so for some time.Recommended blocklist:
64.20.51.16/29
76.73.85.136/29
185.24.233.16
Labels:
Evil Network,
Job Offer Scams,
Pakistan,
Phishing,
Scams
Wednesday 23 September 2015
Phish: "SHIPMENT LABEL" / "DHL Courier Services [roger@community.mile.org]"
This DHL-themed spam is actually a phishing email:
If the potential victim clicks "Click here" then they are directed to ow.ly/Sq9to and from there to a phishing page at br1-update.be/wg/lhd.php on 64.20.51.22 (Inetserver Inc, US) which belongs to a netblock 64.20.51.16/29 which also looks highly suspect.
The phishing page itself is a complex script which is Base 64 encoded, then hex encoded (Pastebin here) which is presumably phishing for email accounts. The spam itself appears to have been sent from a compromised webmail account at community.mile.org
For the moment, I would suggest that the entire 64.20.51.16/29 range is malicious and should be blocked.
From: DHL Courier Services [roger@community.mile.org]Attached is a PDF file shipmentt_label.pdf which is not malicious in itself, but contains a hypertext link (as you can see in this Hybrid Analysis report).
To:
Date: 23 September 2015 at 11:15
Subject: SHIPMENT LABEL
Signed by: community.mile.org
Dear customer,
Your shipment arrived at the post office.Our courier was unable to deliver the shipment to your address.To receive the shipment,please visit the nearestDHL office and take your mailing label with you.
The mailing label is attached in this email.Please print and show at the nearest DHL office to receive the shipment.
Thank you for using DHL services.
Princess Court 11
Wapping Ln,London,
E1W2DA,United Kingdom
Toll Free:+442075532200
Office Hours:9:00am-7:00pm
If the potential victim clicks "Click here" then they are directed to ow.ly/Sq9to and from there to a phishing page at br1-update.be/wg/lhd.php on 64.20.51.22 (Inetserver Inc, US) which belongs to a netblock 64.20.51.16/29 which also looks highly suspect.
The phishing page itself is a complex script which is Base 64 encoded, then hex encoded (Pastebin here) which is presumably phishing for email accounts. The spam itself appears to have been sent from a compromised webmail account at community.mile.org
For the moment, I would suggest that the entire 64.20.51.16/29 range is malicious and should be blocked.
Malware spam: "Bankline ROI - Password Re-activation Form" / "secure.message@rbs.co.uk"
This fake banking spam does not come from RBS, but is instead a simple forgery with a malicious attachment:
In the sample I saw, the attached file was Bankline_Password_reset_3537684.zip containing a malicious exeucutable Bankline_Password_reset_8569474.scr which has a VirusTotal detection rate of 2/56. The Hybrid Analysis report shows behaviour consistent with Upatre / Dyre and shows that the malware communicates with a known bad IP of 197.149.90.166 (Cobranet, Nigeria) which I definitely recommend blocking or monitoring.
From "RBS" [secure.message@rbs.co.uk]
Date Wed, 23 Sep 2015 11:28:48 GMT
Subject Bankline ROI - Password Re-activation Form
Please find the Re-activation form attached, send one per user ensuring only one
box is selected in section 3. A signatory on the bank mandate must sign the form.
Fax to 1850 826978 or alternatively you may wish to email the completed document,
by attaching it to an email and sendinsg it to banklineadministration@rbs.co.uk
On receipt of the completed form we will respond to the request within 2 working
hours and communicate this to the user by email.
<>
Please note - The life-span of an activation code is 21 days; after this time, the
activation code will expire and a new one must be ordered.
Please be aware when choosing a new pin and password for the service, it is important
not to use pin/passwords that you have used before but to use completely different
details.
If you are the sole Standard Administrator may I take this opportunity to suggest
when you are reinstated on the system, to set up another User in a Standard Administrator
role. This will prevent you being locked out completely and allow you to order a
new activation code from within the system and reset your security sooner.
If you require any further assistance then please do not hesitate to contact us on
1850 310269 and one of our associates will be happy to assist you.
Regards
Bankline Product Support
This e-mail message is confidential and for use by the intended recipient only. If
the message is received by anyone other than the intended recipient, please return
the message to the sender by replying to it and then delete the message from your
computer. Internet e-mails are not necessarily secure. Ulster Bank Limited and Ulster
Bank Ireland Limited (\"Bankline Bank Group\")/ Royal Bank of Scotland Group plc
does not accept responsibility for changes made to this message after it was sent.
Ulster Bank Group / Royal Bank of Scotland Group plc may monitor e-mails for business
and operational purposes. By replying to this message you give your consent to our
monitoring of your email communications with us. Whilst all reasonable care has been
taken to avoid the transmission of viruses, it is the responsibility of the recipient
to ensure that the onward transmission, opening or use of this message and any attachments
will not adversely affect its systems or data. No responsibility is accepted by any
member of Ulster Bank Group / Royal Bank of Scotland Group plc in this regard and
the recipient should carry out such virus and other checks as it considers appropriate.
In the sample I saw, the attached file was Bankline_Password_reset_3537684.zip containing a malicious exeucutable Bankline_Password_reset_8569474.scr which has a VirusTotal detection rate of 2/56. The Hybrid Analysis report shows behaviour consistent with Upatre / Dyre and shows that the malware communicates with a known bad IP of 197.149.90.166 (Cobranet, Nigeria) which I definitely recommend blocking or monitoring.
Tuesday 22 September 2015
(More) Domains and businesses associated with Michael Price of BizSummits
Following on from this post, here are some business and domains closely associated with Michael Price of BizSummits, presented without comment for research purposes only.
COO Summit
cooleaders.org
Hiring Spring
hiringspring.com
Exit Partners LLC
exitpartners.net
Exact Leads
exactleads.com
VisitorLeads
visitorleads.com
ListK
listk.com
LoudJob
loudjob.com
Franchisee Funnel
franchiseefunnel.com
Supply Chain Summit
supplychainsummit.org
Hospital Growth Summit
hospitalgrowthsummit.org
CFO Summit
cfosummit.org
Safety Management Summit
safetysummit.org
Project Management Summit
projectmanagementsummit.org
CMO Summit
cmosummit.org
PR Summit
prsummit.org
Corp Summits
corpsummits.com
Quality Management Summit
qualitysummit.org
Corporate Counsel Summit
corporatecounselsummit.org
Executive Summits
execsummits.com
BizSummits
bizsummits.org
Marketing LeadFunnel
marketingleadfunnel.net
Meeting Setters
meetingsetters.com
CEO Ventures
ceoventures.com
HR LeadFunnel
hr-leadfunnel.com
Survey Executives
surveyexecutives.com
iListK
ilistk.com
IT LeadFunnel
itleadfunnel.com
Finance LeadFunnel
financeleadfunnel.com
GoPresent
gopresent.com
AffluentNames.com
affluentnames.com
Documents.me / Nouvou, Inc.
documents.me
AngelPool
angelpool.org
Critical Fit
criticalfit.com
HR Summit
hrsummit.org
Corp Venturing
corpventuring.com
PlugMeIn
plugmein.com
Retargetable
retargetable.com
LeadFunnel
leadfunnel.com
Pathfinder Careers
pathfindercareer.com
The Sales Management Association
salesmgtassoc.org
Executive Angels
executiveangels.net
CareerLeaper
careerleaper.com
Packed Events
packedevents.com
TeamEx
teamex.com
iCirc
icirc.net
HR Management Association
hrmanagementassociation.org
Product Conception Group
productconception.com
COO Summit
cooleaders.org
Hiring Spring
hiringspring.com
Exit Partners LLC
exitpartners.net
Exact Leads
exactleads.com
VisitorLeads
visitorleads.com
ListK
listk.com
LoudJob
loudjob.com
Franchisee Funnel
franchiseefunnel.com
Supply Chain Summit
supplychainsummit.org
Hospital Growth Summit
hospitalgrowthsummit.org
CFO Summit
cfosummit.org
Safety Management Summit
safetysummit.org
Project Management Summit
projectmanagementsummit.org
CMO Summit
cmosummit.org
PR Summit
prsummit.org
Corp Summits
corpsummits.com
Quality Management Summit
qualitysummit.org
Corporate Counsel Summit
corporatecounselsummit.org
Executive Summits
execsummits.com
BizSummits
bizsummits.org
Marketing LeadFunnel
marketingleadfunnel.net
Meeting Setters
meetingsetters.com
CEO Ventures
ceoventures.com
HR LeadFunnel
hr-leadfunnel.com
Survey Executives
surveyexecutives.com
iListK
ilistk.com
IT LeadFunnel
itleadfunnel.com
Finance LeadFunnel
financeleadfunnel.com
GoPresent
gopresent.com
AffluentNames.com
affluentnames.com
Documents.me / Nouvou, Inc.
documents.me
AngelPool
angelpool.org
Critical Fit
criticalfit.com
HR Summit
hrsummit.org
Corp Venturing
corpventuring.com
PlugMeIn
plugmein.com
Retargetable
retargetable.com
LeadFunnel
leadfunnel.com
Pathfinder Careers
pathfindercareer.com
The Sales Management Association
salesmgtassoc.org
Executive Angels
executiveangels.net
CareerLeaper
careerleaper.com
Packed Events
packedevents.com
TeamEx
teamex.com
iCirc
icirc.net
HR Management Association
hrmanagementassociation.org
Product Conception Group
productconception.com
Labels:
BizSummits
Monday 21 September 2015
Malware spam: "Your Sage subscription invoice is ready" / "noreply@sage.com"
This fake Sage email contains a malicious attachment.
The link in the email actually goes to a download location at Cubby rather than sageone.co.uk, this downloads a file invoice.zip which in turn contains a malicious executable invoice.scr which has a VirusTotal detection rate of 1/56. The Hybrid Analysis report shows that this is Upatre dropping the Dyre banking trojan, and one key indication of infection is traffic to the IP 197.149.90.166 in Nigeria.
From: noreply@sage.com [noreply@sage.com]
Date: 21 September 2015 at 11:30
Subject: Your Sage subscription invoice is ready
Dear Ralph Spivey
Account number: 45877254
Your Sage subscription invoice is now online and ready to view.
Sage One subscriptions
Please follow the link bellow to view/download your account invoice: http://www.sageone.co.uk/
Got a question about your invoice?
Call us on 1890 88 5045
If you're an Accountant, please call 1890 92 21 06
If you're a Business Partner, please call 1890 94 53 85
Kind Regards
The Sage UK Subscription Team
Please note: There is no unsubscribe option on this email, as it is a service message, not a marketing communication. This email was sent from an address that cannot accept replies. Please use the contact details above if you need to get in touch with us.
The link in the email actually goes to a download location at Cubby rather than sageone.co.uk, this downloads a file invoice.zip which in turn contains a malicious executable invoice.scr which has a VirusTotal detection rate of 1/56. The Hybrid Analysis report shows that this is Upatre dropping the Dyre banking trojan, and one key indication of infection is traffic to the IP 197.149.90.166 in Nigeria.
Tainted Network: "kfc.i.illuminationes.com/snitch" and VPS Hosting of Latvia (91.226.32.0/23)
I've been seeing some injection attacks since last week utilising hosting services of VPS Hosting in Latvia. These are continuing today, with attacks like this one [URLquery] which sends traffic to:
[donotclick]kfc.i.illuminationes.com/snitch
This is hosted on 91.226.33.54. The exploit is not clear at this point, but some sources say that this is some sort of TDS kit. The URLquery transaction flowchart shows the attack in action.
The injected script sends the keywords and referring site upstream, for example:
UPDATE:
ZScaler are also tracking their infection, an analysis of what it does can be found here.
[donotclick]kfc.i.illuminationes.com/snitch
This is hosted on 91.226.33.54. The exploit is not clear at this point, but some sources say that this is some sort of TDS kit. The URLquery transaction flowchart shows the attack in action.
The injected script sends the keywords and referring site upstream, for example:
[donotcliick]kfc.i.illuminationes.com/snitch?default_keyword=Team%20Tyra%20%7C%20The%20most%20popular%20equestrian%20website%20in%20Sweden%2FEurope&referrer=&se_referrer=&source=www.teamtyra.seAlthough the attacks in the past few days only seem to have utilised 91.226.33.54, an analysis of the netblock [pastebin] shows several bad or spammy sites in 91.226.32.0/23, so my recommendation is that you banish this range from your network.
UPDATE:
ZScaler are also tracking their infection, an analysis of what it does can be found here.
Labels:
Evil Network,
Injection Attacks,
Latvia,
Malware,
TDS
Friday 18 September 2015
Malware spam: "Transaction confirmation" / "donotreply@lloydsbank.co.uk"
This fake banking spam comes with a malicious attachment:
From donotreply@lloydsbank.co.ukAttached is a file Notice.zip which contains a malicious executable Value mortgage policy .exe (note the rogue space) which has a VirusTotal detection rate of 3/55. The Hybrid Analysis report shows activity consistent with Upatre/Dridex including a key indicator of traffic to 197.149.90.166 in Nigeria.
Date Fri, 18 Sep 2015 11:52:36 +0100
Subject Transaction confirmation
Dear Customer,
Please see attached the confirmation of transaction conducted from Your
account. Kindly sign and forward the copy to us for approval.
Best regards,
Your personal Manager
Thora Blanda
tel: 0345 300 0000
LLOYDS BANK.
E.ON "You've got mail" spam
I haven't used E.ON for a couple of years, and I no longer have an account with them. So I was surprised to get this E.ON-themed spam. Is it malware? No, it really is E.ON spamming me..
------------
From: E.ON Energy [eon@eonenergy.com]
Reply-To: "E.ON Energy" [eon@eonenergy.com]
Date: 17 September 2015 at 19:02
Subject: You've got mail
Ooookay. So it's a phish or malware, right? Well, in this case floating over the links clearly shows an eonenergy.com domain, rather than something malicious. And at least E.ON have shown good practice by using their own domain rather than some random tracking domain that others do.
It's been a long time since I logged onto E.ON because these days I generate all my electricity from a secondhand Russian nuclear reactor plucked from a rusty submarine that I have buried under the lawn.
Logging on to my account gives this message..
And from that point onwards there is nothing at all that I can do. I can't turn off the E.ON spam because I don't have an account with them!
It's probably 15 years or so since I registered on E.ON.. when I registered it was part of TXU, then PowerGen which then became E.ON. So if you have registered an account with any of those companies in the past decade and a half, then you might get this spam from E.ON, even if you closed your account a long time ago..
UPDATE:
E.ON have posted some information about the cock-up and an apology here.
------------
From: E.ON Energy [eon@eonenergy.com]
Reply-To: "E.ON Energy" [eon@eonenergy.com]
Date: 17 September 2015 at 19:02
Subject: You've got mail
| You've got mail. If you are having trouble viewing this email, you can view it here. |
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Helping our customers. We're on it. | 
|
|
 |
Disclaimer Notice This email has been sent by E.ON Energy Solutions Limited. While we have checked this email and any attachments for viruses, we cannot guarantee that they are virus-free. You must therefore take full responsibility for virus checking. This message and attachments are confidential and should only be read by those to whom they are addressed. If you are not the intended recipient, please contact us, delete the message from your computer and destroy any copies. Any distribution or copying without prior permission is prohibited. Internet communications are not always secure and therefore E.ON does not accept legal responsibility for this message. The recipient is responsible for verifying its authenticity before acting on the contents. Any views or opinions presented are solely those of the author and do not necessarily represent those of E.ON. Registered Address E.ON Energy Solutions Limited. Registered office: Westwood Way, Westwood Business Park, Coventry, CV4 8LG. Registered in England and Wales No. 3407430. CONSENT CSS |
Ooookay. So it's a phish or malware, right? Well, in this case floating over the links clearly shows an eonenergy.com domain, rather than something malicious. And at least E.ON have shown good practice by using their own domain rather than some random tracking domain that others do.
It's been a long time since I logged onto E.ON because these days I generate all my electricity from a secondhand Russian nuclear reactor plucked from a rusty submarine that I have buried under the lawn.
Logging on to my account gives this message..
And from that point onwards there is nothing at all that I can do. I can't turn off the E.ON spam because I don't have an account with them!
It's probably 15 years or so since I registered on E.ON.. when I registered it was part of TXU, then PowerGen which then became E.ON. So if you have registered an account with any of those companies in the past decade and a half, then you might get this spam from E.ON, even if you closed your account a long time ago..
UPDATE:
E.ON have posted some information about the cock-up and an apology here.
Thursday 17 September 2015
Malware spam: hrwfmailerprod@lancashire.gov.uk / REFURBISHMENT
This fake financial spam (presumably) comes in several different variants (I saw two):
The payload appears to be Upatre/Dyre as seen earlier today.
From "Workflow Mailer" [hrwfmailerprod@lancashire.gov.uk]The other version I had mentioned "QMDM - 5J673827 CDW Computer Centers Inc. - REFURBISHMENT" instead. The attachment appears to have a randomly-generated name e.g. REFURBISHMENT 7216378.zip and REFURBISHMENT 4435708.zip which contain a malicious executable REFURBISHMENT 7015295.scr which has a VirusTotal detection rate of 3/55.
To hp_printer@victimdomain.com
Date Thu, 17 Sep 2015 12:16:26 GMT
Subject FYI: Sent: Online Discussion Message for RFQ 6767609,1 (LCDC - NF014378 R.R. Donnelley & Sons Company - REFURBISHMENT)
From Mabel Winter
To hp_printer@victimdomain.com
Sent Thu, 17 Sep 2015 12:12:26 GMT
ID 7216378
Number 6767609,1
Title Q3EX - 1C995408 R.R. Donnelley & Sons Company - REFURBISHMENT
Negotiation Preview Immediately upon publishing
Negotiation Open Immediately upon publishing
Negotiation Close September 21, 2015 10:00 am GMT
Company R.R. Donnelley & Sons Company
Subject ITT Clarifications
To view the message, please open attachment.
The payload appears to be Upatre/Dyre as seen earlier today.
Malware spam: "Shell E-Bill for Week 38 2015"
This fake financial spam comes with a malicious attachment:
Attached is a file 28834_wk38_2015.zip containing a malicious executable 67482_wk38_2015.scr which has a detection rate of 2/56. Automated analysis is pending, but the payload is almost definitely Upatre/Dyre which has been consistently sending traffic to 197.149.90.166 (Cobranet, Nigeria) for some time now, so I suggest that you block or monitor that IP.
MD5:
0d9c66ffedce257ea346d2c7567310ac
From [invoices@ebillinvoice.com]
To administrator@victimdomain.com
Date Thu, 17 Sep 2015 11:10:15 GMT
Subject Shell E-Bill for Week 38 2015
Customer No : 28834
Email address : administrator@victimdomain.com
Attached file name : 28834_wk38_2015.PDF
Dear Customer,
Please find attached your invoice for Week 38 2015.
In order to open the attached PDF file you will need
the software Adobe Acrobat Reader.
For instructions of how to download and install this
software onto your computer please visit
http://www.adobe.com/products/acrobat/readstep2.html
If you have any queries regarding your e-bill you can contact us at invoices@ebillinvoice.com.
Yours sincerely
Customer Services
======================================================
This email, its content and any files transmitted with
it are confidential and intended solely for the use of
the individual(s) to whom it is addressed.
If you are not the intended recipient, be advised that
you have received this email in error and that any use,
dissemination, forwarding, printing or copying of
this email is strictly prohibited.
======================================================
Attached is a file 28834_wk38_2015.zip containing a malicious executable 67482_wk38_2015.scr which has a detection rate of 2/56. Automated analysis is pending, but the payload is almost definitely Upatre/Dyre which has been consistently sending traffic to 197.149.90.166 (Cobranet, Nigeria) for some time now, so I suggest that you block or monitor that IP.
MD5:
0d9c66ffedce257ea346d2c7567310ac
Wednesday 16 September 2015
Malware spam: "Lloyds Bank - Pendeford Securities - Please Read Action Required/PI Documents/ Region code East 2/ 8715811/"
This fake Lloyds Bank spam comes with a malicious payload:
In the sample I saw, there was a Word document ReportonTitle7117152.1Final.doc attached (detection rate 4/56), containing this malicious macro. The macro attempts to download components from the following locations:
thebackpack.fr/wp-content/themes/salient/wpbakery/js_composer/assets/lib/prettyphoto/images/prettyPhoto/light_rounded/66836487162.txt
thebackpack.fr/wp-content/themes/salient/wpbakery/js_composer/assets/lib/prettyphoto/images/prettyPhoto/light_rounded/sasa.txt
obiectivhouse.ro/wp-content/plugins/maintenance/load/images/fonts-icon/66836487162.txt
obiectivhouse.ro/wp-content/plugins/maintenance/load/images/fonts-icon/sasa.txt
A further download then takes place from:
vandestaak.com/css/libary.exe
This has a detection rate of 3/56. The general characteristics of this file make it a close match to the Upatre/Dyre payload of this concurrent spam run (automated analysis is pending).
Recommended blocklist:
197.149.90.166
vandestaak.com
thebackpack.fr
obiectivhouse.ro
MD5s:
4b944c5e668ea9236ac9ab3b1192243a
1939eba53a1289d68d1fb265d80e60a1
From: RSTNAME} Crabtree [Chang.Crabtree@lloydsbankcommercial.com]
Date: 15 September 2015 at 13:18
Subject: Lloyds Bank - Pendeford Securities - Please Read Action Required/PI Documents/ Region code East 2/ 8715811/
Please find attached our document pack for the above customer. Once completed please return via email to the below address.
If you have any queries relating to the above feel free to contact us at
MN2Lloydsbanking@lloydsbankcommercial.com
Lloyds Banking Group plc. Registered Office: The Mound, Edinburgh EH1 1YZ. Registered in Scotland no. SC95000. Telephone: 0131 225 4555. Lloyds Bank plc. Registered Office: 25 Gresham Street, London EC2V 7HN. Registered in England and Wales no. 2065. Telephone 0207626 1500. Bank of Scotland plc. Registered Office: The Mound, Edinburgh EH1 1YZ. Registered in Scotland no. SC327000. Telephone: 08457 21 31 41. Cheltenham & Gloucester plc. Registered Office: Barnett Way, Gloucester GL4 3RL. Registered in England and Wales 7117152. Telephone: 0845 603 1637
Lloyds Bank plc, Bank of Scotland plc are authorised by the Prudential Regulation Authority and regulated by the Financial Conduct Authority and Prudential Regulation Authority.
Cheltenham & Gloucester plc is authorised and regulated by the Financial Conduct Authority.
Halifax is a division of Bank of Scotland plc. Cheltenham & Gloucester Savings is a division of Lloyds Bank plc.
HBOS plc. Registered Office: The Mound, Edinburgh EH1 1YZ. Registered in Scotland no. SC453043.
This e-mail (including any attachments) is private and confidential and may contain privileged material. If you have received this e-mail in error, please notify the sender and delete it (including any attachments) immediately. You must not copy, distribute, disclose or use any of the information in it or any attachments. Telephone calls may be monitored or recorded.
In the sample I saw, there was a Word document ReportonTitle7117152.1Final.doc attached (detection rate 4/56), containing this malicious macro. The macro attempts to download components from the following locations:
thebackpack.fr/wp-content/themes/salient/wpbakery/js_composer/assets/lib/prettyphoto/images/prettyPhoto/light_rounded/66836487162.txt
thebackpack.fr/wp-content/themes/salient/wpbakery/js_composer/assets/lib/prettyphoto/images/prettyPhoto/light_rounded/sasa.txt
obiectivhouse.ro/wp-content/plugins/maintenance/load/images/fonts-icon/66836487162.txt
obiectivhouse.ro/wp-content/plugins/maintenance/load/images/fonts-icon/sasa.txt
A further download then takes place from:
vandestaak.com/css/libary.exe
This has a detection rate of 3/56. The general characteristics of this file make it a close match to the Upatre/Dyre payload of this concurrent spam run (automated analysis is pending).
Recommended blocklist:
197.149.90.166
vandestaak.com
thebackpack.fr
obiectivhouse.ro
MD5s:
4b944c5e668ea9236ac9ab3b1192243a
1939eba53a1289d68d1fb265d80e60a1
Subscribe to:
Posts (Atom)