While chasing down this exploit kit yesterday, I noticed an awful lot of related IP addresses and domains that also seemed to be hosting malware.
The characterstics of these malicious landing pages is that they use free domains (currently .co.vu) and seem to have a very short lifespan. As I write this, the following malicious domains are LIVE
ooshuchahxe.co.vu
ahjoneeshae.co.vu
phamiephim.co.vu
kaemahchuum.co.vu
pahsiefoono.co.vu
kaghaingai.co.vu
buengaiyei.co.vu
ohmiajusoo.co.vu
oodeerahshe.co.vu
paotuchepha.co.vu
aedeequeekou.co.vu
eikoosiexa.co.vu
phielaingi.co.vu
thohbeekee.co.vu
A typical exploit landing page looks like this [URLquery report] which appears to be the Nuclear EK.
These are hosted on the following Choopa LLC / Gamservers.com IP addresses (it is the same company with two different trading names) [clicking the IP leads to the VirusTotal results, ones identified as malicious are highlighted]:
108.61.165.69
108.61.165.70
108.61.165.96
108.61.167.160
108.61.172.139
108.61.175.125
108.61.177.107
108.61.177.89
All these malicious domains use the following nameservers:
ns1.thallsbe.com
ns1.yotelepa.com
ns1.zenteep.com
ns1.neverflouwks.com
ns1.daxpyorgilgere.com
ns1.irkoblik.com
ns2.thallsbe.com
ns2.yotelepa.com
ns2.zenteep.com
ns2.neverflouwks.com
ns2.daxpyorgilgere.com
ns2.irkoblik.com
Nameservers are mostly (but not all hosted on Choopa LLC IPs):
64.187.225.245
104.224.147.220
108.61.123.219
108.61.172.145
108.61.198.148
108.61.211.121
As I said, these domains see to have a very short life. I identified nearly 3000 domains using these nameservers, the following of which are flagged as malicious by Google (long list, sorry, scroll past it if you like):
offearfactory.cf
ukforsavectory.cf
ukforshivaflow.cf
soundchecker.cf
tobiahsebastiani.cf
crazystuff.ga
atproserafic.ga
soundchecker.ga
terriblelow.ml
stumbleupons.ml
ukforprimeebook.cf
greendriver.ga
ukforsavectory.ga
yellowcheck.ml
misterybook.cf
sporterafic.cf
thorteutsch.cf
imainconfig.ga
materofteck.ga
sporterafic.ga
pleskinebook.ga
lowensineflow.ga
warriordriver.ga
materofteck.ml
sporterafic.ml
lowensineflow.ml
mipkohoophw.cf
mipkoewushohn.cf
mipkoeerrw.ml
mipkohiocoh.ml
qdujbffg.cf
floraperf.cf
floreamva.cf
sintroota.cf
akcyvwkudu.cf
jepeugcpaq.cf
kzjzbbezgt.cf
rittfpynit.cf
unitedbeer.cf
vuktrontas.cf
wchiekohya.cf
wingasheng.cf
nikelnstate.cf
quitambient.cf
xotadddance.cf
xoteaddrack.cf
bloxianoiaba.cf
boyconroewom.cf
myfreenomapi.cf
walltaddates.cf
walltaddonce.cf
walltaddrave.cf
xoteaddotion.cf
trohqueenexai.cf
trotesaiheohu.cf
truechiekitha.cf
trueitheipoag.cf
vukontasixtas.cf
vuvatyisedron.cf
wallddforbake.cf
walltadddabit.cf
walltadddance.cf
walltadddsims.cf
wallteaddrack.cf
oproquanterbot.cf
veterloshamerr.cf
vuflowdeadcrow.cf
wallaerkinderr.cf
wallteaddotion.cf
wicomertulatti.cf
walltadddoppler.cf
amixionifyredhedi.cf
shamidgewoodpiste.cf
shoeufflorthrudis.cf
shoppaycleagoncad.cf
sosanasisernitive.cf
sourustieronixtur.cf
sparetediapletecu.cf
stekoneyredecklan.cf
subspironimitells.cf
sultintemicrearti.cf
coolmember.ga
krogralind.ga
rzanygngis.ga
unitedbeer.ga
wchiekohya.ga
weisewieku.ga
xotaddates.ga
xotaddrave.ga
junoreactor.ga
quitambient.ga
xoteaddrack.ga
dealerstrike.ga
trudahsheeso.ga
vumalworrest.ga
walltaddates.ga
walltaddonce.ga
walltaddrave.ga
wamipkoleoxw.ga
xoteaddotion.ga
proquantterms.ga
tritaeneiquoh.ga
trohqueenexai.ga
trotesaiheohu.ga
troyeachahgie.ga
truechiekitha.ga
truexauphudei.ga
victorysecret.ga
vuxeersktrace.ga
wallddforbake.ga
walltadddabit.ga
walltadddance.ga
walltadddsims.ga
wallteaddrack.ga
xotadddoppler.ga
veterloshamerr.ga
victoaddroplen.ga
vuflowdeadcrow.ga
vuvtrassktrace.ga
wallaerkinderr.ga
wallteaddotion.ga
wheallstechaxa.ga
wolscelipartin.ga
wolvestreyrmst.ga
walltadddoppler.ga
serckinvenaftovan.ga
shamidgewoodpiste.ga
shoppaycleagoncad.ga
sosanasisernitive.ga
sourustieronixtur.ga
sparetediapletecu.ga
stekoneyredecklan.ga
subspironimitells.ga
sultintemicrearti.ga
facilygda.ml
iqmhaslyzd.ml
kriendbasi.ml
queezerbot.ml
rittfpynit.ml
xotaddrave.ml
contermance.ml
crazyworlds.ml
junoreactor.ml
loborrowave.ml
quitambient.ml
vuxtronrace.ml
xoteaddrack.ml
bloxianoiaba.ml
trudahsheeso.ml
vumalworrest.ml
vumullefloor.ml
walltaddates.ml
walltaddonce.ml
walltaddrave.ml
xoteaddotion.ml
lodborrowpler.ml
proquantterms.ml
triceebicicha.ml
triilequadaev.ml
tritaeneiquoh.ml
troshiechooph.ml
trotesaiheohu.ml
victorysecret.ml
vuxeersktrace.ml
wallddforbake.ml
walltadddabit.ml
walltadddance.ml
walltadddsims.ml
wallteaddrack.ml
wamipkoicjnew.ml
oproquantables.ml
veterloshamerr.ml
victoaddroplen.ml
wallteaddotion.ml
wickleyoregene.ml
wolscelipartin.ml
walltadddoppler.ml
serckinvenaftovan.ml
shamidgewoodpiste.ml
shoeufflorthrudis.ml
shoppaycleagoncad.ml
sosanasisernitive.ml
sourustieronixtur.ml
sparetediapletecu.ml
stekoneyredecklan.ml
subspironimitells.ml
sultintemicrearti.ml
sintroota.tk
sionixire.tk
bugleryambur.tk
zarauphudei.cf
zaraachwahgie.cf
zaragietheeghe.cf
zarabixampw.ga
zaradhoophw.ga
zarasicjnew.ga
zarauphudei.ga
zaraachwahgie.ga
zaraeqwuadaev.ga
zaraheeteghoh.ga
zaraohgeegheis.ga
zaratiihuw.ml
zarabixampw.ml
zarasicjnew.ml
zarasorsarw.ml
zaraulleoxw.ml
zaraachwahgie.ml
zaraeqwuadaev.ml
zaraewneiquoh.ml
uzaraeserexwai.ml
zaragietheeghe.ml
zaraweethiocoh.ml
In addition, these domains are tagged as malicious by SURBL:
xoteaddrack.cf
wallddforbake.cf
xoteaddrack.ga
walltadddsims.ga
walltaddates.ml
walltadddabit.ml
wallteaddrack.ml
siewaxiesha.co.vu
fourkopoll.co.vu
kurramithompartherd.co.vu
These are the TLDs and SLDs being abused, operated by Freenom (cf, ga, gq, ml, tk) or CoDotVu (co.vu). It looks like perhaps Freenom cleaned up their space, but you can make your own mind up if you want to block traffic to these as a precaution:
co.vu
cf
ga
gq
ml
tk
A full list of all the domains that I can find associated with these servers can be found here [pastebin].
Recommended minimum blocklist (Choopa LLC IPs are highlighted):
108.61.123.219
108.61.165.69
108.61.165.70
108.61.165.96
108.61.167.160
108.61.172.139
108.61.172.145
108.61.175.125
108.61.177.107
108.61.177.89
108.61.198.148
108.61.211.121
64.187.225.245
104.224.147.220
UPDATE:
Choopa LLC say they have terminated those IPs. However, it may still be worth reviewing your logs for traffic to these servers as they might identify machines that have been compromised.
Wednesday, 7 January 2015
Exploit kits on Choopa LLC / Gameservers.com IP addresses
Labels:
Evil Network,
Malware,
Viruses
Invoice spam with malicious XLS file from multiple companies
This spam run looks very similar to this one going out at roughly the same time, except this has a malicious XLS file rather than a DOC/
The "sender" is spoofed from multiple companies, so far I have seen:
Courtney Stark
Senior Accounts Payable Specialist
AVIVA
Phyllis Cobb
Senior Accounts Payable Specialist
DIGITAL BARRIERS LTD
Colby Burris
Senior Accounts Payable Specialist
XAAR
Randy Welch
Senior Accounts Payable Specialist
CAMELLIA
Kendra Cervantes
Senior Accounts Payable Specialist
TRINITY EXPLORATION & PRODUCTION
In the samples I have seen, there are two slightly different malicious Excel files with fairly low detection rates [1] [2] containing one of these two macros [1] [2] [pastebin] which downloads an executable from one of the following locations:
http://87.106.165.232:8080/mans/pops.php
http://193.136.19.160:8080/mans/pops.php
These locations are also found with this spam run and the payload is identical.
From: Courtney Stark
Date: 7 January 2015 at 12:27
Subject: Invoice 1252.70 GBP
Please find attached invoice for 1252.70 GBP.
Any queries please contact us.
Courtney Stark
Senior Accounts Payable Specialist
AVIVA
The "sender" is spoofed from multiple companies, so far I have seen:
Courtney Stark
Senior Accounts Payable Specialist
AVIVA
Phyllis Cobb
Senior Accounts Payable Specialist
DIGITAL BARRIERS LTD
Colby Burris
Senior Accounts Payable Specialist
XAAR
Randy Welch
Senior Accounts Payable Specialist
CAMELLIA
Kendra Cervantes
Senior Accounts Payable Specialist
TRINITY EXPLORATION & PRODUCTION
In the samples I have seen, there are two slightly different malicious Excel files with fairly low detection rates [1] [2] containing one of these two macros [1] [2] [pastebin] which downloads an executable from one of the following locations:
http://87.106.165.232:8080/mans/pops.php
http://193.136.19.160:8080/mans/pops.php
These locations are also found with this spam run and the payload is identical.
"Remittance Advice" malware spam from multiple spoofed companies
This fake financial spam claims to be from one of several legitimate companies. They are not sending the spam, not have their systems been compromised. Instead, this has a malicious Word document attached.
These different fake senders have been spotted so far:
Reyna Alvarado
Senior Accounts Payable Specialist
AVATION PLC
Dominique Valenzuela
Senior Accounts Payable Specialist
HERMES PACIFIC INVESTMENTS PLC
Alfreda Carney
Senior Accounts Payable Specialist
RED ROCK RESOURCES
Dave Hancock
Senior Accounts Payable Specialist
HANSA TRUST
Kendra Cervantes
Senior Accounts Payable Specialist
TRINITY EXPLORATION & PRODUCTION
The amount of the so-called payment, the name of the sender and the attachment name changes in each case. So far I have spotted three different Word documents, all with low detection rates at VirusTotal [1] [2] [3] which contains one of three different macros [1] [2] [3] [pastebin] which downloads a second stage from one of the following locations:
http://193.136.19.160:8080/mans/pops.php
http://94.23.160.102:8080/mans/pops.php
http://87.106.165.232:8080/mans/pops.php
This file is downloaded as test.exe and is then moved to %TEMP%\1V2MUY2XWYSFXQ.exe. This has a VirusTotal detection rate of 4/56 and that report also says that it POSTs data to 194.146.136.1:8080 (PE "Filipets Igor Victorovych", Ukraine).
For research purposes, a copy of these files can be found here [password=infected]
From: Dominique Valenzuela
Date: 7 January 2015 at 11:38
Subject: Remittance Advice for 3996.63 GBP
Please find attached a remittance advice for recent BACS payment of 3996.63 GBP.
Any queries please contact us.
Dominique Valenzuela
Senior Accounts Payable Specialist
HERMES PACIFIC INVESTMENTS PLC
These different fake senders have been spotted so far:
Reyna Alvarado
Senior Accounts Payable Specialist
AVATION PLC
Dominique Valenzuela
Senior Accounts Payable Specialist
HERMES PACIFIC INVESTMENTS PLC
Alfreda Carney
Senior Accounts Payable Specialist
RED ROCK RESOURCES
Dave Hancock
Senior Accounts Payable Specialist
HANSA TRUST
Kendra Cervantes
Senior Accounts Payable Specialist
TRINITY EXPLORATION & PRODUCTION
The amount of the so-called payment, the name of the sender and the attachment name changes in each case. So far I have spotted three different Word documents, all with low detection rates at VirusTotal [1] [2] [3] which contains one of three different macros [1] [2] [3] [pastebin] which downloads a second stage from one of the following locations:
http://193.136.19.160:8080/mans/pops.php
http://94.23.160.102:8080/mans/pops.php
http://87.106.165.232:8080/mans/pops.php
This file is downloaded as test.exe and is then moved to %TEMP%\1V2MUY2XWYSFXQ.exe. This has a VirusTotal detection rate of 4/56 and that report also says that it POSTs data to 194.146.136.1:8080 (PE "Filipets Igor Victorovych", Ukraine).
For research purposes, a copy of these files can be found here [password=infected]
Malware spam: "Eliza Fernandes" / "NUCSOFT-Payroll December 2014"
This fake spam pretends to be from an Indian company called Nucsoft but it isn't, instead it comes with a malicious Word document attached. Nucsoft are not sending out the spam, nor have their systems been compromised in any way.
http://cerovski1.net.amis.hr/js/bin.exe
This is saved as %TEMP%\1V2MUY2XWYSFXQ.exe and has a VirusTotal detection rate of just 1/56.
The Malwr report shows network connections to the following IPs:
59.148.196.153 (HKBN, Hing Kong)
74.208.11.204 (1&1, US)
It also drops a DLL with a detection rate of 20/56, identified as Dridex.
Recommended blocklist:
59.148.196.153
74.208.11.204
Note - for research purposes, a copy of the DOC and dropped files is here [zip]. Password is "infected".
From: Eliza Fernandes [eliza_fernandes@nucsoft.co.in]Attached is a malicous Word document (not a PDF) called Payroll Dec'14.doc which has a VirusTotal detection rate of 3/56. This contains a malicious macro [pastebin] which downloads a component from the following location:
Date: 7 January 2015 at 07:27
Subject: NUCSOFT-Payroll December 2014
Please find the data for payroll processing.
Please forward the PDF of summary.
Regards,
Eliza Fernandes
NUCSOFT Ltd.
Finance Dept.
-------------------------------------------------------------------------------------------------
DISCLAIMER:
This message contains privileged and confidential information and is intended only for an individual named. If you are not the intended recipient, you should not disseminate, distribute, store, print, copy or deliver this message. Please notify the sender immediately by e-mail if you have received this e-mail by mistake and delete this e-mail from your system. E-mail transmission cannot be guaranteed to be secure or error-free as information could be intercepted,
-------------------------------------------------------------------------------------------------
NUCSOFT : With You - Until Success and Beyond....
Visit us at http://www.nucsoft.com
-------------------------------------------------------------------------------------------------
http://cerovski1.net.amis.hr/js/bin.exe
This is saved as %TEMP%\1V2MUY2XWYSFXQ.exe and has a VirusTotal detection rate of just 1/56.
The Malwr report shows network connections to the following IPs:
59.148.196.153 (HKBN, Hing Kong)
74.208.11.204 (1&1, US)
It also drops a DLL with a detection rate of 20/56, identified as Dridex.
Recommended blocklist:
59.148.196.153
74.208.11.204
Note - for research purposes, a copy of the DOC and dropped files is here [zip]. Password is "infected".
Tuesday, 6 January 2015
hqq.tv serving up exploit kit (via Digital Ocean and Choopa)
I will confess that I haven't had a lot of time to look at this, but here's an infection chain starting from a scummy-looking video streaming site called cine-stream.net. I do not recommend visiting any of the sites labelled [donotclick]
Step 1
[donotclick]cine-stream.net/1609-le-pre-nol-est-une-ordure-en-streaming.html
89.248.170.206 (Ecatel Ltd, Netherlands)
URLquery report
Step 2
[donotclick]hqq.tv/player/embed_player.php?vid=7SO84O65X5SM&autoplay=no
199.83.130.198 (Incapsula, US)
Step 3
[donotclick]agroristaler.info/dasimotulpes16.html
128.199.48.44 (Digital Ocean, Netherlands)
URLquery report
Step 4
[donotclick]aflesministal.info/chat.html
178.62.147.144 (Digital Ocean, Netherlands)
128.199.52.108 (Digital Ocean, Netherlands)
Step 5
[donotclick]pohfefungie.co.vu/VUZQBUgAAgtAGlc.html
[donotclick]eixaaweexum.co.vu/VxFVBkgAAgtAGlc.html
108.61.165.69 (Choopa LLC / Game Servers, Netherlands)
URLquery report
The Digital Ocean and Choopa IPs host several apparently malicious domains:
108.61.165.69
eixaaweexum.co.vu
ienaakeoke.co.vu
weswalkers.co.vu
pohfefungie.co.vu
vieleevethu.co.vu
178.62.147.144
128.199.52.108
sebitibir.info
abrisgalor.info
aflesministal.info
128.199.48.44
abibruget.info
alsonutird.info
fiflakutir.info
fistikopor.info
agroristaler.info
poliloparatoser.info
In my opinion, .co.vu domains are often bad news and are good candidates for blocking. In the mean time I would recommend the following minimum blocklist:
108.61.165.69
178.62.147.144
128.199.52.108
128.199.48.44
Step 1
[donotclick]cine-stream.net/1609-le-pre-nol-est-une-ordure-en-streaming.html
89.248.170.206 (Ecatel Ltd, Netherlands)
URLquery report
Step 2
[donotclick]hqq.tv/player/embed_player.php?vid=7SO84O65X5SM&autoplay=no
199.83.130.198 (Incapsula, US)
Step 3
[donotclick]agroristaler.info/dasimotulpes16.html
128.199.48.44 (Digital Ocean, Netherlands)
URLquery report
Step 4
[donotclick]aflesministal.info/chat.html
178.62.147.144 (Digital Ocean, Netherlands)
128.199.52.108 (Digital Ocean, Netherlands)
Step 5
[donotclick]pohfefungie.co.vu/VUZQBUgAAgtAGlc.html
[donotclick]eixaaweexum.co.vu/VxFVBkgAAgtAGlc.html
108.61.165.69 (Choopa LLC / Game Servers, Netherlands)
URLquery report
The Digital Ocean and Choopa IPs host several apparently malicious domains:
108.61.165.69
eixaaweexum.co.vu
ienaakeoke.co.vu
weswalkers.co.vu
pohfefungie.co.vu
vieleevethu.co.vu
178.62.147.144
128.199.52.108
sebitibir.info
abrisgalor.info
aflesministal.info
128.199.48.44
abibruget.info
alsonutird.info
fiflakutir.info
fistikopor.info
agroristaler.info
poliloparatoser.info
In my opinion, .co.vu domains are often bad news and are good candidates for blocking. In the mean time I would recommend the following minimum blocklist:
108.61.165.69
178.62.147.144
128.199.52.108
128.199.48.44
"PAYMENT ADVICE 06-JAN-2015" malware spam
This spam has a malicious attachment:
I have only seen one sample so far, with a document BACS092459_473.doc which has a VirusTotal detection rate of 0/56 and which contains this macro [pastebin] which attempts to download an additional component from:
http://206.72.192.15:8080/mans/pops.php
This is exactly the same file as seen in this parallel spam run today and it has the same characteristics.
From: Celeste , Senior Accountant
Date: 6 January 2015 at 10:13
Subject: PAYMENT ADVICE 06-JAN-2015
Dear all,
Payment has been made to you in amount GBP 18898,28 by BACS.
See attachment.
Regards,
Celeste
Senior Accountant
I have only seen one sample so far, with a document BACS092459_473.doc which has a VirusTotal detection rate of 0/56 and which contains this macro [pastebin] which attempts to download an additional component from:
http://206.72.192.15:8080/mans/pops.php
This is exactly the same file as seen in this parallel spam run today and it has the same characteristics.
Malware spam: SGBD National Payments Centre / Saint Gobain UK / This is your Remittance Advice
This fake financial spam has a malicious payload:
Note that this email is a forgery. Saint Gobain UK are not sending the spam, nor have their systems been compromised in any way. Instead, criminals are using a botnet to spam out malicious Excel documents.
Each email has a different reference number, and the attachment file name matches. The telephone number is randomly generated in each case, using a dialling code of 01484 which is Huddersfield (in the UK). There will probably be a lot of confused people in Huddersfield at the moment.
There are actually four different version of the malicious Excel file, none of which are detected by anti-virus vendors [1] [2] [3] [4] containing four different but similar macros [1] [2] [3] [4] [pastebin] which then download a component from one of the following locations:
http://213.174.162.126:8080/mans/pops.php
http://194.28.139.100:8080/mans/pops.php
http://206.72.192.15:8080/mans/pops.php
http://213.9.95.58:8080/mans/pops.php
This file is downloaded as test.exe and it then saved as %TEMP%\1V2MUY2XWYSFXQ.exe. It has a VirusTotal detection rate of just 3/48. That report shows that the malware then connects to the following URLs:
http://194.146.136.1:8080/
http://179.43.141.164/X9BMtSKOfaz/e&WGWM+o%3D_c%26%248/InRRqJL~L
http://179.43.141.164/TiHlXjsnCOo8%2C/fS%24P/VZFrel2ih%2Dlv+%26aTn
http://179.43.141.164/suELl1XsT%2CFX.k%26z4./sn%3F=/%3Ffw/HFBN@8J
http://179.43.141.164/fhmhi/igm/c&@%7E%2Dj.==m~cg_%2B%2C%3Daggs.%2Dkgm%26$~@fk@g/a%2Cgm+lkb%2D.~$kh/
194.146.136.1 is allocated to PE "Filipets Igor Victorovych" in Ukraine. 179.43.141.164 is Private Layer Incin Panama. I would definitely recommend blocking them and possibly the entire /24s in which they are hosted.
The Malwr report shows no activity, indicating that it is hardened against analysis.
Recommend blocklist:
194.146.136.1
179.43.141.164
213.174.162.126
194.28.139.100
206.72.192.15
213.9.95.58
Date: 6 January 2015 at 08:56
Subject: This is your Remittance Advice #ATS29858
DO NOT REPLY TO THIS EMAIL ADDRESS
Please find attached your remittance advice from Saint Gobain UK.
For any queries relating to this remittance please notify the Payment Enquiry Team on 01484913947
Regards,
SGBD National Payments Centre
Note that this email is a forgery. Saint Gobain UK are not sending the spam, nor have their systems been compromised in any way. Instead, criminals are using a botnet to spam out malicious Excel documents.
Each email has a different reference number, and the attachment file name matches. The telephone number is randomly generated in each case, using a dialling code of 01484 which is Huddersfield (in the UK). There will probably be a lot of confused people in Huddersfield at the moment.
There are actually four different version of the malicious Excel file, none of which are detected by anti-virus vendors [1] [2] [3] [4] containing four different but similar macros [1] [2] [3] [4] [pastebin] which then download a component from one of the following locations:
http://213.174.162.126:8080/mans/pops.php
http://194.28.139.100:8080/mans/pops.php
http://206.72.192.15:8080/mans/pops.php
http://213.9.95.58:8080/mans/pops.php
This file is downloaded as test.exe and it then saved as %TEMP%\1V2MUY2XWYSFXQ.exe. It has a VirusTotal detection rate of just 3/48. That report shows that the malware then connects to the following URLs:
http://194.146.136.1:8080/
http://179.43.141.164/X9BMtSKOfaz/e&WGWM+o%3D_c%26%248/InRRqJL~L
http://179.43.141.164/TiHlXjsnCOo8%2C/fS%24P/VZFrel2ih%2Dlv+%26aTn
http://179.43.141.164/suELl1XsT%2CFX.k%26z4./sn%3F=/%3Ffw/HFBN@8J
http://179.43.141.164/fhmhi/igm/c&@%7E%2Dj.==m~cg_%2B%2C%3Daggs.%2Dkgm%26$~@fk@g/a%2Cgm+lkb%2D.~$kh/
194.146.136.1 is allocated to PE "Filipets Igor Victorovych" in Ukraine. 179.43.141.164 is Private Layer Incin Panama. I would definitely recommend blocking them and possibly the entire /24s in which they are hosted.
The Malwr report shows no activity, indicating that it is hardened against analysis.
Recommend blocklist:
194.146.136.1
179.43.141.164
213.174.162.126
194.28.139.100
206.72.192.15
213.9.95.58
Friday, 2 January 2015
binarysmoney.com / clickmoneys.com / thinkedmoney.com "job" spam
I've been plagued with these for the past few days:
Subject lines include:
New employment opportunities
Staff Wanted
Employment invitation
new job
New job offer
Interesting Job
response
Spamvertised sites seen so far are binarysmoney.com, clickmoneys.com and thinkedmoney.com, all multihomed on the following IPs:
46.108.40.76 (Adnet Telecom / "Oancea Mihai Gabriel Intreprindere Individuala", Romania)
201.215.67.43 (VTR Banda Ancha S.A., Chile)
31.210.63.94 (Hosting Internet Hizmetleri Sanayi Ve Ticaret Anonim Sirketi, Turkey)
Another site hosted on these IPs is moneyproff.com. All the domains have apparently fake WHOIS details.
It looks like a money mule spam, but in fact it leads to some binary options trading crap.
There is no identifying information on the page at all. Trustworthy? Nope. But let's look at that relaxed looking chap at the top of the page, in a picture called matthew.png.
Well, that's just a Shutterstock stock photo that is pretty widely used on the web. In fact, everything about this whole thing is a cookie-cutter site with text and images copied from elsewhere.
Binary options are a haven for scammers, and my opinion is that this is such a scam given the spammy promotion and hidden identity of the operators. I would recommend that you avoid this and also block traffic to the following IPs and domains:
46.108.40.76
201.215.67.43
31.210.63.94
clickmoneys.com
thinkedmoney.com
binarysmoney.com
moneyproff.com
Date: 2 January 2015 at 11:02
Subject: response
Good day!
We considered your resume to be very attractive and we thought the vacant position in our company could be interesting for you.
We cooperate with different countries and currently we have many clients in the world.
Part-time and full-time employment are both currently important.
We offer a flat wage from $1500 up to $5000 per month.
The job offers a good salary so, interested candidates please registration on the our site: www.binarysmoney.com
Attention! Accept applications only on this and next week.
Respectively submitted
Personnel department
Subject lines include:
New employment opportunities
Staff Wanted
Employment invitation
new job
New job offer
Interesting Job
response
Spamvertised sites seen so far are binarysmoney.com, clickmoneys.com and thinkedmoney.com, all multihomed on the following IPs:
46.108.40.76 (Adnet Telecom / "Oancea Mihai Gabriel Intreprindere Individuala", Romania)
201.215.67.43 (VTR Banda Ancha S.A., Chile)
31.210.63.94 (Hosting Internet Hizmetleri Sanayi Ve Ticaret Anonim Sirketi, Turkey)
Another site hosted on these IPs is moneyproff.com. All the domains have apparently fake WHOIS details.
It looks like a money mule spam, but in fact it leads to some binary options trading crap.
There is no identifying information on the page at all. Trustworthy? Nope. But let's look at that relaxed looking chap at the top of the page, in a picture called matthew.png.
Well, that's just a Shutterstock stock photo that is pretty widely used on the web. In fact, everything about this whole thing is a cookie-cutter site with text and images copied from elsewhere.
Binary options are a haven for scammers, and my opinion is that this is such a scam given the spammy promotion and hidden identity of the operators. I would recommend that you avoid this and also block traffic to the following IPs and domains:
46.108.40.76
201.215.67.43
31.210.63.94
clickmoneys.com
thinkedmoney.com
binarysmoney.com
moneyproff.com
Wednesday, 31 December 2014
Evil network: 217.71.50.0/24 / ELTAKABEL-AS / TXTV d.o.o. Tuzla / aadeno@inet.ba
This post by Brian Krebs drew my attention to a block of Bosnian IP addresses with an unusually bad reputation. The first clue is given by Google's safe browsing diagnostics..
An investigation into what was lurking in this AS highlighted a problem block of 217.71.50.0/24 which contains very many bad sites, the WHOIS details for that block being..
inetnum: 217.71.48.0 - 217.71.63.255
descr: TXTV d.o.o. Tuzla
org: ORG-TdT1-RIPE
netname: BA-TXTV-20030807
country: BA
admin-c: IK879-RIPE
tech-c: IK879-RIPE
status: ALLOCATED PA
mnt-by: RIPE-NCC-HM-MNT
mnt-lower: MNT-NSC1
mnt-routes: MNT-NSC1
notify: ripe@txtv.ba
changed: hostmaster@ripe.net 20030807
changed: hostmaster@ripe.net 20040625
changed: hostmaster@ripe.net 20050719
changed: bitbucket@ripe.net 20081003
changed: hostmaster@ripe.net 20110804
changed: hostmaster@ripe.net 20140324
changed: bit-bucket@ripe.net 20140325
source: RIPE
organisation: ORG-TdT1-RIPE
org-name: TXTV d.o.o. Tuzla
org-type: LIR
address: TXTV d.o.o.
address: Admir Jaganjac
address: Focanska 1N
address: 75000
address: Tuzla
address: BOSNIA AND HERZEGOVINA
phone: +38735353333
fax-no: +38735266114
tech-c: TXTV1-RIPE
abuse-mailbox: abuse@txtv.ba
mnt-ref: MNT-TXTV
mnt-ref: RIPE-NCC-HM-MNT
mnt-by: RIPE-NCC-HM-MNT
admin-c: AJ2947-RIPE
admin-c: AA26986-RIPE
admin-c: IK879-RIPE
abuse-c: NSC11-RIPE
source: RIPE
e-mail: ripe@txtv.ba
changed: bitbucket@ripe.net 20140324
person: Igor Krneta
address: Majora Drage Bajalovica 18
address: 78000 Banjaluka, BA
e-mail: ripe@elta-kabel.com
phone: +387 51 961 001
nic-hdl: IK879-RIPE
mnt-by: MNT-NAVIGOSC
changed: ikrneta@navigosc.net 20071126
source: RIPE
route: 217.71.50.0/24
descr: Inet subnet #1
origin: AS31630
mnt-by: GENELEC-MNT
changed: aadeno@inet.ba 20061029
source: RIPE
I highlighted the part of most interest, which appears to be a block suballocated to someone using the email address aadeno@inet.ba.
I took a look at the sites hosted in this /24 and these are the results [csv]. There are 37 malicious websites (identified by Google) out of 185 that I found in this network range. The usual level of badness tends to be around 1%, but here it is 20%. Looking at the domains, it appears that there is nothing at all of value here and you can probably count them all as malicious.
Recommended blocklist:
217.71.50.0/24
darotkskeu.com
hijuvchr.com
humhfsara.com
lomospaoerotr.com
noerdfjkieswp.com
p28aa.com
pkoefkosaep.com
teeirkfoews.com
niggercar.es
invoice-ups.net
www-myups.net
invoice-myups.org
invoice-ups.org
office-hosts.org
softupdates.org
updatedns.org
www-myups.org
abdilo.ru
bihilafes.ru
cloudughtold.su
dedicnqher.su
dnspqajr.su
dnsxjkd.su
hosrvnwj.su
hostfjwmr.su
hostsple.su
hostyksn.su
servergotold.su
serverhersse.su
servermexyr.su
serveruey.su
serverxpqk.su
serviolt.su
ugulddedic.su
usehostru.su
uttofhost.su
vpsjsner.su
vpslopwz.su
baycityads.biz
blingstarscpm.biz
plustimber.biz
plutoads.biz
tempomedia.biz
dsffdsk323721372131.com
ny-discount-sales.com
rxmega-shop.com
rx-product-shop.com
safe-refill-rx.com
viphealhtmarket.com
datadirects.eu
dataremark.eu
dataresultsid.eu
datasynchronize.eu
datavail.eu
datsunplus.eu
dedistarid.eu
detectionstream1.eu
dmpcheck.eu
drellmedia.eu
elitemembers.eu
eplymedia.eu
eravideoads.eu
euserviceid.eu
forwardingref.eu
glowcheck.eu
iprecognition.eu
newsettingso.eu
ordealsting.eu
planacheck.eu
pluginverifys.eu
proudeuro.eu
refforwarding.eu
resellerapis.eu
rpmstatus.eu
samjectstar.eu
secondtierdirect.eu
selldataset.eu
soundads.eu
spokenads.eu
stretchstrong.eu
syncdata1.eu
trackingstreamchk.eu
trackstats.eu
trafficlax.eu
verablade.eu
club-rx-bestseller.ru
fuckaustralia.ru
rx-bestseller.ru
Safe BrowsingSome of those domains rang a bell to do with recent malware attacks. One odd thing that struck me was that this is a sparsely populated but relatively large collection of IP addresses that appear to be mostly allocated to broadband customers rather than web hosts.
Diagnostic page for AS198252 (ELTAKABEL-AS)
What happened when Google visited sites hosted on this network?
Of the 165 site(s) we tested on this network over the past 90 days, 6 site(s), including, for example, office-hosts.org/, invoice-ups.org/, refforwarding.eu/, served content that resulted in malicious software being downloaded and installed without user consent.
The last time Google tested a site on this network was on 2014-12-31, and the last time suspicious content was found was on 2014-12-26.
Has this network hosted sites acting as intermediaries for further malware distribution?
Over the past 90 days, we found 10 site(s) on this network, including, for example, iprecognition.eu/, invoice-ups.net/, datavail.eu/, that appeared to function as intermediaries for the infection of 525 other site(s) including, for example, webtretho.com/, detik.com/, zaodich.com/.
Has this network hosted sites that have distributed malware?
Yes, this network has hosted sites that have distributed malicious software in the past 90 days. We found 15 site(s), including, for example, iprecognition.eu/, invoice-ups.net/, datavail.eu/, that infected 572 other site(s), including, for example, webtretho.com/, detik.com/, zaodich.com/.
An investigation into what was lurking in this AS highlighted a problem block of 217.71.50.0/24 which contains very many bad sites, the WHOIS details for that block being..
inetnum: 217.71.48.0 - 217.71.63.255
descr: TXTV d.o.o. Tuzla
org: ORG-TdT1-RIPE
netname: BA-TXTV-20030807
country: BA
admin-c: IK879-RIPE
tech-c: IK879-RIPE
status: ALLOCATED PA
mnt-by: RIPE-NCC-HM-MNT
mnt-lower: MNT-NSC1
mnt-routes: MNT-NSC1
notify: ripe@txtv.ba
changed: hostmaster@ripe.net 20030807
changed: hostmaster@ripe.net 20040625
changed: hostmaster@ripe.net 20050719
changed: bitbucket@ripe.net 20081003
changed: hostmaster@ripe.net 20110804
changed: hostmaster@ripe.net 20140324
changed: bit-bucket@ripe.net 20140325
source: RIPE
organisation: ORG-TdT1-RIPE
org-name: TXTV d.o.o. Tuzla
org-type: LIR
address: TXTV d.o.o.
address: Admir Jaganjac
address: Focanska 1N
address: 75000
address: Tuzla
address: BOSNIA AND HERZEGOVINA
phone: +38735353333
fax-no: +38735266114
tech-c: TXTV1-RIPE
abuse-mailbox: abuse@txtv.ba
mnt-ref: MNT-TXTV
mnt-ref: RIPE-NCC-HM-MNT
mnt-by: RIPE-NCC-HM-MNT
admin-c: AJ2947-RIPE
admin-c: AA26986-RIPE
admin-c: IK879-RIPE
abuse-c: NSC11-RIPE
source: RIPE
e-mail: ripe@txtv.ba
changed: bitbucket@ripe.net 20140324
person: Igor Krneta
address: Majora Drage Bajalovica 18
address: 78000 Banjaluka, BA
e-mail: ripe@elta-kabel.com
phone: +387 51 961 001
nic-hdl: IK879-RIPE
mnt-by: MNT-NAVIGOSC
changed: ikrneta@navigosc.net 20071126
source: RIPE
route: 217.71.50.0/24
descr: Inet subnet #1
origin: AS31630
mnt-by: GENELEC-MNT
changed: aadeno@inet.ba 20061029
source: RIPE
I highlighted the part of most interest, which appears to be a block suballocated to someone using the email address aadeno@inet.ba.
I took a look at the sites hosted in this /24 and these are the results [csv]. There are 37 malicious websites (identified by Google) out of 185 that I found in this network range. The usual level of badness tends to be around 1%, but here it is 20%. Looking at the domains, it appears that there is nothing at all of value here and you can probably count them all as malicious.
Recommended blocklist:
217.71.50.0/24
darotkskeu.com
hijuvchr.com
humhfsara.com
lomospaoerotr.com
noerdfjkieswp.com
p28aa.com
pkoefkosaep.com
teeirkfoews.com
niggercar.es
invoice-ups.net
www-myups.net
invoice-myups.org
invoice-ups.org
office-hosts.org
softupdates.org
updatedns.org
www-myups.org
abdilo.ru
bihilafes.ru
cloudughtold.su
dedicnqher.su
dnspqajr.su
dnsxjkd.su
hosrvnwj.su
hostfjwmr.su
hostsple.su
hostyksn.su
servergotold.su
serverhersse.su
servermexyr.su
serveruey.su
serverxpqk.su
serviolt.su
ugulddedic.su
usehostru.su
uttofhost.su
vpsjsner.su
vpslopwz.su
baycityads.biz
blingstarscpm.biz
plustimber.biz
plutoads.biz
tempomedia.biz
dsffdsk323721372131.com
ny-discount-sales.com
rxmega-shop.com
rx-product-shop.com
safe-refill-rx.com
viphealhtmarket.com
datadirects.eu
dataremark.eu
dataresultsid.eu
datasynchronize.eu
datavail.eu
datsunplus.eu
dedistarid.eu
detectionstream1.eu
dmpcheck.eu
drellmedia.eu
elitemembers.eu
eplymedia.eu
eravideoads.eu
euserviceid.eu
forwardingref.eu
glowcheck.eu
iprecognition.eu
newsettingso.eu
ordealsting.eu
planacheck.eu
pluginverifys.eu
proudeuro.eu
refforwarding.eu
resellerapis.eu
rpmstatus.eu
samjectstar.eu
secondtierdirect.eu
selldataset.eu
soundads.eu
spokenads.eu
stretchstrong.eu
syncdata1.eu
trackingstreamchk.eu
trackstats.eu
trafficlax.eu
verablade.eu
club-rx-bestseller.ru
fuckaustralia.ru
rx-bestseller.ru
Labels:
Bosnia,
Evil Network,
Malware,
Viruses
NetGuard Toolbar (ngcmp.com) spam
Sometimes a spam comes through and it isn't immediately obvious what they are trying to do:
An examination of those two PSInet addresses shows the following domains are associated with them:
ncmp.co
ngmp.co
ngcmp.com
ng-portal.com
ngcmp.net
ng-central.net
luxebagscloset.com
reviewwordofmouth.com
All of these domains have anonymous WHOIS details, but you can see that there is a common pattern here. I don't recommend that you visit spam sites, but I did in this case to see what it was about.
It appears to be some crappy toolbar called NetGuard and indeed the ngcmp.com pulls down many resources from the netguardtoolbar.com website. The site claims to be from a company called "NG Systems" but gives no other identification. netguardtoolbar.com has also had anonymous WHOIS details since it was registered in 2008.
If we look at the "Privacy" page of the site, we can see what this is all about.
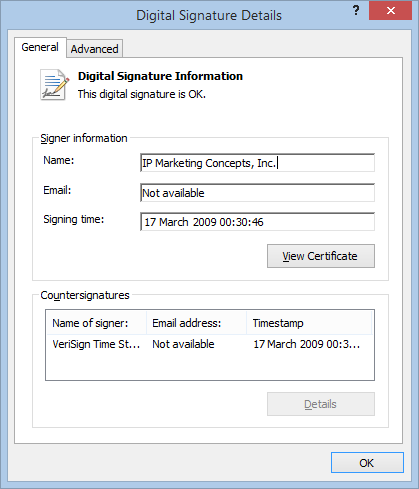
Predictably, there seems to be no such corporation as "NG Systems", but if you download the Toolbar it turns out it is digitally signed by a company called "IP Marketing Concepts, Inc."
If we drill down into the certificate details we can find out more about this mystery corporation.
Some Googling around finds a Delware corporation number 4099908 founded in 2006, but as Delware is a "go to" place for corporation trying to hide their identities, it is hard to find out more information without paying.
The executable itself is tagged by only one AV engine as malicious, but VirusTotal does note that it looks like a PUA. Malwr notes that individual components appear to be Russian in origin.
So all in all, this spam is being sent out by a company that goes a very, very long way to disguise its origins. Would you really want to either install their product or advertise on their network?
From: Brad Lorien [bclorien@ngcmp.com]There is no link or attachment in the email. So presumably the spammer is soliciting replies to the email address bclorien@ngcmp.com which is a valid address. The domain ngcmp.com uses a mail server mail.ngcmp.com to receive email messages, hosted on 38.71.66.127 (PSInet / Virtual Empire, US). A look at the spam headers are rather revealing..
Date: 31 December 2014 at 01:12
Subject: Real estate (12/30/2014)
Our company reaches an online community of almost 41 million people,
who are mostly US and Canadian based. We have the ability to present
our nearly 41 million strong network with a best, first choice when
they are looking online for what your company does.
We are seeking a preferred choice to send our people who are looking
for real estate in Abilene and surrounding markets.
I’m in the office weekdays from 9:00 AM to 5:00 PM Pacific time.
Best regards,
Brad Lorien
Network Specialist, SPS EServices
Phone: (877) 489.2929, ext. 64
Received: from [38.71.66.126] (port=60856 helo=ngcmp.net)We can see that the spam was sent via a relay at 38.71.66.126 which is one IP different from the server handling incoming mail, which pretty much firmly identifies that whoever controls the ngcmp.com domain is actually sending the spam. The mail headers also identify the originating IP as well as the relay, which is a Verizon Wireless customer at 75.215.49.211, possibly someone sending spam using throwaway cell phones to avoid being traced.
by [redacted] with esmtp (Exim 4.80)
(envelope-from <bclorien@ngcmp.com>)
id 1Y67tI-0006Ub-TC
for [redacted]; Wed, 31 Dec 2014 01:16:17 +0000
Received: from mail.ngcmp.com (211.sub-75-215-49.myvzw.com [75.215.49.211])
by ngcmp.net (Postfix) with ESMTPA id 0812E3E34E
for <[redacted]>; Tue, 30 Dec 2014 19:18:13 -0600 (CST)
(envelope-from bclorien@ngcmp.com)
An examination of those two PSInet addresses shows the following domains are associated with them:
ncmp.co
ngmp.co
ngcmp.com
ng-portal.com
ngcmp.net
ng-central.net
luxebagscloset.com
reviewwordofmouth.com
All of these domains have anonymous WHOIS details, but you can see that there is a common pattern here. I don't recommend that you visit spam sites, but I did in this case to see what it was about.
It appears to be some crappy toolbar called NetGuard and indeed the ngcmp.com pulls down many resources from the netguardtoolbar.com website. The site claims to be from a company called "NG Systems" but gives no other identification. netguardtoolbar.com has also had anonymous WHOIS details since it was registered in 2008.
If we look at the "Privacy" page of the site, we can see what this is all about.
NetGuard does not ask you for any personally identifiable information such as an email address, phone number, your name, or any such data. We do track IP addresses only of those who choose to download our App. We also track downloads of the NetGuard App, as well as uninstalls of the NetGuard App, so that we may have accurate data on those two items only in dealing with our Advertisers. Our Advertisers assist us in maintaining our NetGuard App Community, which allows us to provide the public with even more features as time and innovation allows. NetGuard does, as part of our advertising process, allow Advertisers who maintain an active Advertiser Account, to present their websites when an end user of the NetGuard does a search on any of the major search engines. This in no way changes the search results contained on the native pages of the major search engines, but does allow NetGuard to continue to present the general public with more options as time and innovation allows.This is basically adware. Going back to the original spam message, these "41 million people" are presumably suckers who have downloaded this crap, and NG Systems are busy spamming out to find more low-life advertisers to fill up their network. Or am I just sounding annoyed?
Predictably, there seems to be no such corporation as "NG Systems", but if you download the Toolbar it turns out it is digitally signed by a company called "IP Marketing Concepts, Inc."
If we drill down into the certificate details we can find out more about this mystery corporation.
CN = IP Marketing Concepts, Inc.
OU = SECURE APPLICATION DEVELOPMENT
O = IP Marketing Concepts, Inc.
L = Lewes
S = Delaware
C = US
Some Googling around finds a Delware corporation number 4099908 founded in 2006, but as Delware is a "go to" place for corporation trying to hide their identities, it is hard to find out more information without paying.
The executable itself is tagged by only one AV engine as malicious, but VirusTotal does note that it looks like a PUA. Malwr notes that individual components appear to be Russian in origin.
So all in all, this spam is being sent out by a company that goes a very, very long way to disguise its origins. Would you really want to either install their product or advertise on their network?
Wednesday, 24 December 2014
Malware spam: Rhianna Wellings / Rhianna@teckentrupdepot.co.uk / Signature Invoice 44281
Teckentrup Depot UK is a legitimate UK company, but these emails are not from Teckentrup Depot and they contain a malicious attachment. Teckentrup Depot has not been hacked, their database has not been compromised, and they are not responsible for this in any way.
http://Lichtblick-tiere.de/js/bin.exe
http://sunfung.hk/js/bin.exe
The file is saved into the location %TEMP%\1V2MUY2XWYSFXQ.exe and currently has a VirusTotal detection rate of just 4/56. The ThreatExpert report shows traffic to the following IPs:
74.208.11.204 (1&1 Internet, US)
81.169.156.5 (Strato AG, Germany)
59.148.196.153 (HKBN, Hong Kong)
According to the Malwr report it also drops a malicious DLL with a detection rate of 24/56, detected as the Dridex banking trojan.
Recommended blocklist:
74.208.11.204
81.169.156.5
59.148.196.153
lichtblick-tiere.de
sunfung.hk
From: Rhianna Wellings [Rhianna@teckentrupdepot.co.uk]Attached is a malicious Word document called Signature Invoice.doc which comes in two different versions, both of which are undetected by AV vendors [1] [2]. Each one contains a different macro [1] [2] [pastebin] which then downloads an additional component from one of these two locations:
Date: 24 December 2014 at 07:54
Subject: Signature Invoice 44281
Your report is attached in DOC format.
To load the report, you will need the Microsoft® Word® reader, available to download at http://www.microsoft.com/
http://Lichtblick-tiere.de/js/bin.exe
http://sunfung.hk/js/bin.exe
The file is saved into the location %TEMP%\1V2MUY2XWYSFXQ.exe and currently has a VirusTotal detection rate of just 4/56. The ThreatExpert report shows traffic to the following IPs:
74.208.11.204 (1&1 Internet, US)
81.169.156.5 (Strato AG, Germany)
59.148.196.153 (HKBN, Hong Kong)
According to the Malwr report it also drops a malicious DLL with a detection rate of 24/56, detected as the Dridex banking trojan.
Recommended blocklist:
74.208.11.204
81.169.156.5
59.148.196.153
lichtblick-tiere.de
sunfung.hk
Tuesday, 23 December 2014
"Remittance Advice" spam comes with a malicious Excel attachment
This fake remittance advice comes with a malicious Excel attachment.
The reference in the subject varies, and the name of the attachment always matches (so in this case DPRC93.xls). There are in fact three different versions of the document, all of which have a malicious macro. At the moment, this is poorly-detected by AV vendors [1] [2] [3] [4].
If you read this blog regularly then you might have seen me mention these attacks many times before, and most of these have a familiar pattern. However, the macro has now changed completely, as it now loads some of the data from the Excel spreadsheet itself.
The macro itself looks like this [pastebin] and as far as I can tell from it, it loads some data from the Excel spreadsheet and puts it into a file %TEMP%\windows.vbs. So far I have seen four different scripts [1] [2] [3] [4] which download a component from one of the following locations:
http://185.48.56.133:8080/sstat/lldvs.php
http://95.163.121.27:8080/sstat/lldvs.php
http://92.63.88.100:8080/sstat/lldvs.php
http://92.63.88.106:8080/sstat/lldvs.php
It appears that this email is downloaded as test.exe and is then saved as %TEMP%\servics.exe.
The ThreatExpert report shows traffic to the following:
194.146.136.1 (PE "Filipets Igor Victorovych", Ukraine)
80.237.255.196 (Denes Balazs / HostEurope, Germany)
85.25.20.107 (PlusServer AG, Germany)
VirusTotal indicates a detection rate of just 3/54, and identifies it as Dridex.
Recommended blocklist:
194.146.136.1
80.237.255.196
85.25.20.107
185.48.56.133
95.163.121.27
92.63.88.100
92.63.88.106
Note that there are two IPs acting as downloaders in the 92.63.88.0/24 range (MWTV, Latvia). It may be that you would also want to block that range as well.
From: Whitney
Date: 23 December 2014 at 09:12
Subject: Remittance Advice -DPRC93
Confidentiality and Disclaimer: This email and its attachments are intended for the addressee only and may be confidential or the subject of legal privilege.
If this email and its attachments have come to you in error you must take no action based on them, nor must you copy them, distribute them or show them to anyone.
Please contact the sender to notify them of the error.
This email and any attached files have been scanned for the presence of computer viruses. However, you are advised that you open any attachments at your own risk.
Please note that electronic mail may be monitored in accordance with the Telecommunications (Lawful Business Practices)(Interception of Communications) Regulations 2000.
The reference in the subject varies, and the name of the attachment always matches (so in this case DPRC93.xls). There are in fact three different versions of the document, all of which have a malicious macro. At the moment, this is poorly-detected by AV vendors [1] [2] [3] [4].
If you read this blog regularly then you might have seen me mention these attacks many times before, and most of these have a familiar pattern. However, the macro has now changed completely, as it now loads some of the data from the Excel spreadsheet itself.
The macro itself looks like this [pastebin] and as far as I can tell from it, it loads some data from the Excel spreadsheet and puts it into a file %TEMP%\windows.vbs. So far I have seen four different scripts [1] [2] [3] [4] which download a component from one of the following locations:
http://185.48.56.133:8080/sstat/lldvs.php
http://95.163.121.27:8080/sstat/lldvs.php
http://92.63.88.100:8080/sstat/lldvs.php
http://92.63.88.106:8080/sstat/lldvs.php
It appears that this email is downloaded as test.exe and is then saved as %TEMP%\servics.exe.
The ThreatExpert report shows traffic to the following:
194.146.136.1 (PE "Filipets Igor Victorovych", Ukraine)
80.237.255.196 (Denes Balazs / HostEurope, Germany)
85.25.20.107 (PlusServer AG, Germany)
VirusTotal indicates a detection rate of just 3/54, and identifies it as Dridex.
Recommended blocklist:
194.146.136.1
80.237.255.196
85.25.20.107
185.48.56.133
95.163.121.27
92.63.88.100
92.63.88.106
Note that there are two IPs acting as downloaders in the 92.63.88.0/24 range (MWTV, Latvia). It may be that you would also want to block that range as well.
Monday, 22 December 2014
"Tiket alert" spam. Tiket? Really?
Sometimes the spammers don't really try very hard. Like they have to make a quota or something. A "Tiket alert" from the FBI.. or is it FBR? Really?
This has a VirusTotal detection rate of 2/54. Between that VirusTotal analysis and the Anubis analysis we can see that the malware attempts to phone home to:
http://202.153.35.133:42463/2212us12//0/51-SP3/0/
http://202.153.35.133:42463/2212us12//1/0/0/
http://moorfuse.com/images/unk12.pne
202.153.35.133 is Excell Media Pvt Ltd, India.
Recommended blocklist:
202.153.35.133
moorfuse.com
mitsuba-kenya.com
negociomega.com
From: FBR service [jon.wo@fbi.com]I have seen another version of this where the download location is negociomega.com/ticket/fsb.html. Clicking on the link downloads a file ticket8724_pdf.zip which in turn contains a malicious executable ticket8724_pdf.exe.
Date: 22 December 2014 at 18:29
Subject: Tiket alert
Look at the link file for more information.
http://mitsuba-kenya.com/ticket/fsb.html
Assistant Vice President, FBR service
Management Corporation
This has a VirusTotal detection rate of 2/54. Between that VirusTotal analysis and the Anubis analysis we can see that the malware attempts to phone home to:
http://202.153.35.133:42463/2212us12/
http://202.153.35.133:42463/2212us12/
http://moorfuse.com/images/unk12.pne
202.153.35.133 is Excell Media Pvt Ltd, India.
Recommended blocklist:
202.153.35.133
moorfuse.com
mitsuba-kenya.com
negociomega.com
Angler EK on 193.109.69.59
193.109.69.59 (Mir Telematiki Ltd, Russia) is hosting what appears to be the Angler Exploit Kit.
The infection chain that I have seen is as follows (don't click those links, obviously):
[donotclick]www.opushangszer.hu/hora-at-200-b-csiptetos-gitarhangolo/1-864-359
-->
[donotclick]bettersaid.net/7b614b6f9fb62682c46d303fea879a38.swf
-->
[donotclick]www.smallbusinesssnapshot.com/
a6107b69be5422d82da0c2109cc7f20f.php?q=7a7581fad469383e7313d27d1cedf2d3
-->
[donotclick]qwe.holidayspeedfive.biz/em3t8gxum0
-->
[donotclick]qwe.holidayspeedfive.biz/
KuCRwb_Bwr38O4rT6dqEUCT9x5K26Bw_PNEHE3DJ_U9vgmcD31TZILN2BlAmHabL
The last step is where the badness happens, hosted on 193.109.69.59 (Mir Telematiki Ltd, Russia) which is also being used to host the following malicious domains:
qwe.holidayspeedsix.biz
qwe.holidayspeedfive.biz
qwe.holidayspeedseven.biz
A quick look at the contents of 193.109.68.0/23 shows some other questionable sites. A look at the sites hosted in this /23 indicates that most of them appear to be selling counterfeit goods, so blocking the entire /23 will probably be no great loss.
Recommended minimum blocklist:
193.109.69.59
holidayspeedsix.biz
holidayspeedfive.biz
holidayspeedseven.biz
The infection chain that I have seen is as follows (don't click those links, obviously):
[donotclick]www.opushangszer.hu/hora-at-200-b-csiptetos-gitarhangolo/1-864-359
-->
[donotclick]bettersaid.net/7b614b6f9fb62682c46d303fea879a38.swf
-->
[donotclick]www.smallbusinesssnapshot.com/
a6107b69be5422d82da0c2109cc7f20f.php?q=7a7581fad469383e7313d27d1cedf2d3
-->
[donotclick]qwe.holidayspeedfive.biz/em3t8gxum0
-->
[donotclick]qwe.holidayspeedfive.biz/
KuCRwb_Bwr38O4rT6dqEUCT9x5K26Bw_PNEHE3DJ_U9vgmcD31TZILN2BlAmHabL
The last step is where the badness happens, hosted on 193.109.69.59 (Mir Telematiki Ltd, Russia) which is also being used to host the following malicious domains:
qwe.holidayspeedsix.biz
qwe.holidayspeedfive.biz
qwe.holidayspeedseven.biz
A quick look at the contents of 193.109.68.0/23 shows some other questionable sites. A look at the sites hosted in this /23 indicates that most of them appear to be selling counterfeit goods, so blocking the entire /23 will probably be no great loss.
Recommended minimum blocklist:
193.109.69.59
holidayspeedsix.biz
holidayspeedfive.biz
holidayspeedseven.biz
Friday, 19 December 2014
Malware spam: "Blocked Transaction. Case No 970332"
Date: 19 December 2014 at 16:06In the sample I have seen, the attachment is ACH transfer 1336.doc which despite the name is actually a .DOCX file, which has a VirusTotal dectection rate of 4/54. Inside are a series of images detailing how to turn off macro security.. which is a very bad idea.
Subject: Blocked Transaction. Case No 970332
The Automated Clearing House transaction (ID: 732021371), recently initiated from your online banking account, was rejected by the other financial institution.
Canceled ACH transaction
ACH file Case ID 083520
Transaction Amount 1458.42 USD
Sender e-mail info@victimdomain
Reason of Termination See attached statement
Please open the word file enclosed with this email to get more info about this issue.
Malware spam: no-replay@my-fax.com / "Employee Documents - Internal Use"
This fake fax spam leads to malware:
http://newsurveyresults.com/myfax/company.html
http://ChallengingDomesticAbuse.co.uk/myfax/company.html
http://crematori.org/myfax/company.html
http://gnrcorbus.com/myfax/company.html
http://sonata-arctica.wz.cz/myfax/company.html
Clicking the link downloads a file fax8127480_924_pdf.zip which in turn contains a malicious executable fax8127480_924.exe which has a VirusTotal detection rate of 3/55. Most automated analysis tools are inconclusive [1] [2] but the VT report shows network connections to the following locations:
http://202.153.35.133:40542/1912uk22//0/51-SP3/0/
http://202.153.35.133:40542/1912uk22//1/0/0/
http://natural-anxiety-remedies.com/wp-includes/images/wlw/pack22.pne
Recommended blocklist:
202.153.35.133
natural-anxiety-remedies.com
From: Fax [no-replay@my-fax.com]The download locations in the email vary, so far I have seen:
Date: 19 December 2014 at 15:37
Subject: Employee Documents - Internal Use
DOCUMENT NOTIFICATION, Powered by NetDocuments
DOCUMENT NAME: Fax Documents
DOCUMENT LINK: http://crematori.org/myfax/company.html
Documents are encrypted in transit and store in a secure repository
---------------------------------------------------------------------------------
This message may contain information that is privileged and confidential. If you received this transmission in error, please notify the sender by reply email and delete the message and any attachments.
http://newsurveyresults.com/myfax/company.html
http://ChallengingDomesticAbuse.co.uk/myfax/company.html
http://crematori.org/myfax/company.html
http://gnrcorbus.com/myfax/company.html
http://sonata-arctica.wz.cz/myfax/company.html
Clicking the link downloads a file fax8127480_924_pdf.zip which in turn contains a malicious executable fax8127480_924.exe which has a VirusTotal detection rate of 3/55. Most automated analysis tools are inconclusive [1] [2] but the VT report shows network connections to the following locations:
http://202.153.35.133:40542/1912uk22/
http://202.153.35.133:40542/1912uk22/
http://natural-anxiety-remedies.com/wp-includes/images/wlw/pack22.pne
Recommended blocklist:
202.153.35.133
natural-anxiety-remedies.com
Malware spam: "BACS payment Ref:901109RW"
This spam comes with a malicious attachment, in a format similar to the following:
To add credibility, the attachment has the same name as the reference in the subject and body text (in this case it is 901109RW.xls). The reference is randomly generated.
So far, I have seen three different type of attachment, all undetected by AV vendors [1] [2] [3] containing a different malicious macro each [1] [2] [3] [pastebin]. These macros then try to download an executable from the following locations:
http://78.129.153.23/sstat/lldvs.php
http://5.9.253.183/sstat/lldvs.php
http://185.48.56.123/sstat/lldvs.php
The file is downloaded as test.exe and is then moved to %TEMP%\VMUYXWYSFXQ.exe. It has a VirusTotal detection rate of 2/54. VT also reports that it phones home to 194.146.136.1 (PE "Filipets Igor Victorovych", Ukraine)
Additional analysis is pending.
UPDATE:
A further version of this is doing the rounds with an attachment which also has zero detections at VirusTotal and a different macro [pastebin], however it downloads the same binary from http://78.129.153.23/sstat/lldvs.php as the previous example does.
From: Fern
Date: 19 December 2014 at 10:09
Subject: BACS payment Ref:901109RW
Please see below our payment confirmation for funds into your account on Tuesday re invoice 901109RW
Accounts Assistant
Tel: 01874 662 346
Fax: 01874 501 248
To add credibility, the attachment has the same name as the reference in the subject and body text (in this case it is 901109RW.xls). The reference is randomly generated.
So far, I have seen three different type of attachment, all undetected by AV vendors [1] [2] [3] containing a different malicious macro each [1] [2] [3] [pastebin]. These macros then try to download an executable from the following locations:
http://78.129.153.23/sstat/lldvs.php
http://5.9.253.183/sstat/lldvs.php
http://185.48.56.123/sstat/lldvs.php
The file is downloaded as test.exe and is then moved to %TEMP%\VMUYXWYSFXQ.exe. It has a VirusTotal detection rate of 2/54. VT also reports that it phones home to 194.146.136.1 (PE "Filipets Igor Victorovych", Ukraine)
Additional analysis is pending.
UPDATE:
A further version of this is doing the rounds with an attachment which also has zero detections at VirusTotal and a different macro [pastebin], however it downloads the same binary from http://78.129.153.23/sstat/lldvs.php as the previous example does.
Thursday, 18 December 2014
Malware spam: aquaid.co.uk "Card Receipt"
[UPDATE: as of December 2015, there is a new version of the spam doing the rounds]
This spam claims to be from the legitimate firm AquAid, but it isn't. Instead it comes with a malcious attachment. The email is a forgery, AquAid are not sending the spam, nor have their systems been compromised in any way.
In the sample I have seen, the attachment is called CAR014 151239.doc which is malicious, but only has a VirusTotal detection rate of 2/54. This particular document (note that there are usually several different documents in the spam run) contains this malicious macro [pastebin]. This macro downloads a malware executable from:
http://sardiniarealestate.info/js/bin.exe
..which is saved as %TEMP%\YEWZMJFAHIB.exe - this has a marginally better detection rate of 3/53.
The ThreatExpert report shows connections to the following two IPs:
74.208.11.204 (1&1, US)
81.169.156.5 (Strato AG, Germany)
The Malwr report shows that it drops a DLL which is very poorly detected but is probably the Dridex banking trojan.
Recommended blocklist:
74.208.11.204
81.169.156.5
FOR RESEARCHERS ONLY: a copy of the malicious DOC attachment plus dropped files can be found here. Password is "infected". Only handle these if you know what you are doing.
http://forpetsonly.cz/js/bin.exe
This file has a VirusTotal detection rate of 2/57. The Malwr report shows it phoning home to:
59.148.196.153
74.208.11.204
It also drops a DLL with a detection rate of 2/57.
http://junidesign.de/js/bin.exe
http://jacekhondel.w.interia.pl/js/bin.exe
This malware is the same as used in this spam run.
This spam claims to be from the legitimate firm AquAid, but it isn't. Instead it comes with a malcious attachment. The email is a forgery, AquAid are not sending the spam, nor have their systems been compromised in any way.
From: Tracey Smith [tracey.smith@aquaid.co.uk]
Date: 18 December 2014 at 07:24
Subject: Card Receipt
HiPlease find attached receipt of payment made to us todayRegardsTraceyTracey Smith| Branch AdministratorAquAid | Birmingham & Midlands CentralUnit 35 Kelvin Way Trading Estate | West Bromwich | B70 7TPTelephone: 0121 525 4533Fax: 0121 525 3502Mobile: 07795328895Email: tracey.smith@aquaid.co.ukAquAid really is the only drinks supplier you will ever need with our huge product range. With products ranging from bottled and mains fed coolers ranging up to coffee machines and bespoke individual one off units we truly have the right solution for all environments. We offer a refreshing ethical approach to drinks supply in that we support both Christian Aid and Pump Aid with a donation from all sales. All this is done while still offering a highly focused local service and competitive pricing. A personalised sponsorship certificate is available for all clients showing how you are helping and we offer £25 for any referral that leads to business.************************************************************ *********
AquAid Franchising Ltd is a company registered in England and Wales with registered number 3505477 and registered office at 51 Newnham Road, Cambridge, CB3 9EY, UK. This message is intended only for use by the named addressee and may contain privileged and/or confidential information. If you are not the named addressee you should not disseminate, copy or take any action in reliance on it. If you have received this message in error please notify the sender and delete the message and any attachments accompanying it immediately. Neither AquAid nor any of its Affiliates accepts liability for any corruption, interception, amendment, tampering or viruses occurring to this message in transit or for any message sent by its employees which is not in compliance with AquAid corporate policy.
In the sample I have seen, the attachment is called CAR014 151239.doc which is malicious, but only has a VirusTotal detection rate of 2/54. This particular document (note that there are usually several different documents in the spam run) contains this malicious macro [pastebin]. This macro downloads a malware executable from:
http://sardiniarealestate.info/js/bin.exe
..which is saved as %TEMP%\YEWZMJFAHIB.exe - this has a marginally better detection rate of 3/53.
The ThreatExpert report shows connections to the following two IPs:
74.208.11.204 (1&1, US)
81.169.156.5 (Strato AG, Germany)
The Malwr report shows that it drops a DLL which is very poorly detected but is probably the Dridex banking trojan.
Recommended blocklist:
74.208.11.204
81.169.156.5
FOR RESEARCHERS ONLY: a copy of the malicious DOC attachment plus dropped files can be found here. Password is "infected". Only handle these if you know what you are doing.
UPDATE 2015-01-13
This spam keeps coming back every few days or so. This time the attachment has a VirusTotal detection rate of 3/57 and the malicious macro it contains [pastebin] downloads from:http://forpetsonly.cz/js/bin.exe
This file has a VirusTotal detection rate of 2/57. The Malwr report shows it phoning home to:
59.148.196.153
74.208.11.204
It also drops a DLL with a detection rate of 2/57.
UPDATE 2015-02-25
Another version of this spam run is in progress, with these malicious macros [1] [2] downloading from the following locations:http://junidesign.de/js/bin.exe
http://jacekhondel.w.interia.pl/js/bin.exe
This malware is the same as used in this spam run.
Wednesday, 17 December 2014
"Blocked ACH Transfer" spam has a malicious DOC attachment
Another spam run pushing a malicious Word attachment..
Attached is a file ACH transaction 3360.doc which isn't actually a Word 97-2003 document at all, but a malicious Word 2007 document that would normally have a .DOCX extension (which is basically a ZIP file). The current VirusTotal detection rate of this is just 1/55.
Inside this is a malicious macro [pastebin] which downloads a file from:
http://www.lynxtech.com.hk/images/tn.exe
This has a VirusTotal detection rate of just 1/54. The Malwr report shows it POSTING to 5.187.1.78 (Fornex Hosting, Germany) and also a query to 209.208.62.36 (Atlantic.net, US). Presumably this then drops additional components onto the infected system, although I do not know what they are.
Recommended blocklist:
5.187.1.78
209.208.62.36
Date: 17 December 2014 at 07:27
Subject: Blocked ACH Transfer
The ACH transaction (ID: 618003565), recently sent from your online banking account, was rejected by the Electronic Payments Association.
Canceled transaction
ACH file Case ID 623742
Total Amount 2644.93 USD
Sender e-mail info@mobilegazette.com
Reason for rejection See attached word file
Please see the document provided below to have more details about this issue.
Attached is a file ACH transaction 3360.doc which isn't actually a Word 97-2003 document at all, but a malicious Word 2007 document that would normally have a .DOCX extension (which is basically a ZIP file). The current VirusTotal detection rate of this is just 1/55.
Inside this is a malicious macro [pastebin] which downloads a file from:
http://www.lynxtech.com.hk/images/tn.exe
This has a VirusTotal detection rate of just 1/54. The Malwr report shows it POSTING to 5.187.1.78 (Fornex Hosting, Germany) and also a query to 209.208.62.36 (Atlantic.net, US). Presumably this then drops additional components onto the infected system, although I do not know what they are.
Recommended blocklist:
5.187.1.78
209.208.62.36
"PL REMITTANCE DETAILS ref844127RH" malware spam
This fake remittance advice comes with a malicious Excel attachment.
The reference in the subject and the name of the Excel attachment differ from email to email, but are always consistent in the same message. There are two poorly detected malicious Excel files that I have seen [1] [2] containing two slightly different macros [1] [2] which then reach out to the following download locations:
http://23.226.229.112:8080/stat/lldv.php
http://38.96.175.139:8080/stat/lldv.php
The file from these locations is downloaded as test.exe and is then saved to %TEMP%\VMHKWKMKEUQ.exe. This has a VirusTotal detection rate of 1/55. The ThreatTrack report [pdf] shows it POSTing to the following IP:
194.146.136.1 (PE "Filipets Igor Victorovych", Ukraine)
This IP has been used in several recent attacks and I strongly recommend blocking it.
The Malwr report also shows it dropping a malicious DLL identified as Dridex.
The ThreatExpert report gives some different IPs being contacted:
80.237.255.196 (Denes Balazs / HostEurope, Germany)
85.25.20.107 (PlusServer, Germany)
The Ukrainian IP is definitely malicious, but if you wanted to establish maximum protection then I would recommend the following blocklist:
194.146.136.1
80.237.255.196
85.25.20.107
23.226.229.112
38.96.175.139
From: Briana
Date: 17 December 2014 at 08:42
Subject: PL REMITTANCE DETAILS ref844127RH
The attached remittance details the payment of £664.89 made on 16-DEC-2014 by BACSE.
This email was generated using PL Payment Remittance of Integra Finance System.
Can you please check that your supplier details are correct, if any changes are required please email back to this email address quoting your remittance reference.
The reference in the subject and the name of the Excel attachment differ from email to email, but are always consistent in the same message. There are two poorly detected malicious Excel files that I have seen [1] [2] containing two slightly different macros [1] [2] which then reach out to the following download locations:
http://23.226.229.112:8080/stat/lldv.php
http://38.96.175.139:8080/stat/lldv.php
The file from these locations is downloaded as test.exe and is then saved to %TEMP%\VMHKWKMKEUQ.exe. This has a VirusTotal detection rate of 1/55. The ThreatTrack report [pdf] shows it POSTing to the following IP:
194.146.136.1 (PE "Filipets Igor Victorovych", Ukraine)
This IP has been used in several recent attacks and I strongly recommend blocking it.
The Malwr report also shows it dropping a malicious DLL identified as Dridex.
The ThreatExpert report gives some different IPs being contacted:
80.237.255.196 (Denes Balazs / HostEurope, Germany)
85.25.20.107 (PlusServer, Germany)
The Ukrainian IP is definitely malicious, but if you wanted to establish maximum protection then I would recommend the following blocklist:
194.146.136.1
80.237.255.196
85.25.20.107
23.226.229.112
38.96.175.139
Spam: "Localizan a los 43 estudiantes desaparecidos en Ayotzinapa"
This Spanish-language malware spam comes with a malicious attachment.
The Word document contains a malicious macro, and detailed instructions for the victim on how to disable the inbuilt security to enable it to run.
Once this has been done, the malicious macro [pastebin] runs. This attempts to download a file from:
http://www.milusz.eu/templates/default/00/ss.exe
At the moment, this download location is coming up with a 404 error. If the download were to work, it would save the file as %TEMP%\ test00010.exe. The Word document has a moderate detection rate of 10/54.
This type of malicious spam has been around for a long time, and this particular technique seems to be exclusively in Spanish, I have never seen this attack in English or any other language.
From: El UniversalThis translates roughly as:
Date: 16 December 2014 at 09:06
Subject: Localizan a los 43 estudiantes desaparecidos en Ayotzinapa.
Localizan a los 43 estudiantes desaparecidos en Ayotzinapa.
Hoy 16 de diciembre del 2014 por la madrugada, agentes de la Policía Ministerial de Guerrero
han localizado con vida a los 43 estudiantes, desaparecidos el dia 26 de septiembre del 2014.
Para ver imágenes exclusivas del reencuentro de los estudiantes con sus familias, y las condiciones en que
vivieron durante su secuestro, anexamos un documento en este correo electrónico en formato Microsoft Word.
El Universal © todos los Derechos Reservados 2014.
Located at 43 students missing in Ayotzinapa.This email relates to the kidnapping and possible murder of 43 Mexican students which has been blamed by some on the Mexican Police.
Today December 16, 2014 at dawn, agents of the Ministerial Police Guerrero
have been located alive at 43 students, missing the day September 26, 2014.
To view exclusive footage of the reunion of students and their families, and the conditions under which
They lived during his abduction, we attach a document to this email in Microsoft Word format.
The Universal © All Rights Reserved 2014.
The Word document contains a malicious macro, and detailed instructions for the victim on how to disable the inbuilt security to enable it to run.
Once this has been done, the malicious macro [pastebin] runs. This attempts to download a file from:
http://www.milusz.eu/templates/default/00/ss.exe
At the moment, this download location is coming up with a 404 error. If the download were to work, it would save the file as %TEMP%\ test00010.exe. The Word document has a moderate detection rate of 10/54.
This type of malicious spam has been around for a long time, and this particular technique seems to be exclusively in Spanish, I have never seen this attack in English or any other language.
Malware spam: UK GEOLOGY PROJECT by "Rough & Tumble" with "Moussa Minerals" [roughandtumble63@yahoo.co.uk]
This somewhat odd and terse spam comes with a malicious attachment.
http://openstacksg.com/js/bin.exe
http://worldinlens.net/js/bin.exe
This malicious executable is saved as %TEMP%\ADGYMSEKRJE.exe and has a detection rate of only 2/54.
Is is common with recent similar malware attempts, it attempts to phone home to 74.208.11.204 (1&1, US) as shown in the ThreatTrack report [pdf]. The Malwr report indicates a dropped file with an MD5 of ee826c184155a1fa1aea984f914e606a which is probably Dridex.
From: UK GEOLOGY PROJECT by "Rough & Tumble" with "Moussa Minerals" <roughandtumble63@yahoo.co.uk>There is no body text, but there is an malicious DOC attachment named 20140918_122519.doc which come in two slightly different versions with poor detection rates [1] [2]. The macros have been subtly changed from recent spam runs [1] [2] [pastebin] and download a second stage from one of the following locations:
Date: 17 December 2014 at 07:20
Subject: Invoice as requested
http://openstacksg.com/js/bin.exe
http://worldinlens.net/js/bin.exe
This malicious executable is saved as %TEMP%\ADGYMSEKRJE.exe and has a detection rate of only 2/54.
Is is common with recent similar malware attempts, it attempts to phone home to 74.208.11.204 (1&1, US) as shown in the ThreatTrack report [pdf]. The Malwr report indicates a dropped file with an MD5 of ee826c184155a1fa1aea984f914e606a which is probably Dridex.
Monday, 15 December 2014
Malware spam: IFS Applications / vitacress.co.uk / DOC-file for report is ready
This fake payment advice spam is not from Vitacress but is a forgery with a malicious Word document attached.
http://gv-roth.de/js/bin.exe
http://notaxcig.com/js/bin.exe
This file is saved as %TEMP%\DYIATHUQLCW.exe and is currently has a VirusTotal detection rate of just 1/52.
The ThreatExpert report and Malwr report shows attempted connections to the following IPs which have been used in many recent attacks and should be blocked if you can:
203.172.141.250 (Ministry of Education, Thailand)
74.208.11.204 (1&1, US)
The malware almost definitely drops the Dridex trojan onto the target system, but I have not been able to get a sample of this yet.
http://finepack.co.in/js/bin.exe
http://loneleaf.ca/js/bin.exe
This file is saved as %TEMP%\TQWTGECOROR.exe and it currently has a detection rate of just 1/54. The Malwr report shows it posting to 74.208.11.204 yet again, although it does not show the dropped Dridex binary that I would expect to see.
From: IFS Applications [Do_Not_Reply@vitacress.co.uk]Attached is a file Payment Advice_593016.doc which is actually one of two different documents with zero detections at VirusTotal [1] [2] and contain one of two malicious macros [1] [2] [pastebin] that download a malware binary from one of the following locations:
Date: 15 December 2014 at 07:49
Subject: DOC-file for report is ready
The DOC-file for report Payment Advice is ready and is attached in this mail.
http://gv-roth.de/js/bin.exe
http://notaxcig.com/js/bin.exe
This file is saved as %TEMP%\DYIATHUQLCW.exe and is currently has a VirusTotal detection rate of just 1/52.
The ThreatExpert report and Malwr report shows attempted connections to the following IPs which have been used in many recent attacks and should be blocked if you can:
203.172.141.250 (Ministry of Education, Thailand)
74.208.11.204 (1&1, US)
The malware almost definitely drops the Dridex trojan onto the target system, but I have not been able to get a sample of this yet.
UPDATE 2014-12-16
A second wave of spam is in progress with a pair of new malicious Word documents with low detection rates [1] [2] containing new macros [1] [2] that download a malicious file from the following locations:http://finepack.co.in/js/bin.exe
http://loneleaf.ca/js/bin.exe
This file is saved as %TEMP%\TQWTGECOROR.exe and it currently has a detection rate of just 1/54. The Malwr report shows it posting to 74.208.11.204 yet again, although it does not show the dropped Dridex binary that I would expect to see.
Subscribe to:
Posts (Atom)