A follow-up to this post, I took a look at the netblocks 5.133.179.0/24 and 212.38.166.0/24 suballocated to:
person: Oleg Nikol'skiy
address: British Virgin Islands, Road Town, Tortola, Drake Chambers
phone: +18552100465
e-mail: abuse@ipserver.su
nic-hdl: ON929-RIPE
mnt-by: IPSERVER-MNT
changed: abuse@ipserver.su 20150528
created: 2015-05-28T11:11:09Z
last-modified: 2015-05-28T11:11:09Z
source: RIPE
I'm going to say straight away that my methodology is flawed, but I will share what I have. Very many IPs in this range have hosted badness in the past year-and-a-bit (e.g. 5.133.179.165), mostly using subdomains.. to the extent that there are too many sites to analyse easily if I take the data from a passive DNS service.
Instead, I elected to use the DomainTools reverse DNS which limits the results to domains only (not subdomains) and these are mostly active sites. Running the list through my analyser checks that the IPs are valid, and would normally tell me things such as the Google Safebrowsing Diagnostics and SURBL rating.
Here's what is odd. None of the sites that I found [pastebin] have a negative reputation, I would expect to see about 1% in a normal sample, and out of 399 sites it comes back with zero. In fact, none of these sites seem to have any web presence at all, and all the ones that I have tried come back with almost no references on Google at all.
I am going to suggest that there is nothing of value in these IP ranges, and given that historically .SU domains have a bad reputation, then my suggestion is that you block traffic to:
5.133.179.0/24
212.38.166.0/24
In the meantime I will continue digging..
Tuesday 8 September 2015
Monday 7 September 2015
Something evil on 184.105.163.192/26 / White Falcon Communications / Dmitry Glazyrin
So.. I spotted some Nuclear EK (or some other Flash exploit) traffic on our network which attracted my interest. The IP in question was 184.105.163.243 hosted on what appears to be a Hurricane Electric IP. Personally, I don't tend to see a lot of bad stuff on HE so I looked more closely at the IP WHOIS and saw it was part of a range 184.105.163.192/26 suballocated to:
contact:ID;I:POC-DC-1258
contact:Auth-Area:contacts
contact:Class-Name:contact
contact:Name:Dmitry Glazyrin
contact:Company:White Falcon Communications
contact:Street-Address:3-758 Riverside Dr
contact:City:Port Coquitlam
contact:Province:BC
contact:Postal-Code:V3B 7V8
contact:Country-Code:CA
contact:Phone:+1-510-580-4100
The next step was to query the range using DNSDB to see what has been hosted there. This came back with several thousand sites that have been hosted there in the past, the following of which are still hosted in the 184.105.163.192/26 range now..
bilettver.ru
ituslugi-ekb.ru
kerept.ru
porno-gt.com
pornosup.com
redkrab.com
vgubki.com
erotubik.com
autowagen.ru
decoitalcolor.ru
jimbobox.ru
kr-enot.ru
alemanas.ru
dynamo-energia.ru
master-lesa.ru
kinoprosmotra.net
multi-torrent.com
pl-games.ru
voyeur-hard.com
fishemania.com
learnigo.ru
qazashki.net
surfus.ru
mysuppadomainname.gq
kinoprosmotrov.net
multtracker.com
kyricabgr.tk
onlyhdporno.com
stat-irc.tk
white-wolves.tk
blondescript.com
dc-dcbcf352.hotvideocentral.com
wishfishworld.com
5ka.info
igro-baza1.ru
igro-baza2.ru
igro-baza3.ru
igro-baza4.ru
igro-baza5.ru
kinorelizov.net
torrent-mult.com
trailer-games.ru
vvpvv10.ru
vvpvv9.ru
todoke.ru
glazikvovana.cf
glazikvovana.ga
glazikvovana.gq
glazikvovana.ml
glazikvovana.tk
glazikvovki.cf
glazikvovki.ga
glazikvovki.gq
glazikvovki.ml
glazikvovki.tk
popochkavovana.cf
popochkavovana.ga
popochkavovana.gq
popochkavovana.ml
popochkavovana.tk
popochkavovki.cf
popochkavovki.ga
popochkavovki.gq
popochkavovki.ml
popochkavovki.tk
resnichkavovana.cf
resnichkavovana.ga
resnichkavovana.gq
resnichkavovana.ml
resnichkavovana.tk
resnichkavovki.cf
resnichkavovki.ga
resnichkavovki.gq
resnichkavovki.ml
resnichkavovki.tk
samaragss.ru
wechkavovana.cf
wechkavovana.ga
wechkavovana.gq
wechkavovana.ml
wechkavovana.tk
wechkavovki.cf
wechkavovki.ga
wechkavovki.gq
wechkavovki.ml
wechkavovki.tk
zalypkavovana.ml
zalypkavovana.tk
zalypkavovki.cf
zalypkavovki.ga
zalypkavovki.gq
zalypkavovki.ml
zalypkavovki.tk
zybikvovana.cf
zybikvovana.ga
zybikvovana.gq
zybikvovana.ml
zybikvovana.tk
zybikvovki.cf
zybikvovki.ga
zybikvovki.gq
zybikvovki.ml
zybikvovki.tk
staffrc.com
stopudof.com
35igr.ru
adandc.ru
avgyst.ru
comedy24.ru
e7ya.ru
funrussia.ru
ladykafe.ru
med-cafe.ru
mykazantip.ru
ohotaforum.ru
powerpoint-ppt.ru
sibledy.ru
turistvip.ru
ya-pisatel.ru
kypitest.ru
anykadavai.tk
forwarditaly.org
getyourimesh.com
mymobi.ml
yellowfrance.org
Sites that are flagged as malware by Google are highlighted and these are all hosted on 184.105.163.243. But what was interesting was what White Falcon Communications have been hosting in the past. When I ran the entirety of all the sites from DNSDB through my checker, I got some interesting results* [csv].
Out of 2867 sites analysed, 1973 (69%) sites had either hosted malware or were spammy. Some of the unrated sites are clearly phishing sites (e.g. usabanksecurity.com). Although these sites are not hosted on White Falcon Communications IPs now, they all have been at some point in the past.
So, who is this outfit? Well, it didn't take to come up with a couple of news stories, firstly this one where White Falcon had been raided by police in Canada in connection with C2 infrastructure for the Citadel botnet. That was followed by this story where White Falcon was allegedly suing law enforcement back, due to alleged "negligence".
However, given the sheer volume of crap that White Falcon has hosted in the past and its current problem with exploit kits, I would definitely recommend blocking traffic to 184.105.163.192/26 to be on the safe side.
* fields are domain name, current IP address, MyWOT ratings, Google Safebrowsing rating, SURBL status.
contact:ID;I:POC-DC-1258
contact:Auth-Area:contacts
contact:Class-Name:contact
contact:Name:Dmitry Glazyrin
contact:Company:White Falcon Communications
contact:Street-Address:3-758 Riverside Dr
contact:City:Port Coquitlam
contact:Province:BC
contact:Postal-Code:V3B 7V8
contact:Country-Code:CA
contact:Phone:+1-510-580-4100
The next step was to query the range using DNSDB to see what has been hosted there. This came back with several thousand sites that have been hosted there in the past, the following of which are still hosted in the 184.105.163.192/26 range now..
bilettver.ru
ituslugi-ekb.ru
kerept.ru
porno-gt.com
pornosup.com
redkrab.com
vgubki.com
erotubik.com
autowagen.ru
decoitalcolor.ru
jimbobox.ru
kr-enot.ru
alemanas.ru
dynamo-energia.ru
master-lesa.ru
kinoprosmotra.net
multi-torrent.com
pl-games.ru
voyeur-hard.com
fishemania.com
learnigo.ru
qazashki.net
surfus.ru
mysuppadomainname.gq
kinoprosmotrov.net
multtracker.com
kyricabgr.tk
onlyhdporno.com
stat-irc.tk
white-wolves.tk
blondescript.com
dc-dcbcf352.hotvideocentral.com
wishfishworld.com
5ka.info
igro-baza1.ru
igro-baza2.ru
igro-baza3.ru
igro-baza4.ru
igro-baza5.ru
kinorelizov.net
torrent-mult.com
trailer-games.ru
vvpvv10.ru
vvpvv9.ru
todoke.ru
glazikvovana.cf
glazikvovana.ga
glazikvovana.gq
glazikvovana.ml
glazikvovana.tk
glazikvovki.cf
glazikvovki.ga
glazikvovki.gq
glazikvovki.ml
glazikvovki.tk
popochkavovana.cf
popochkavovana.ga
popochkavovana.gq
popochkavovana.ml
popochkavovana.tk
popochkavovki.cf
popochkavovki.ga
popochkavovki.gq
popochkavovki.ml
popochkavovki.tk
resnichkavovana.cf
resnichkavovana.ga
resnichkavovana.gq
resnichkavovana.ml
resnichkavovana.tk
resnichkavovki.cf
resnichkavovki.ga
resnichkavovki.gq
resnichkavovki.ml
resnichkavovki.tk
samaragss.ru
wechkavovana.cf
wechkavovana.ga
wechkavovana.gq
wechkavovana.ml
wechkavovana.tk
wechkavovki.cf
wechkavovki.ga
wechkavovki.gq
wechkavovki.ml
wechkavovki.tk
zalypkavovana.ml
zalypkavovana.tk
zalypkavovki.cf
zalypkavovki.ga
zalypkavovki.gq
zalypkavovki.ml
zalypkavovki.tk
zybikvovana.cf
zybikvovana.ga
zybikvovana.gq
zybikvovana.ml
zybikvovana.tk
zybikvovki.cf
zybikvovki.ga
zybikvovki.gq
zybikvovki.ml
zybikvovki.tk
staffrc.com
stopudof.com
35igr.ru
adandc.ru
avgyst.ru
comedy24.ru
e7ya.ru
funrussia.ru
ladykafe.ru
med-cafe.ru
mykazantip.ru
ohotaforum.ru
powerpoint-ppt.ru
sibledy.ru
turistvip.ru
ya-pisatel.ru
kypitest.ru
anykadavai.tk
forwarditaly.org
getyourimesh.com
mymobi.ml
yellowfrance.org
Sites that are flagged as malware by Google are highlighted and these are all hosted on 184.105.163.243. But what was interesting was what White Falcon Communications have been hosting in the past. When I ran the entirety of all the sites from DNSDB through my checker, I got some interesting results* [csv].
Out of 2867 sites analysed, 1973 (69%) sites had either hosted malware or were spammy. Some of the unrated sites are clearly phishing sites (e.g. usabanksecurity.com). Although these sites are not hosted on White Falcon Communications IPs now, they all have been at some point in the past.
So, who is this outfit? Well, it didn't take to come up with a couple of news stories, firstly this one where White Falcon had been raided by police in Canada in connection with C2 infrastructure for the Citadel botnet. That was followed by this story where White Falcon was allegedly suing law enforcement back, due to alleged "negligence".
However, given the sheer volume of crap that White Falcon has hosted in the past and its current problem with exploit kits, I would definitely recommend blocking traffic to 184.105.163.192/26 to be on the safe side.
* fields are domain name, current IP address, MyWOT ratings, Google Safebrowsing rating, SURBL status.
Labels:
Botnet,
Canada,
Evil Network,
Nuclear EK
Malware spam: "Credit Note CN-60938 from Stilwell Financial Inc" / "message-service@post.xero.com"
This fake financial spam comes with a malicious payload.
In the only sample I saw, the download location for a file at xerofiles.com which came up with a 403 error. This domain belongs to an accounting service called Xero, it is unclear if they were actually hosting the malware or if there is some error in the spam email itself.
Somewhat interestingly, the bad guys have attempted to forge the mail headers to make it looks like it comes from Xero itself.
From: Accounts [message-service@post.xero.com]
To: hp_printer@victimdomain.com
Date: 7 September 2015 at 11:55
Subject: Credit Note CN-60938 from Stilwell Financial Inc for victimdomain.com (0178)
Hi Boris,
To download your credit note CN-60938 for 401.04 GBP please follow the link below : https://get.xerofiles.com/[snip]
This has been allocated against invoice number
If you have any questions, please let us know.
Thanks,
Stilwell Financial Inc
In the only sample I saw, the download location for a file at xerofiles.com which came up with a 403 error. This domain belongs to an accounting service called Xero, it is unclear if they were actually hosting the malware or if there is some error in the spam email itself.
Somewhat interestingly, the bad guys have attempted to forge the mail headers to make it looks like it comes from Xero itself.
Received: from 78.187.120.220.static.ttnet.com.tr (unknown [95.9.34.122])The fake parts of the headers are highlighted. The actual sending IP is 95.9.34.122 in Turkey. I don't know what the payload is in this case as the download location doesn't work, it will most likely be some sort of banking trojan.
by [redacted] (Postfix) with ESMTP id 74F50400BE;
Mon, 7 Sep 2015 11:59:12 +0100 (BST)
Received: from mail2.go.xero.com (198.61.155.105) by
GCN5B9ZDBKTFX.mail.protection.outlook.com (10.997.33.92) with Microsoft SMTP
Server id 05.9.975.7 via Frontend Transport; Mon, 7 Sep 2015 12:55:16 +0200
From: Accounts <message-service@post.xero.com>
To: hp_printer@[redacted]
Date: Mon, 7 Sep 2015 12:55:16 +0200
Subject: Credit Note CN-60938 from Stilwell Financial Inc for [redacted] (0178)
MIME-Version: 1.0
Content-Type: text/plain; charset=ISO-8859-1; format=flowed
Content-Transfer-Encoding: 7bit
X-Mailer: aspNetEmail ver 3.5.2.0
Message-ID: <504359-L45H474JYDT96LCSOCCGF9O9R1IXJTQ2949EW0C2@xero.com>
Malware spam: "Companies House" [WebFiling@companieshouse.gov.uk]
This spam does not come from Companies House, but is instead a simple forgery with a malicious attachment:
The "case number" is random, and is reflected in the name of the attachment (in this case Case_0676414.zip) which in turn contains a malicious executable Case_0043258.scr which has an icon to make it look like a PDF file.
This executable has a detection rate of 4/56. The Hybrid Analysis report shows that it communicates with 197.149.90.166 (Cobranet, Nigeria) which has been seen handling malicious traffic for the past couple of weeks. The payload is Upatre/Dyre.
MD5:
f1d62047d22f352a14fe6dc0934be3bb
From "Companies House" [WebFiling@companieshouse.gov.uk]
Date Mon, 7 Sep 2015 12:40:01 +0100
Subject RE: Case 0676414
The submission number is: 0676414
For more details please check attached file.
Please quote this number in any communications with Companies House.
All Web Filed documents are available to view / download for 10 days after their
original submission. However it is not possible to view copies of accounts that
were downloaded as templates.
Companies House Executive Agency may use information it holds to prevent
and detect fraud. We may also share such information, for the same purpose,
with other Organizations that handle public funds.
If you have any queries please contact the Companies House Contact Centre
on +44 (0)303 1234 500 or email enquiries@companies-house.gov.uK
Note: This email was sent from a notification-only email address which cannot
accept incoming email. Please do not reply directly to this message.
Companies House
4 Abbey Orchard Street
Westminster
London
SW1P 2HT
Tel +44 (0)303 1234 500
The "case number" is random, and is reflected in the name of the attachment (in this case Case_0676414.zip) which in turn contains a malicious executable Case_0043258.scr which has an icon to make it look like a PDF file.
This executable has a detection rate of 4/56. The Hybrid Analysis report shows that it communicates with 197.149.90.166 (Cobranet, Nigeria) which has been seen handling malicious traffic for the past couple of weeks. The payload is Upatre/Dyre.
MD5:
f1d62047d22f352a14fe6dc0934be3bb
Friday 4 September 2015
Malware spam: "RE:resume" aka "What happened to your files?" / Cryptowall 3.0
This fake résumé spam leads to ransomware:
The Hybrid Analysis report shows pretty clearly what is going on. An infection sequence begins, with the following domains and IPs contacted:
46.30.46.117 [Eurobyte LLC, Russia)
186.202.153.84 (gaiga.net)
192.186.235.39 (satisgoswamicollege.org)
52.88.9.255 (entriflex.com)
23.229.143.32 (eliasgreencondo.com)
Blocking those domains and IPs may be enough to stop the ransomware working. The malicious macro in the document drops a file carved_0.exe which has a detection rate of 4/56.
Once the machine is infected, various "What happened to your files?" messages pop up, such as this one (from the Hybrid Analysis report)
This further references another bunch of domains that you might want to block, especially in a corporate environment:
namepospay.com
optiontosolutionbbs.com
optionpay2all.com
democraticash.com
This further Hybrid Analysis report on the dropped binary also identifies the following malicious site:
68.178.254.208 (erointernet.com)
Incidentally, it is worth noting that the malware attempts to identify the IP address of the infected system by visiting ip-addr.es - although this is not a malcious site, you can consider it to be a potential indicator of compromise.
The payload here is Cryptowall 3.0 and as is typical, removing the malware is easy.. but decrypting the files without paying the ransom is fearsomely difficult.
Recommended blocklist:
46.30.46.0/24
gaiga.net
satisgoswamicollege.org
entriflex.com
eliasgreencondo.com
erointernet.com
namepospay.com
optiontosolutionbbs.com
optionpay2all.com
democraticash.com
MD5s:
d6b3573944a4b400d6e220aabf0296ec
5b311508910797c91cc9c9eb4b4edb0c
From: fredrickkroncke@yahoo.comThe attached document in this case is Teresa_Alexander_resume.doc, which upon opening asks you to enable active content:
Date: 5 September 2015 at 03:50
Subject: RE:resume
Signed by: yahoo.com
Hi my name is Teresa Alexander attach is my resume
Awaiting your prompt reply
Kind regards
Teresa Alexander
Protected DocumentFollowing these steps would be a Very Bad Idea as the malware would encrypt all your files on the disk. This malicious DOC file itself has a VirusTotal detection rate of 4/56.
This document is protected by Microsoft Office.
Please enable Editing and Content to see this document.
Can’t view? Follow the steps below.
Open the document in Microsoft Office. Previewing online does not work for protected documents.
If you downloaded this document from your email, please click “Enable Editing” from the yellow bar above.
Once you have enabled editing, please hit “Enable Content” on the yellow bar above.
The Hybrid Analysis report shows pretty clearly what is going on. An infection sequence begins, with the following domains and IPs contacted:
46.30.46.117 [Eurobyte LLC, Russia)
186.202.153.84 (gaiga.net)
192.186.235.39 (satisgoswamicollege.org)
52.88.9.255 (entriflex.com)
23.229.143.32 (eliasgreencondo.com)
Blocking those domains and IPs may be enough to stop the ransomware working. The malicious macro in the document drops a file carved_0.exe which has a detection rate of 4/56.
Once the machine is infected, various "What happened to your files?" messages pop up, such as this one (from the Hybrid Analysis report)
This further references another bunch of domains that you might want to block, especially in a corporate environment:
namepospay.com
optiontosolutionbbs.com
optionpay2all.com
democraticash.com
This further Hybrid Analysis report on the dropped binary also identifies the following malicious site:
68.178.254.208 (erointernet.com)
Incidentally, it is worth noting that the malware attempts to identify the IP address of the infected system by visiting ip-addr.es - although this is not a malcious site, you can consider it to be a potential indicator of compromise.
The payload here is Cryptowall 3.0 and as is typical, removing the malware is easy.. but decrypting the files without paying the ransom is fearsomely difficult.
Recommended blocklist:
46.30.46.0/24
gaiga.net
satisgoswamicollege.org
entriflex.com
eliasgreencondo.com
erointernet.com
namepospay.com
optiontosolutionbbs.com
optionpay2all.com
democraticash.com
MD5s:
d6b3573944a4b400d6e220aabf0296ec
5b311508910797c91cc9c9eb4b4edb0c
Tuesday 1 September 2015
Malware spam: "Complaint of your Internet activity"
This spam comes with a malicious attachment:
This Hybrid Analysis report shows it to be just another variant of Update / Dyre with the same characteristics as the malspam seen earlier today, sending traffic to an IP that I suggest you block or monitor:
197.149.90.166 (Cobranet, Nigeria)
Some other subjects spotted include:
Complaint notification 50646
Infringement of your Internet activity
Infringement notification 51494
From: Margret KuhicAll the sames I have seen have a corrupt attachment which is Base 64 encoded, it is possible that other people might receive a valid attachment though. The attachment was meant to be 723296788_Marquardt-Bailey_Margret Kuhic.zip containing the malicious executable june_stiedemannmolestiae.et.exe which has a VirusTotal detection rate of 2/56.
Date: 1 September 2015 at 16:10
Subject: Complaint of your Internet activity
This is a complaint notification. Full details attached. Please notify us within 24 hours with taken actions.
Margret Kuhic
Dynamic Communications Agent
T: 1-679-732-5379
F: 100.173.9045
This Hybrid Analysis report shows it to be just another variant of Update / Dyre with the same characteristics as the malspam seen earlier today, sending traffic to an IP that I suggest you block or monitor:
197.149.90.166 (Cobranet, Nigeria)
Some other subjects spotted include:
Complaint notification 50646
Infringement of your Internet activity
Infringement notification 51494
Malware spam: "Private message notification 41447" / "Adrien Abbott"
This spam comes with a malicious attachment:
197.149.90.166 (Cobranet, Nigeria)
..which is an IP that has been used several time for this sort of attack recently and is worth blocking. The report details other IP addresses too, but this seems to be the key one to block or monitor.
MD5:
7c94abe2e3b60f8a72b7358d50d04ee0
From: Adrien AbbottI have only seen a single sample of this spam, and the attachment was not formatted properly making it harmless, however other variants could be more dangerous. If properly decoded, the attachment should have been named 89867740_Torphy and Sons_Adrien Abbott.zip containing a malicious executable jodie_okonofficia-quo.exe. This executable has a VirusTotal detection rate of just 2/56, the Hybrid Analysis report shows network activity consistent with this being Upatre dropping the Dyre banking trojan, with communications made to:
Date: 1 September 2015 at 12:34
Subject: Private message notification 41447
You've received a private message. Please open the attached to view it.
Adrien Abbott
Chief Tactics Executive
home: 1-583-761-3793
work: 380.022.2492
twitter: @nicole
skype: nicole
messenger: nicole
197.149.90.166 (Cobranet, Nigeria)
..which is an IP that has been used several time for this sort of attack recently and is worth blocking. The report details other IP addresses too, but this seems to be the key one to block or monitor.
MD5:
7c94abe2e3b60f8a72b7358d50d04ee0
Sunday 30 August 2015
WARNING: projectmanagementinternational.org / "Project Management International" aka Patty Jones and Anthony Christopher Jones
"Project Management International" (projectmanagementinternational.org) appears to be another website run by Patty Jones (aka Patchree Patchrint) and Anthony Christopher Jones of California.
These so-called training courses run by the Joneses are promoted through spam and have a terrible reputation. One BBB report for a previous incarnation of this scheme sums up many of the complaints that I have seen:
On to this particular scheme called "Project Management International" which should not be confused with many reputable organisations of a similar name, using the domain projectmanagementinternational.org which just frames another site at ipmam862026.sitebuilder.name.com. The "ipma" part of the name is significant as I will mention later. The site is promoted through spam email such as the one found here:
The site is generic looking but fairly smart:
It lists some upcoming courses:
The domain was registered on May 20th 2015 to an anonymous registrant. The site itself lists no contact details on the Contact page:
It appears to be using an email address of "info@projectmanagementinternational.org" for correspondence, but a look at the underlying HTML tells a different story:
The "About Project Management page" features some generic text about Project Management:
The text is almost identical to the defunct website Institute of Program Management America (IPMA) that I mentioned last year. If you remember, this new website also uses "IPMA" in its underlying URL (ipmam862026.sitebuilder.name.com) which also links the two schemes. A RipOffReport for IPMA also shows the same pattern as before.
There is little doubt that this is the same scheme as mentioned in all my previous posts on the activities of Jones and Patchrint. My personal recommendation is that you give this "Project Management International" a very wide berth, and if you feel that you have been defrauded then you would be doing a lot of people a favour if your pursued them aggressively. Also, if you have any positive (or negative) experiences then sharing them in the Comments would be appreciated.
These so-called training courses run by the Joneses are promoted through spam and have a terrible reputation. One BBB report for a previous incarnation of this scheme sums up many of the complaints that I have seen:
Grant Funding USA advertised a 3-day grant writing workshop for non-profit professionals to be held November 12-14 at the Georgetown Law School campus in Washington DC. The course was described as an overview of the grant writing process and concluding with a certificate in professional grant writing. The cost was $495. My organization paid the fee, I received a confirmation email. I received a credit card authorization letter requesting authorization; we completed and submitted it. I spoke with an individual over the phone confirming my registration. I received a registration packet (about 15 pages) with suggestions for preparation and materials to bring to the course. On the first day, November 12, I arrived at Georgetown Law at 8 AM. The guard was unaware of our course and was working on figuring out where we needed to be (there were 7 other students). After about 45 minutes, we all received an email from the organization Grant Funding USA that said our instructor had fallen ill and they were working on securing a substitute instructor to start the class by the afternoon.At 1pm, we received an email from the same email address saying that they were unable to secure a substitute for Wednesday, but class would begin promptly at 8am on Thursday. I called the number for the organization multiple times and continually got their voicemail. On Thursday, November 13 at 8AM, I arrived at Georgetown again, and found the other students in the lobby upset and confused. The guard was unaware of the course and said he had no information for us. He directed me to the Georgetown Student Life office (who would have been responsible for securing the space). They informed me that Georgetown has never heard of Grant Funding USA nor has a relationship with them. There was no workshop scheduled to be held on their campus. Grant Funding USA has not answered my numerous calls or emails. Other participants fooled by this scam were from Smithsonian Institute and State Gov't of New Jersey.This story seems to be echoed over and over again. A venue is booked at a prestigious location, but changed at the last minute. The person taking the course very often seems to be ill and doesn't turn up. Sometimes an ill-prepared substitute teacher is found, but has difficulty being paid. Calls to the so-called institute are either not answered or met with hostility. Read the comments for more stories such as this.
On to this particular scheme called "Project Management International" which should not be confused with many reputable organisations of a similar name, using the domain projectmanagementinternational.org which just frames another site at ipmam862026.sitebuilder.name.com. The "ipma" part of the name is significant as I will mention later. The site is promoted through spam email such as the one found here:
Project Management Certification Course (July 28-31, 2015: University of Southern California)
The Project Management Certification Course will be offered July 28 - 31, 2015 at the University of Southern California in Los Angeles, CA . Project management professionals, business and technology professionals, students, and educators are invited to register at the Project Management International website here .
July 28 - 31, 2015
University of Southern California
Los Angeles, California
The PMCC is designed for those seeking professional project management certification. It serves as both a thorough professional education and recognized certification. Those seeking additional credentials such as the PMP®/PgMP®, PMI-SP®, and PMI-RMP® will benefit from this dynamic and interactive work session, while those currently holding credentials will find the certification to be an enhancement as well as the most up to date advanced professional development.
Project Management Masters Certification program provides 36 hours of project management education, meeting education requirements for both PMI's Certified Associate in Project Management (CAPM) ® and Project Management Professional (PMP) certifications. Additionally, the Master Certification provides 36 Professional Development Units (PDUs) for current holders of PMP®/PgMP®, PMI-SP®, and PMI-RMP® credentials.
The program meets the education requirement for all professional designations through the Project Management Institute and other professional agencies. Additionally, the program awards 3.6 Continuing Education Units (CEUs) upon request.
Program Description
Our certificate program teaches technical and business professionals how to master the critical skills of project management techniques as part of their technical career development.
The skills developed in the Project Management Masters Certification program apply to large and small projects, product design and development efforts, construction projects, IT projects, software development, and any project with critical performance, time, and budget targets.
Our approach to project management education offers proven, results-focused learning.
Courses are developed and facilitated by professional subject experts with extensive industrial experience. Course emphasis is on providing practical skills and tools supported by relevant case examples.
Tuition
Tuition for the four-day Project Management Certification Course is $995.00
Program Schedule and Content
1. Project Initiation, Costing, and Selection, Day 1
2. Project Organization and Leadership, Day 2
3. Detailed Project Planning, Day 2 and 3
4. Project Monitoring and Control, Day 3 and 4
5. Project Risk and Stakeholder Management, Day 4
Benefits
· A Project Management International Certificate of Accomplishment is awarded upon completion of the four day program of five courses. Completion letters are given for each course.
· Our instructors have extensive industrial experience. They focus on providing you with practical skills and tools using relevant case examples.
· Each class is highly focused and promotes maximum interaction.
· You can network with other project management professionals from a variety of industries.
· Earn Professional Development Units (PDUs) for maintenance of certification under the PMI Continuing Certification Requirements Program.
· Applicants for PMI's Certified Associate in Project Management (CAPM)® and Project Management Professional (PMP) certifications will have met all education requirements for eligibility.
Registration
Participants may reserve a seat online at the Project Management International website, by calling the Program Office toll-free at (800) 288-8387, or by sending their name and contact information via email to the Program Registrar .
Upon receiving your registration, a confirmation email is sent to registrants that include session site information, travel information, program description, and details on how to confirm attendance and make payment arrangements.
To unsubscribe from this mailing list, simply reply to this message and write EXCLUDE to be removed from future notices.
The site is generic looking but fairly smart:
It lists some upcoming courses:
August 25 - 28, 2015: University of Houston
September 22- 25, 2015: University of Miami
October 6-9, 2015: University of Southern California
The domain was registered on May 20th 2015 to an anonymous registrant. The site itself lists no contact details on the Contact page:
It appears to be using an email address of "info@projectmanagementinternational.org" for correspondence, but a look at the underlying HTML tells a different story:
<h4> If you have any additional questions, simply email us directly at <a href="mailto:info@grantfundingusa.org?subject=ContactUS"> </a> <a href="mailto:grantfundingusa@gmail.com?subject=Contact+Us" target="_self" title="info@thefundinginstitute.org">info@projectmanagementinternational.org </a> and our coordinators will respond to you directly. </h4>The underlying code references both info@grantfundingusa.org and grantfundingusa@gmail.com (the organisation mentioned in the BBB report I mentioned earlier) and which is the same site I warned about a year ago. The only other contact details on the site are a telephone number of 800-288-8387.
The "About Project Management page" features some generic text about Project Management:
The text is almost identical to the defunct website Institute of Program Management America (IPMA) that I mentioned last year. If you remember, this new website also uses "IPMA" in its underlying URL (ipmam862026.sitebuilder.name.com) which also links the two schemes. A RipOffReport for IPMA also shows the same pattern as before.
There is little doubt that this is the same scheme as mentioned in all my previous posts on the activities of Jones and Patchrint. My personal recommendation is that you give this "Project Management International" a very wide berth, and if you feel that you have been defrauded then you would be doing a lot of people a favour if your pursued them aggressively. Also, if you have any positive (or negative) experiences then sharing them in the Comments would be appreciated.
Thursday 27 August 2015
Malware spam: "Payslip for period end date 27/08/2015" / "noreply@fermanagh.gov.uk"
This spam does not come from Fermanagh District Council. Of course it doesn't. It is instead a simple forgery with a malicious attachment:
Attached is a file payroll.zip which contains a malicious executable payroll.scr - or it would have done, but in my case the email was malformed and the archive was not attached properly.
This executable has a detection rate of 3/56 and the Hybrid Analysis report indicates that it sends traffic to a server at 197.149.90.166 (Cobranet, Nigeria) which has been used in a few recent attacks and is definitely worth blocking.
MD5:
fdea30868df48bff9e7c2b2605431d23
From: noreply@fermanagh.gov.uk [noreply@fermanagh.gov.uk]
Date: 27 August 2015 at 12:28
Subject: Payslip for period end date 27/08/2015
Dear administrator
Please find attached your payslip for period end 27/08/2015
Payroll Section
Attached is a file payroll.zip which contains a malicious executable payroll.scr - or it would have done, but in my case the email was malformed and the archive was not attached properly.
This executable has a detection rate of 3/56 and the Hybrid Analysis report indicates that it sends traffic to a server at 197.149.90.166 (Cobranet, Nigeria) which has been used in a few recent attacks and is definitely worth blocking.
MD5:
fdea30868df48bff9e7c2b2605431d23
Wednesday 26 August 2015
Malware spam: "RE:resume" leads to Cryptowall
This fake resume spam has a malicious payload. I got part way through decrypting it to discover that @Techhelplistcom had done all the hard bits which saved me some effort. This particular spam delivers a version of the Cryptowall ransomware.
In the only sample I saw, the spam looks like this:
The format of this message is very similar to this other fake resume spam seen recently, and a key feature here is that the message is really sent through Yahoo! and is not a forgery.
Deobfuscating the macro shows that a file is downloaded from http://46.30.46.60/444.jpg which is then run through a decoding mechanism to create (I think) %APPDATA%\278721985.exe. The Hybrid Analysis report shows some of this in action, but Techhelplist did the hard work of decrypting it..
To save a bit of time, a helpful soul left a note on the VT scan of the fake JPEG which leads to this VT report on the actual executable itself, and this then leads to this rather informative Hybrid Analysis report which has some nice screenshots.
Out of all the IPs and domains listed in those reports, I think these are probably the priorities to block:
46.30.46.60 (Eurobyte, Russia)
linecellardemo.net / 23.229.194.224 (GoDaddy, US)
You might want to block the entire 46.30.46.0/24 range because.. well, Russia really.
MD5s:
41177ea4a2c88a2b0d320219389ce27d
d1e23b09bb8f5c53c9e4d01f66db3654
In the only sample I saw, the spam looks like this:
From: emmetrutzmoser@yahoo.comAttached was a file Janet_Ronald_resume.doc [VT 5/56] which (of course) contains a malicious macro that looks like this [pastebin].
To:
Date: 26 August 2015 at 23:29
Subject: RE:resume
Signed by: yahoo.com
Hi! my name is Janet Ronald it is my resume!Awaiting your prompt reply
Best regards
Janet Ronald
The format of this message is very similar to this other fake resume spam seen recently, and a key feature here is that the message is really sent through Yahoo! and is not a forgery.
Deobfuscating the macro shows that a file is downloaded from http://46.30.46.60/444.jpg which is then run through a decoding mechanism to create (I think) %APPDATA%\278721985.exe. The Hybrid Analysis report shows some of this in action, but Techhelplist did the hard work of decrypting it..
To save a bit of time, a helpful soul left a note on the VT scan of the fake JPEG which leads to this VT report on the actual executable itself, and this then leads to this rather informative Hybrid Analysis report which has some nice screenshots.
Out of all the IPs and domains listed in those reports, I think these are probably the priorities to block:
46.30.46.60 (Eurobyte, Russia)
linecellardemo.net / 23.229.194.224 (GoDaddy, US)
You might want to block the entire 46.30.46.0/24 range because.. well, Russia really.
MD5s:
41177ea4a2c88a2b0d320219389ce27d
d1e23b09bb8f5c53c9e4d01f66db3654
Fake fax spam spoofs multiple senders, has malicious payload
This fake fax spam comes from random senders - company names and attachment names vary from spam to spam.
The Hybrid Analysis report shows it phoning home to:
197.149.90.166/260822U/Yd1D3h1R87/0/61-SP1/0/FDMBEFJBMKBEMM
197.149.90.166/260822U/Yd1D3h1R87/41/5/42/FDMBEFJBMKBEMM
This pattern marks the malware out as being Upatre/Dyre. 197.149.90.166 is an IP address belonging to Cobranet in Nigeria which was also used in a similar attack yesterday.
From: "Heaney, Vandervort and Hilll"Attached is a ZIP file combining various elements from the spam (for example, in this case it was fax_AhnxlQ8_Heaney, Vandervort and Hilll_Donny Kub.zip). This contains a malicious executable (e.g. Invoice Lake Janeview.exe) which currently has a 2/56 detection rate at VirusTotal.
Subject: Fax #AhnxlQ8 from Donny Kub
Date: Wed, 26 Aug 2015 14:02:30 +0000
You have a fax.
Data sent: Wed, 26 Aug 2015 14:03:30 +0000
TO: info@victimdomain.com
*********************************
We are a new fax delivery service - Heaney, Vandervort and Hilll.
Our company develops rapidly and services remain fastest and open to everyone.
As our slogan goes: "Fast. Cheap. Best quality."
*********************************
The Hybrid Analysis report shows it phoning home to:
197.149.90.166/260822U/Yd1D3h1R87/0/61-SP1/0/FDMBEFJBMKBEMM
197.149.90.166/260822U/Yd1D3h1R87/41/5/42/FDMBEFJBMKBEMM
This pattern marks the malware out as being Upatre/Dyre. 197.149.90.166 is an IP address belonging to Cobranet in Nigeria which was also used in a similar attack yesterday.
Malware spam: "Scanned image from MX-2600N" / "noreply@victimdomain.com"
NOTE: As of December 2015 there is an updated version of this spam run.
This spam is not from a scanner, but it is instead a simple forgery with a malicious attachment:
http://fotolagi.com/45ygege/097uj.exe
http://asterixpr.republika.pl/45ygege/097uj.exe
http://detocoffee.ojiji.net/45ygege/097uj.exe
This malicious binary currently has a VirusTotal detection rate of just 2/54. Automated analysis [1] [2] shows network traffic to 91.239.232.9 (Hostpro Ltd, Ukraine) which has been used in serveral attacks recently. The payload is almost definitely the Dridex banking trojan.
This spam is not from a scanner, but it is instead a simple forgery with a malicious attachment:
From: noreply@victimdomain.comThe email appears to come from the victim's own domain, but it does not. The "From" address on email is extremely easy to forge. So far I have seen three different malicious attachments, each one in the format noreply@victimdomain.com_20150826_181106.doc with detection rates of around 7/56 [1] [2] [3] containing one of three malicious macros [1] [2] [3] which attempt to download a malicious component from one of the following locations:
Reply-To: noreply@victimdomain.com
To: victim@victimdomain.com
Date: 19 May 2014 at 18:11
Subject: Scanned image from MX-2600N
Reply to: noreply@victimdomain.com [noreply@victimdomain.com]
Device Name: Not Set
Device Model: MX-2600N
Location: Not Set
File Format: DOC MMR(G4)
Resolution: 200dpi x 200dpi
Attached file is scanned image in DOC format.
Use Microsoft(R)Word(R) of Microsoft Systems Incorporated
to view the document.
http://fotolagi.com/45ygege/097uj.exe
http://asterixpr.republika.pl/45ygege/097uj.exe
http://detocoffee.ojiji.net/45ygege/097uj.exe
This malicious binary currently has a VirusTotal detection rate of just 2/54. Automated analysis [1] [2] shows network traffic to 91.239.232.9 (Hostpro Ltd, Ukraine) which has been used in serveral attacks recently. The payload is almost definitely the Dridex banking trojan.
Tuesday 25 August 2015
Malware spam: "Invoice 26949 from I - SPI Ltd" / "sales@ispitrade.com"
My spam traps did not collect the body text from this message, so all I have is headers. However, this fake financial email is not from i-Spi Ltd and is instead a simple forgery with a malicious attachment:
http://landrevie.g.free.fr/45gf3/7uf3ref.exe
http://e-projekt.ns1.internetdsl.pl/45gf3/7uf3ref.exe
http://nathalieetalain.free.fr/45gf3/7uf3ref.exe
http://claudio.locatelli.free.fr/45gf3/7uf3ref.exe
http://spitlame.free.fr/45gf3/7uf3ref.exe
http://nathalieetalain.free.fr/45gf3/7uf3ref.exe
This Hybrid Analysis report shows network traffic to:
91.239.232.9 (Hostpro Ltd, Ukraine)
This is the same bad IP as found in this earlier spam run, I recommend that you block it. The payload here is almost definitely the Dridex banking trojan.
From [sales@ispitrade.com]Attached is a file Inv_26949_from_I__SPI_Ltd_7888.doc which actually comes in several different versions [1] [2] [3] [4] [5] [6] which contains a malicious macro like this one [pastebin] that downloads an executable from one of the following locations:
Date Tue, 25 Aug 2015 20:37:09 +0800
Subject Invoice 26949 from I - SPI Ltd
http://landrevie.g.free.fr/45gf3/7uf3ref.exe
http://e-projekt.ns1.internetdsl.pl/45gf3/7uf3ref.exe
http://nathalieetalain.free.fr/45gf3/7uf3ref.exe
http://claudio.locatelli.free.fr/45gf3/7uf3ref.exe
http://spitlame.free.fr/45gf3/7uf3ref.exe
http://nathalieetalain.free.fr/45gf3/7uf3ref.exe
This Hybrid Analysis report shows network traffic to:
91.239.232.9 (Hostpro Ltd, Ukraine)
This is the same bad IP as found in this earlier spam run, I recommend that you block it. The payload here is almost definitely the Dridex banking trojan.
Malware spam: "UPDATE_VACATIONS_SCHEDULE_09_2015.pdf" via sugarsync.com
This fake Dropbox email leads to malware, hosted on the sharing service sugarsync.com.
https://www.sugarsync.com/pf/D3941255_827_052066225?directDownload=true
https://www.sugarsync.com/pf/D160756_82_6104120627?directDownload=true
https://www.sugarsync.com/pf/D2694666_265_638165437?directDownload=true
In each case, the binary downloaded is identical and has a VirusTotal detection rate of 3/55. Analysis is pending, but the payload appears to be the Dyre banking trojan.
UPDATE:
The Hybrid Analysis report shows traffic to 197.149.90.166 (Cobranet, Nigeria) which I recommend you block.
From: June Abel via Dropbox [no-reply@dropbox.com]I have seen three different samples with different download location:
Date: 25 August 2015 at 12:59
Subject: June Abel shared "UPDATE_VACATIONS_SCHEDULE_09_2015.pdf" with you
June used Dropbox to share a file with you!
Click here to download.
© 2015 Dropbox
https://www.sugarsync.com/pf/D3941255_827_052066225?directDownload=true
https://www.sugarsync.com/pf/D160756_82_6104120627?directDownload=true
https://www.sugarsync.com/pf/D2694666_265_638165437?directDownload=true
In each case, the binary downloaded is identical and has a VirusTotal detection rate of 3/55. Analysis is pending, but the payload appears to be the Dyre banking trojan.
UPDATE:
The Hybrid Analysis report shows traffic to 197.149.90.166 (Cobranet, Nigeria) which I recommend you block.
Malware spam: "Visa Card Aug 2015" / "david@ellesmere.engineering"
This fake financial spam does not come from Ellesemere Engineering but is in fact a simple forgery with a malicious attachment.
Attached is a document Visa Card Aug 2015.docm which I have seen in three different versions, containing one of three malicious macros [1] [2] [3] that then attempt to download a malicious binary from one of the following locations:
http://e-projekt.ns1.internetdsl.pl/45gf3/7uf3ref.exe
http://nathalieetalain.free.fr/45gf3/7uf3ref.exe
http://landrevie.g.free.fr/45gf3/7uf3ref.exe
This executable has a detection rate of just 1/55 and the Malwr report shows network traffic to:
91.239.232.9 (Hostpro Ltd, Ukraine)
I strongly recommend that you block that IP address. The payload to this is almost definitely the Dridex banking trojan.
MD5s:
c1a8edf0ea4e5b35826cdf9afdb35c94
2ef4032a000b8a5da438175302e525a4
9d98b19e6f5ea4dc883df7b3053bbfe2
25578c66ef3da0734fc3f88f89f59773
From [david@ellesmere.engineering]
To "'Sharon Howarth'" [sharon@ellesmere.engineering]
Date Tue, 25 Aug 2015 09:52:47 +0200
Subject Visa Card Aug 2015
Visa Card payments this month
---
This email has been checked for viruses by Avast antivirus software.
https://www.avast.com/antivirus
Attached is a document Visa Card Aug 2015.docm which I have seen in three different versions, containing one of three malicious macros [1] [2] [3] that then attempt to download a malicious binary from one of the following locations:
http://e-projekt.ns1.internetdsl.pl/45gf3/7uf3ref.exe
http://nathalieetalain.free.fr/45gf3/7uf3ref.exe
http://landrevie.g.free.fr/45gf3/7uf3ref.exe
This executable has a detection rate of just 1/55 and the Malwr report shows network traffic to:
91.239.232.9 (Hostpro Ltd, Ukraine)
I strongly recommend that you block that IP address. The payload to this is almost definitely the Dridex banking trojan.
MD5s:
c1a8edf0ea4e5b35826cdf9afdb35c94
2ef4032a000b8a5da438175302e525a4
9d98b19e6f5ea4dc883df7b3053bbfe2
25578c66ef3da0734fc3f88f89f59773
Monday 24 August 2015
Popular German wesite dwdl.de hacked, serving malware via 94.142.140.222
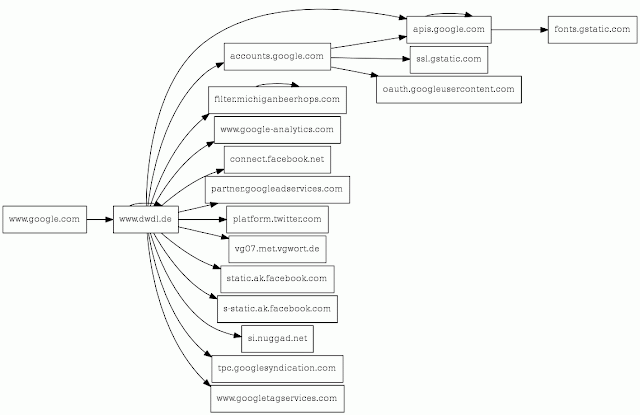
Popular German media website dwdl.de has been hacked and is serving up malware, according to this URLquery report.
URLquery's IDS function detects what looks like the RIG Exploit kit:
The exploit is in injected code pointing to a server at 94.142.140.222 (Marosnet Telecommunication Company, Russia) which in the example is using filter.michiganbeerhops.com which is a hijacked GoDaddy domain.
The exploit only appears to work if the site is accessed via a search engine, which looks like a classic .htaccess hack. URLquery's script relationship chart shows this in action:
VirusTotal gives an overview of other malicious domains on this server. It indicates that the following domains have been hijacked and malicious subdomains set up:
123goled.com
123gooled.com
123homeautomation.com
123oled.com
135warranty.com
1drones.com
4ktechsupport.com
audiovideoalternatives.com
audiovideoinsight.com
autonomouscontrolsystem.com
autonomouscontrolsystems.com
autonomousinterface.com
avioav.com
birminghamaudiovideo.com
birminghamtheatercompany.com
birminghamtheatersystems.com
cleanlittleengine.com
cleanpowercell.com
cleansunpower.com
clearviewelectronic.com
clearviewelectronic.net
clearviewelectronics.info
clearviewelectronics.me
clearviewelectronics.net
clearviewelectronics.org
crazyoled.com
daddybeer.com
devilscrotchhotsauce.com
dreamybikini.com
educationdrone.com
efgled.com
energeticled.com
ferndalebar.com
hometheaterlogistics.com
hopsmichigan.com
imagerled.com
inwallsoundbar.com
ledgest.com
ledimager.com
ledisme.com
ledrefill.com
ledrequired.com
ledstuf.com
lightsusingled.com
michiganbeerhops.com
timeandplacephotos.com
torredelpainelandscapes.com
travelersvisions.com
travelerviews.net
travelervisions.com
travelervisions.net
triadthinking.com
turkeylight.com
turkishlandscapes.com
tuscanycolor.com
understandinglight.com
urbanchina.info
veniciancolor.com
venicianlight.com
viewartsandsciences.com
viewevolution.com
viewevolution.net
viewevolution.org
viewhumanities.com
viewliberalarts.com
viewnaturalsciences.com
viewprocess.org
viewsocialsciences.com
visionandthought.com
visioningmind.com
visioningmind.net
visioningplace.com
visioningplace.net
visionofchina.net
visionofchina.org
visquest.info
visualcreativethinking.com
visualcreativethinking.net
visualcreativity.info
visualizationfuture.com
visualizationthinking.com
visualizingmaps.net
visualknowledge.org
visualmexico.net
vizmodeling.com
vizmodels.com
vizsee.com
vizthought.com
volgadeutsch.com
wallartbycountry.com
wayfindingadventure.com
wayfindingtravel.com
waysofthinking.com
waysofthinking.net
waystosee.net
webviews.info
westerneuropelandscapes.com
wilkiephotos.com
worldwallart.com
worldwallart.net
xianspirit.com
yunnanlandscapes.com
yunnanlight.com
zocaloscenes.com
URLquery's IDS function detects what looks like the RIG Exploit kit:
The exploit is in injected code pointing to a server at 94.142.140.222 (Marosnet Telecommunication Company, Russia) which in the example is using filter.michiganbeerhops.com which is a hijacked GoDaddy domain.
The exploit only appears to work if the site is accessed via a search engine, which looks like a classic .htaccess hack. URLquery's script relationship chart shows this in action:
VirusTotal gives an overview of other malicious domains on this server. It indicates that the following domains have been hijacked and malicious subdomains set up:
123goled.com
123gooled.com
123homeautomation.com
123oled.com
135warranty.com
1drones.com
4ktechsupport.com
audiovideoalternatives.com
audiovideoinsight.com
autonomouscontrolsystem.com
autonomouscontrolsystems.com
autonomousinterface.com
avioav.com
birminghamaudiovideo.com
birminghamtheatercompany.com
birminghamtheatersystems.com
cleanlittleengine.com
cleanpowercell.com
cleansunpower.com
clearviewelectronic.com
clearviewelectronic.net
clearviewelectronics.info
clearviewelectronics.me
clearviewelectronics.net
clearviewelectronics.org
crazyoled.com
daddybeer.com
devilscrotchhotsauce.com
dreamybikini.com
educationdrone.com
efgled.com
energeticled.com
ferndalebar.com
hometheaterlogistics.com
hopsmichigan.com
imagerled.com
inwallsoundbar.com
ledgest.com
ledimager.com
ledisme.com
ledrefill.com
ledrequired.com
ledstuf.com
lightsusingled.com
michiganbeerhops.com
timeandplacephotos.com
torredelpainelandscapes.com
travelersvisions.com
travelerviews.net
travelervisions.com
travelervisions.net
triadthinking.com
turkeylight.com
turkishlandscapes.com
tuscanycolor.com
understandinglight.com
urbanchina.info
veniciancolor.com
venicianlight.com
viewartsandsciences.com
viewevolution.com
viewevolution.net
viewevolution.org
viewhumanities.com
viewliberalarts.com
viewnaturalsciences.com
viewprocess.org
viewsocialsciences.com
visionandthought.com
visioningmind.com
visioningmind.net
visioningplace.com
visioningplace.net
visionofchina.net
visionofchina.org
visquest.info
visualcreativethinking.com
visualcreativethinking.net
visualcreativity.info
visualizationfuture.com
visualizationthinking.com
visualizingmaps.net
visualknowledge.org
visualmexico.net
vizmodeling.com
vizmodels.com
vizsee.com
vizthought.com
volgadeutsch.com
wallartbycountry.com
wayfindingadventure.com
wayfindingtravel.com
waysofthinking.com
waysofthinking.net
waystosee.net
webviews.info
westerneuropelandscapes.com
wilkiephotos.com
worldwallart.com
worldwallart.net
xianspirit.com
yunnanlandscapes.com
yunnanlight.com
zocaloscenes.com
Labels:
Germany,
GoDaddy,
Hacked sites,
Russia
Malware spam: "Message from scanner" / "scanner.coventrycitycentre@brianholt.co.uk"
I don't have the body text for this particular message, but I can tell you this is not from Brian Holt (a property agent in Coventry, UK) but is instead a simple forgery with a malicious attachment.
To show the level of detail the bad guys go to, they have even included extra mail headers (usually hidden) to attempt to identify the sender as a Konica MFD. It's a strange thing to do, considering that anyone skilled enough to examine the mail headers should also notice the malicious executable Sscanner15081208190.exe embedded into the attachment Sscanner15081208190.zip . This executable has a detection rate of just 5/54.
The Hybrid Analysis report shows the malware POSTing to:
smboy.su/mu/tasks.php
.SU (Soviet Union) domains are almost always bad news. If you can block them on your web filter then I recommend that you do so. This particular site is hosted on 95.172.146.73 (RTComm-Sibir, Russia). The network range of 95.172.146.0/23 does seem to contain some legitimate Russian-language sites, but you might want to block the whole range to be on the safe side.
The payload is unknown, but typically malware like this will drop either the Dyre banking trojan or some sort of ransomware.
Subject Message from scanner
From scanner.coventrycitycentre@brianholt.co.uk
X-Mailer KONICA MINOLTA bizhub C360
Date Wed, 12 Aug 2015 08:19:28 +0000
Message-Id [55CB0190.015.00206B68D2CD.scanner.coventrycitycentre@brianholt.co.uk]
MIME-Version 1.0
Content-Type multipart/mixed; boundary="KONICA_MINOLTA_Internet_Fax_Boundary"
Content-Transfer-Encoding 7bit
To show the level of detail the bad guys go to, they have even included extra mail headers (usually hidden) to attempt to identify the sender as a Konica MFD. It's a strange thing to do, considering that anyone skilled enough to examine the mail headers should also notice the malicious executable Sscanner15081208190.exe embedded into the attachment Sscanner15081208190.zip . This executable has a detection rate of just 5/54.
The Hybrid Analysis report shows the malware POSTing to:
smboy.su/mu/tasks.php
.SU (Soviet Union) domains are almost always bad news. If you can block them on your web filter then I recommend that you do so. This particular site is hosted on 95.172.146.73 (RTComm-Sibir, Russia). The network range of 95.172.146.0/23 does seem to contain some legitimate Russian-language sites, but you might want to block the whole range to be on the safe side.
The payload is unknown, but typically malware like this will drop either the Dyre banking trojan or some sort of ransomware.
Friday 21 August 2015
What the hell is event.swupdateservice.net?
So.. I saw some mysterious outbound traffic to event.swupdateservice.net/event (138.91.189.124 / Microsoft, US). Googling around for the domain came up with some references to malware, but nothing very conclusive.
The WHOIS details for the domain are anonymised (never a good sign), and the IP address is also used by event.ezwebservices.net which uses similarly hidden details. Team Cymru have an analysis of what is being phoned home to this mystery server, and I found an existing Malwr analysis referencing the alternate domain.
I eventually found the mystery executable in C:\Users\[username]\AppData\Local\SoftUpdate\SoftUpdate.exe on the afflicted machine. Various analysis tools confirm that it generates this traffic [1] [2] [3].
The binary itself does not identify its creator. I found various references (such as in this report) linking this software and the domains to Emaze.com (a "free" presentation tool) and a look at the users traffic logs indicates that they visited this site, referred to it by VisualBee.com which is some sort of https://www.hybrid-analysis.com/sample/f479a3779efb6591c96355a55e910f6a20586f3101cd923128c764810604092f?environmentId=1PowerPoint plugin.
Neither domain identifies itself through the WHOIS details, not can I find any contact details on either site. A look through the historical WHOIS for VisualBee.com gives:
Administrative Contact:
info, info info@visualbee.com
visual software systems LTD.
6 Hanechoshet st.
Tel-Aviv, Israel 69710
Israel
+972.775422537
And for Emaze.com:
Administrative Contact:
Rubenstein, Steven rubenstein.steven@gmail.com
504 224th PL SE
Bothell, Washington 98021
United States
+1.4254862149
This Crunchbase profile for Shai Schwartz links the two companies.
I don't like sharing data with commercial operations who are not prepared to fully reveal their identity, and I personally recommend blocking traffic to:
visualbee.com
emaze.com
swupdateservice.net
ezwebservices.net
The WHOIS details for the domain are anonymised (never a good sign), and the IP address is also used by event.ezwebservices.net which uses similarly hidden details. Team Cymru have an analysis of what is being phoned home to this mystery server, and I found an existing Malwr analysis referencing the alternate domain.
I eventually found the mystery executable in C:\Users\[username]\AppData\Local\SoftUpdate\SoftUpdate.exe on the afflicted machine. Various analysis tools confirm that it generates this traffic [1] [2] [3].
The binary itself does not identify its creator. I found various references (such as in this report) linking this software and the domains to Emaze.com (a "free" presentation tool) and a look at the users traffic logs indicates that they visited this site, referred to it by VisualBee.com which is some sort of https://www.hybrid-analysis.com/sample/f479a3779efb6591c96355a55e910f6a20586f3101cd923128c764810604092f?environmentId=1PowerPoint plugin.
Neither domain identifies itself through the WHOIS details, not can I find any contact details on either site. A look through the historical WHOIS for VisualBee.com gives:
Administrative Contact:
info, info info@visualbee.com
visual software systems LTD.
6 Hanechoshet st.
Tel-Aviv, Israel 69710
Israel
+972.775422537
And for Emaze.com:
Administrative Contact:
Rubenstein, Steven rubenstein.steven@gmail.com
504 224th PL SE
Bothell, Washington 98021
United States
+1.4254862149
This Crunchbase profile for Shai Schwartz links the two companies.
I don't like sharing data with commercial operations who are not prepared to fully reveal their identity, and I personally recommend blocking traffic to:
visualbee.com
emaze.com
swupdateservice.net
ezwebservices.net
Thursday 20 August 2015
Malware spam: "Email from Transport for London" / "noresponse@cclondon.com"
This fake TfL spam comes with a malicious attachment:
93.185.4.90:12326/2008uk77/jI7tL6q34q/0/61-SP1/0/FDMBEFJBMKBEMM
93.185.4.90:12326/2008uk77/jI7tL6q34q/41/5/42/FDMBEFJBMKBEMM
These GET requests are a characteristic of Upatre/Dyre. 93.185.4.90 is allocated to C2NET, Czech Republic and I strongly recommend that you block it.
Those Hybrid Analysis reports also identify some botnet IPs and dropped files, which I suggest that you study if interested.
From "Transport for London" [noresponse@cclondon.com]The attachment name seems to vary, in the samples I have seen there is 7887775.zip, 0174458.zip and rather oddly [?var=partorderb].zip. From these I have recovered two malicious samples with a VirusTotal detection rate of 6/56 and 1/57. These two Hybrid Analysis reports [1] [2] show the malware connecting to various malicious and non-malicious IPs, but in particular we see a traffic pattern like this:
Date Thu, 20 Aug 2015 17:04:26 +0530
Subject Email from Transport for London
Dear Customer
Please open the attached file(7887775.zip) to view correspondence from Transport
for London.
If the attachment is in PDF format you may need Adobe Acrobat Reader to read or download
this attachment. If you require Adobe Acrobat Reader this is available at no cost
from the Adobe Website www.adobe.com
Thank you for contacting Transport for London.
Business Operations
Customer Service Representative
______________________________________________________________________
This email has been scanned by the Symantec Email Security.cloud service.
This email and any attachment are intended solely for the addressee, are strictly
confidential and may be legally privileged. If you are not the intended recipient
any reading, dissemination, copying or any other use or reliance is prohibited. If
you have received this email in error please notify the sender immediately by email
and then permanently delete the email.
93.185.4.90:12326/2008uk77/jI7tL6q34q/0/61-SP1/0/FDMBEFJBMKBEMM
93.185.4.90:12326/2008uk77/jI7tL6q34q/41/5/42/FDMBEFJBMKBEMM
These GET requests are a characteristic of Upatre/Dyre. 93.185.4.90 is allocated to C2NET, Czech Republic and I strongly recommend that you block it.
Those Hybrid Analysis reports also identify some botnet IPs and dropped files, which I suggest that you study if interested.
Labels:
Czech Republic,
Dyre,
EXE-in-ZIP,
Malware,
Spam,
Upatre,
Viruses
Search the Ashley Madison hacked leaked database (enter name or email)
Search the Ashley Madison hacked leaked database (enter name or
email)
Nothing found
The profile_relationship column specifies the relationship status.
const ATTACHED_FEMALE_SEEKING_MALE = 1;
const ATTACHED_MALE_SEEKING_FEMALE = 2;
const SINGLE_MALE_SEEKING_FEMALE = 3;
const SINGLE_FEMALE_SEEKING_MALE = 4;
const MALE_SEEKING_MALE = 5;
const FEMALE_SEEKING_FEMALE = 6;
So, if it's a "2", it's a cheating man. The pref_opento items, which is a list of sexual fantasies users are open to:
1: "Threesome"
3: "Being Dominant/Master"
4: "Being Submissive/Slave"
6: "Bondage"
7: "Conventional Sex"
11: "Fetishes"
14: "Nothing Kinky"
15: "One-Night Stands"
17: "Role Playing"
18: "Sex Talk"
19: "Spanking"
21: "Experimenting with Tantric Sex"
22: "Transvestitism"
23: "Experimenting with Sex Toys"
23: "Exploring with Sex Toys"
26: "Aggressiveness"
27: "Blindfolding"
28: "Bubble Bath for 2"
29: "Cuddling & Hugging"
30: "Curious - Domination"
31: "Curious - Submission"
32: "Dressing Up/Lingerie"
33: "Erotic Movies"
34: "Erotic Tickling"
36: "Extended Foreplay/Teasing"
37: "Gentleness"
38: "Good With Your Hands"
39: "Kissing"
40: "Light Kinky Fun"
41: "Likes to be Watched/Exhibitionism"
42: "Likes to Give Oral Sex"
43: "Likes to Receive Oral Sex"
44: "Likes to Go Slow"
45: "Lots of Stamina"
46: "Open to Experimentation"
48: "Sensual Massage"
49: "Sharing Fantasies"
50: "Someone I Can Teach"
51: "Someone Who Can Teach Me"
52: "You Like to Cross Dress"
They also have a "looking for" section. Those numbers are:
1: "A Don Juan"
4: "Sense of Humor"
6: "Aggressive/Take Charge Nature"
9: "Average Sex Drive"
10: "Confidence"
11: "Discretion/Secrecy"
12: "Dislikes Routine"
14: "Good Personal Hygiene"
16: "Has a Secret Love Nest"
17: "High Sex Drive"
18: "Imagination"
19: "Likes Routine"
30: "A Professional/Well Groomed"
31: "Stylish/Classy"
32: "Casual Jeans/T-shirt Type"
33: "Tattoos"
34: "Body Piercing"
35: "BBW"
36: "Full Size Body"
37: "Muscular/Fit Body"
38: "Petite Figure"
39: "Slim to Average Body"
40: "Tall Height"
41: "Short Height"
42: "Long Hair"
43: "Short Hair"
44: "Girl Next Door"
45: "Naughty Girl"
46: "Bad Boy"
47: "Boy Next Door"
48: "Creative and Adventurous"
49: "Relaxed and Easy Going"
50: "Hopeless Romantic"
51: "A Father Figure"
52: "Not Possessive"
53: "A Good Listener"
54: "Good Communicator"
55: "Disease Free"
56: "Drug Free"
57: "Casual/Social Drinker"
58: "Seeking a Sugar Baby"
59: "Seeking a Sugar Daddy"
60: "Natural Breasts"
61: "Facial Hair"
62: "Tall, Dark and Handsome"
Nothing found
The profile_relationship column specifies the relationship status.
const ATTACHED_FEMALE_SEEKING_MALE = 1;
const ATTACHED_MALE_SEEKING_FEMALE = 2;
const SINGLE_MALE_SEEKING_FEMALE = 3;
const SINGLE_FEMALE_SEEKING_MALE = 4;
const MALE_SEEKING_MALE = 5;
const FEMALE_SEEKING_FEMALE = 6;
So, if it's a "2", it's a cheating man. The pref_opento items, which is a list of sexual fantasies users are open to:
1: "Threesome"
3: "Being Dominant/Master"
4: "Being Submissive/Slave"
6: "Bondage"
7: "Conventional Sex"
11: "Fetishes"
14: "Nothing Kinky"
15: "One-Night Stands"
17: "Role Playing"
18: "Sex Talk"
19: "Spanking"
21: "Experimenting with Tantric Sex"
22: "Transvestitism"
23: "Experimenting with Sex Toys"
23: "Exploring with Sex Toys"
26: "Aggressiveness"
27: "Blindfolding"
28: "Bubble Bath for 2"
29: "Cuddling & Hugging"
30: "Curious - Domination"
31: "Curious - Submission"
32: "Dressing Up/Lingerie"
33: "Erotic Movies"
34: "Erotic Tickling"
36: "Extended Foreplay/Teasing"
37: "Gentleness"
38: "Good With Your Hands"
39: "Kissing"
40: "Light Kinky Fun"
41: "Likes to be Watched/Exhibitionism"
42: "Likes to Give Oral Sex"
43: "Likes to Receive Oral Sex"
44: "Likes to Go Slow"
45: "Lots of Stamina"
46: "Open to Experimentation"
48: "Sensual Massage"
49: "Sharing Fantasies"
50: "Someone I Can Teach"
51: "Someone Who Can Teach Me"
52: "You Like to Cross Dress"
They also have a "looking for" section. Those numbers are:
1: "A Don Juan"
4: "Sense of Humor"
6: "Aggressive/Take Charge Nature"
9: "Average Sex Drive"
10: "Confidence"
11: "Discretion/Secrecy"
12: "Dislikes Routine"
14: "Good Personal Hygiene"
16: "Has a Secret Love Nest"
17: "High Sex Drive"
18: "Imagination"
19: "Likes Routine"
30: "A Professional/Well Groomed"
31: "Stylish/Classy"
32: "Casual Jeans/T-shirt Type"
33: "Tattoos"
34: "Body Piercing"
35: "BBW"
36: "Full Size Body"
37: "Muscular/Fit Body"
38: "Petite Figure"
39: "Slim to Average Body"
40: "Tall Height"
41: "Short Height"
42: "Long Hair"
43: "Short Hair"
44: "Girl Next Door"
45: "Naughty Girl"
46: "Bad Boy"
47: "Boy Next Door"
48: "Creative and Adventurous"
49: "Relaxed and Easy Going"
50: "Hopeless Romantic"
51: "A Father Figure"
52: "Not Possessive"
53: "A Good Listener"
54: "Good Communicator"
55: "Disease Free"
56: "Drug Free"
57: "Casual/Social Drinker"
58: "Seeking a Sugar Baby"
59: "Seeking a Sugar Daddy"
60: "Natural Breasts"
61: "Facial Hair"
62: "Tall, Dark and Handsome"
Labels:
Hacked sites,
Humour
Wednesday 19 August 2015
Malware spam: "SHIPMENT NOTICE" / "serviceuk@safilo.com"
This fake financial spam does not come from Safilo UK Ltd but is instead a simple forgery with a malicious attachment:
megapolisss006.su/go/gate.php
.SU (Soviet Union) domains are bad news in general, if you can I would recommend blocking traffic to all of them. This domain is hosted on the following IPs:
195.2.88.196 (Zenon N.S.P., Russia)
94.229.22.39 (Bashrtcomm LIR, Russia)
94.229.22.42 (Bashrtcomm LIR, Russia)
You might want to consider blocking:
195.2.88.0/24
94.229.16.0/21
This though is the recommended minimum blocklist:
195.2.88.196
94.229.22.39
94.229.22.42
I am not entirely certain of the payload as the download locations seem to be unreliable.
From serviceuk@safilo.comAttached is a file ship20150817.zip which in turn contains a malicious executable ship20150817.exe which has a detection rate of 4/56. According to these automated analysis tools [1] [2] the malware attempts to phone home to:
Date Wed, 19 Aug 2015 17:47:46 +0700
Subject SHIPMENT NOTICE
Dear Customer,
please be informed that on Aug 19, 2015 we sent you the following items:
1 pieces from order 1I5005729
1 pieces from order 1I5005841
IMPORTANT
To find out all details concerning your orders and shipments open the file here attached
or go to the Order status page of the site.
Safilo UK Ltd.
serviceuk@safilo.com
-------
megapolisss006.su/go/gate.php
.SU (Soviet Union) domains are bad news in general, if you can I would recommend blocking traffic to all of them. This domain is hosted on the following IPs:
195.2.88.196 (Zenon N.S.P., Russia)
94.229.22.39 (Bashrtcomm LIR, Russia)
94.229.22.42 (Bashrtcomm LIR, Russia)
You might want to consider blocking:
195.2.88.0/24
94.229.16.0/21
This though is the recommended minimum blocklist:
195.2.88.196
94.229.22.39
94.229.22.42
I am not entirely certain of the payload as the download locations seem to be unreliable.
Monday 10 August 2015
Malware spam: "Gabriel Daniel" / "Resume" / "Gabriel_Daniel_resume.doc"
This fake résumé comes with a malicious attachment:
As far as I can tell, it appears to download a disguised JPG file from 46.30.43.179/1.jpg (Eurobyte LLC, Russia) which appears to be an encrypted executable. I wasn't able to decode all of the macro, however this Hybrid Analysis report shows clearly what is going on..
So, it is pretty clear that the payload here is Cryptowall (which encrypts all the victim's files). The same Hybrid Analysis report shows that it POSTS information to:
conopizzauruguay.com/wp-content/wp-content/themes/twentythirteen/cccc.php?v=c91jzn46yr
conopizzauruguay.com/wp-content/wp-content/themes/twentythirteen/cccc.php?b=86v97tziud5m
conopizzauruguay.com/wp-content/wp-content/themes/twentythirteen/cccc.php?o=ups5xom3u2sb01
It also directs the visitor to various personalised ransom pages hosted on 80.78.251.170 (Agava, Russia).
Recommended blocklist:
46.30.43.179
80.78.251.170
conopizzauruguay.com
MD5:
e34cf893098bd17ae9ef18b04cff58aa
From: alvertakarpinskykcc@yahoo.comInterestingly, the email does really appear to come via Yahoo!'s mail servers. Attached is a document Gabriel_Daniel_resume.doc which contains this malicious macro [pastebin] which has a VirusTotal detection rate of 2/56.
Date: 10 August 2015 at 19:40
Subject: Resume
Signed by: yahoo.com
Hi my name is Gabriel Daniel doc is my resume
I would appreciate your immediate attention to this matter
Kind regards
Gabriel Daniel
As far as I can tell, it appears to download a disguised JPG file from 46.30.43.179/1.jpg (Eurobyte LLC, Russia) which appears to be an encrypted executable. I wasn't able to decode all of the macro, however this Hybrid Analysis report shows clearly what is going on..
So, it is pretty clear that the payload here is Cryptowall (which encrypts all the victim's files). The same Hybrid Analysis report shows that it POSTS information to:
conopizzauruguay.com/wp-content/wp-content/themes/twentythirteen/cccc.php?v=c91jzn46yr
conopizzauruguay.com/wp-content/wp-content/themes/twentythirteen/cccc.php?b=86v97tziud5m
conopizzauruguay.com/wp-content/wp-content/themes/twentythirteen/cccc.php?o=ups5xom3u2sb01
It also directs the visitor to various personalised ransom pages hosted on 80.78.251.170 (Agava, Russia).
Recommended blocklist:
46.30.43.179
80.78.251.170
conopizzauruguay.com
MD5:
e34cf893098bd17ae9ef18b04cff58aa
Malware spam: "Premium Charging MI Package for Merchant 17143013" / "GEMS@worldpay.com"
This fake financial email does not come from Worldpay but is instead a simple forgery with a malicious attachment:
So far I have seen only one sample with named 17143013 01.docm. Despite having a detection rate of 5/55 at VirusTotal, the document is malformed and is Base 64 encoded. When manually decoded it still has a detection rate of 5/55 and it contains this malicious macro [pastebin] which then downloads a component from:
gardinfo.net/435rg4/3245rd2.exe
This is exactly the same payload as seen in this spam run also from this morning.
From: GEMS@worldpay.com
Date: 10 August 2015 at 10:17
Subject: Premium Charging MI Package for Merchant 17143013
*** Please do not reply to this Message *** Attached is the Management Information to support your Monthly Invoice. Should you have any queries, please refer to your usual helpdesk number.
So far I have seen only one sample with named 17143013 01.docm. Despite having a detection rate of 5/55 at VirusTotal, the document is malformed and is Base 64 encoded. When manually decoded it still has a detection rate of 5/55 and it contains this malicious macro [pastebin] which then downloads a component from:
gardinfo.net/435rg4/3245rd2.exe
This is exactly the same payload as seen in this spam run also from this morning.
Malware spam: "Your order 10232 from Create Blinds Online: Paid" / "orders@createblindsonline.co.uk"
This fake invoice does not come from Create Blinds Online but is instead a simple forgery with a malicious attachment.
Attached is a file invoice-10232.doc which comes in at least two different variants [1] [2] containing a macro that looks like this [pastebin]. This attempts to download a malicious binary from one of the following locations:
mbmomti.com.br/435rg4/3245rd2.exe
j-choi.asia/435rg4/3245rd2.exe
The VirusTotal detection rate for this is 3/55. The Malwr report and Hybrid Analysis reports show that it generates traffic to 78.47.119.85 (Hetzner, Germany). The payload is almost definitely the Dridex banking trojan.
MD5s:
0864bc6951795b86d435176c3320a8bc
e3f30c2195c565e88a8534b15c7b942e
ba4ec70aa2179be4387a4aef10a8cd4f
From: orders@createblindsonline.co.uk
Reply-To: orders@createblindsonline.co.uk
Date: 10 August 2015 at 07:59
Subject: Your order 10232 from Create Blinds Online: Paid
We would like to thank you for your recent order.
Order Status updated on: 10/08/2015
Your Customer ID: 1761
Your Order ID: 10232
Invoice Number: 10232
Delivery Note:
We received your order and payment on Aug/102015
Your order details are attached:
Kind regards
Create Blinds Online Team
This electronic message contains information from Create Blinds Online which may be privileged or confidential. The information is intended to be for the use of the individual(s) or entity named above. If you are not the intended recipient be aware that any disclosure, copying, distribution or use of the contents of this information is prohibited. If you have received this electronic message in error, please notify us by telephone or email (to the numbers or address above) immediately.
Attached is a file invoice-10232.doc which comes in at least two different variants [1] [2] containing a macro that looks like this [pastebin]. This attempts to download a malicious binary from one of the following locations:
mbmomti.com.br/435rg4/3245rd2.exe
j-choi.asia/435rg4/3245rd2.exe
The VirusTotal detection rate for this is 3/55. The Malwr report and Hybrid Analysis reports show that it generates traffic to 78.47.119.85 (Hetzner, Germany). The payload is almost definitely the Dridex banking trojan.
MD5s:
0864bc6951795b86d435176c3320a8bc
e3f30c2195c565e88a8534b15c7b942e
ba4ec70aa2179be4387a4aef10a8cd4f
Friday 7 August 2015
Malware spam: "Sleek Granite Computer" / "saepe 422-091-2468.zip" / "nulla.exe"
What the heck is a Sleek Granite Computer? As clickbait it is kind of weird.. but perhaps interesting enough to get people to click on the malicious attachment is comes with.
This has a VirusTotal detection rate of 4/55 with Sophos identifying it as a variant of Upatre. The Hybrid Analysis report shows a typical Upatre / Dyre traffic pattern to:
195.154.241.208:12800/0608us12/6FsvE66Gy1/0/61-SP1/0/FDMBEFJBMKBEMM
195.154.241.208:12800/0608us12/6FsvE66Gy1/41/2/18/FDMBEFJBMKBEMM
This IP address belongs to Online SAS in France who seem to have hosted quite a bit of this stuff recently, the hostname identifies it as belonging to poneytelecom.eu. Traffic is also spotted to:
37.57.144.177 (Triolan / Content Delivery Network, Ukraine)
95.143.141.50 (LTnet, Czech Republic)
There is also non-malicious traffic to icanhazip.com to identify the IP address of the infected machine. This is worth monitoring though as it is a potential indicator of compromise. The payload is almost definitely the Dyre banking trojan.
Recommended blocklist:
195.154.241.208
37.57.144.177
95.143.141.50
MD5:
9520d04a140c7ca00e3c4e75dd9ccd9f
From: mafecoandohob [mafecoandohob@bawhhorur.com]The only sample of this I had was malformed and the attachment wasn't attached properly. However, if properly formatted it would have been named saepe 422-091-2468.zip and it contains a malicious executable named nulla.exe.
To: Karley Pollich
Date: 7 August 2015 at 13:17
Subject: Sleek Granite Computer
Good day!
If you remember earlier this week we discussed with You our new project which we intend to start next month.
For Your kind review we enclose here the business plan and all the related documents.
Please send us an e-mail in case You have any comments or proposed changes.
According to our calculations the project will start bringing profit in 6 months.
Thanks in advance.
Karley Pollich
Dynamic Response Strategist
Pagac and Sons
Toys, Games & Jewelery
422-091-2468
This has a VirusTotal detection rate of 4/55 with Sophos identifying it as a variant of Upatre. The Hybrid Analysis report shows a typical Upatre / Dyre traffic pattern to:
195.154.241.208:12800/0608us12/6FsvE66Gy1/0/61-SP1/0/FDMBEFJBMKBEMM
195.154.241.208:12800/0608us12/6FsvE66Gy1/41/2/18/FDMBEFJBMKBEMM
This IP address belongs to Online SAS in France who seem to have hosted quite a bit of this stuff recently, the hostname identifies it as belonging to poneytelecom.eu. Traffic is also spotted to:
37.57.144.177 (Triolan / Content Delivery Network, Ukraine)
95.143.141.50 (LTnet, Czech Republic)
There is also non-malicious traffic to icanhazip.com to identify the IP address of the infected machine. This is worth monitoring though as it is a potential indicator of compromise. The payload is almost definitely the Dyre banking trojan.
Recommended blocklist:
195.154.241.208
37.57.144.177
95.143.141.50
MD5:
9520d04a140c7ca00e3c4e75dd9ccd9f
Labels:
Czech Republic,
Dyre,
EXE-in-ZIP,
France,
Malware,
Spam,
Ukraine,
Upatre,
Viruses
Thursday 6 August 2015
Malware spam: "Voice message from 07773403290" / ""tel: 07773403290" [non-mail-user@voiplicity.co.uk]"
This fake voicemail spam comes with a malicious attachment:
wedspa.su/go/gate.php
This is hosted on a RU-Center IP address of 185.26.113.229 in Russia. Furthmore, a malicious executable is downloaded from the following locations:
globalconspiracy.hj.cx/1.exe
mastiksoul.org/1.exe
In turn, this has a detection rate of 2/55 and automated analysis of this [1] [2] show that it phones home to 212.47.196.149 (Web Hosting Solutions, Estonia).
The payload is unclear at this point, but you can guarantee that it will be nothing good.
Recommended blocklist:
185.26.113.229
212.47.196.149
MD5s:
da575b916f419b9e8bfea12168fa9902
f3ede4ebcd4b6debf15646a3d1a8bbd1
From "tel: 07773403290" [non-mail-user@voiplicity.co.uk]I was not able to determine if there was any body text from my sample collector, however each sample had an identical attachment message_01983527496.wav.zip which contains a malicious executable message_01983527496.exe. This has a VirusTotal detection rate of 5/55 and automated analysis tools [1] [2] show it POSTing to:
Date Thu, 06 Aug 2015 11:54:43 +0300
Subject RE: Voice message from 07773403290
wedspa.su/go/gate.php
This is hosted on a RU-Center IP address of 185.26.113.229 in Russia. Furthmore, a malicious executable is downloaded from the following locations:
globalconspiracy.hj.cx/1.exe
mastiksoul.org/1.exe
In turn, this has a detection rate of 2/55 and automated analysis of this [1] [2] show that it phones home to 212.47.196.149 (Web Hosting Solutions, Estonia).
The payload is unclear at this point, but you can guarantee that it will be nothing good.
Recommended blocklist:
185.26.113.229
212.47.196.149
MD5s:
da575b916f419b9e8bfea12168fa9902
f3ede4ebcd4b6debf15646a3d1a8bbd1
Labels:
EXE-in-ZIP,
Malware,
Spam,
Viruses,
Voice Mail
Subscribe to:
Posts (Atom)